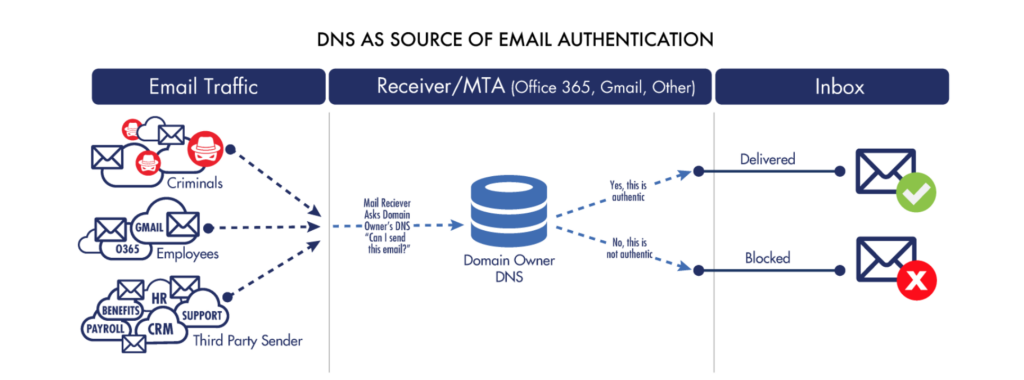
The domain name system (DNS) is the largest globally distributed database in the world. It permeates the entire world and is available everywhere you have internet access.
In other words, DNS is the perfect choice for email authentication from a usage and performance point of view. No matter where in the world a receiving mail server may be located, it will have access to DNS, from which it can retrieve the information it needs to validate the sender of an incoming message.
DNS is not just globally available, it’s also got low latency and high reliability. Mail gateways that process thousands or even millions of incoming messages per minute can issue DNS queries for every one of those messages as needed to validate their senders.
Due to the hierarchical nature of DNS, only domain owners are able to update information in their zone files. In other words, all of a domain’s records — from the A record to the TXT records used for SPF, DKIM, and DMARC — are definitively under the control of whoever owns that domain. The result: For any given domain, you can trust what DNS tells you.
Authentication Challenges with DNS
Unfortunately, from a management point of view, DNS is static, hard to work with, and finicky. DNS isn’t optimized for today’s email authentication standards, especially in our modern cloud era.
In fact, about 80% of companies trying to implement email authentication fail to get to enforcement (the point at which they’re actually protected from impersonation). A major contributing factor is the difficulty of working with DNS and the TXT records required for email authentication.
Reasons DNS Email Authentication Can Be Tricky
There are a host of reasons this is so tedious:
- Fragile Text Fields: Text fields are extremely fragile and require the precise typing of characters. Any extra spaces or just one wrong character can create serious misconfigurations.
- No Validation: There is no method to validate any changes, because DNS doesn’t offer error handling.
- Lack of Testing: There’s no way to test or stage changes. Updates are essentially made in a live, worldwide production system: the global DNS.
- Never-Ending Process: Every addition or revocation of a SaaS app to your email authentication records requires yet more DNS changes, resulting in continuous DNS work and the constant attention of scarce infrastructure resources.
- Lack of Centralized Visibility: Organizations often struggle to maintain a holistic view of their DNS configurations, leading to inconsistencies and vulnerabilities in their email authentication setup.
- Delayed Propagation: Changes to DNS records can have delayed propagation times across the global internet. This latency can result in significant downtime or periods during which email authentication is not functioning as intended, exposing organizations to risk.
- Complexity in Policy Enforcement: Crafting and enforcing DMARC policies that accurately reflect an organization’s email authentication strategy requires technical expertise. The complexity increases with the organization’s size and the volume of legitimate email senders (like marketing platforms and third-party vendors).
- Insufficient Feedback Mechanisms: Although DMARC includes mechanisms for reporting and feedback, interpreting these reports can be overwhelming due to their technical nature and the sheer volume of data. Organizations often lack the tools or expertise to effectively analyze this information to improve their email security posture.
How Most Companies Navigate These Challenges
Recognizing this brittleness, most enterprises have built cumbersome change management procedures around DNS updates. This doesn’t work when (in the case of email authentication) you need to update configurations frequently to keep pace with provider changes.
Some of Valimail’s ISP partners have told us that the top reason they see email failing authentication through DKIM is that the TXT records hosting the DKIM keys are broken. That’s a clear indication of the widespread difficulty IT people have with managing email authentication in DNS. It’s just too easy to make a fatal error.
In short, the less you mess around with DNS records, the happier you’ll be.
Solve Your DNS Authentication Issues with Valimail
Valimail solves these issues by giving you a user-friendly application that allows you to manage your senders without needing direct access to DNS. Valimail ensures that all changes are correct and accurate removing the riskiness of ongoing DNS updates. For more information, please check out our data sheet, A Next-Generation Approach to Email Authentication.
