Google has rolled out a helpful update to its DMARC aggregate reports: new diagnostic details about why an email fails sender authentication requirements. This approach helps senders of all sizes understand how they’re doing with respect to Google’s sender requirements in one place (their DMARC report) instead of needing to evaluate compliance from service to service and SMTP log to SMTP log.
This is a big step forward for transparency and troubleshooting, and we at Valimail are already incorporating it into our reporting pipeline.
From industry discussion to real-world insight
This change didn’t come out of nowhere. It started as a conversation at an industry event: our CTO’s idea to make sender requirement failure reasons more visible to brands across their entire sending infrastructure, by leveraging DMARC aggregate reports.
Now, it’s live, giving organizations clearer visibility into authentication problems that were previously hard to pinpoint. This level of specific detail around various types of email authentication or sender compliance failures was never previously available in DMARC reporting, having been available only in the direct NDRs (non-delivery reports) and SMTP rejections returned to senders when message delivery fails or is deferred.
Google’s DMARC XML feedback includes additional information under the <policy_evaluated> section, particularly in the <reason> tag, now offering a newly-populated “comment” field that looks like this:
<policy_evaluated>
<disposition>none</disposition>
<dkim>fail</dkim>
<spf>fail</spf>
<reason>
<type>local_policy</type>
<comment>Sender requirement failed: 550-5.7.1</comment>
</reason>
</policy_evaluated>The phrase Sender requirement failed: is a fixed string, but the trailing SMTP error code offers specific clues into what went wrong.
Decoding the new error signals
We’re now observing these error codes in the wild. Here’s a breakdown with quick definitions of the most common codes seen:
- 421-4.7.27: Rate limiting due to SPF failure.
- 421-4.7.29: Rate limiting due to lack of TLS.
- 421-4.7.30: Rate limiting because DKIM authentication didn’t pass.
- 421-4.7.32: Rate limiting due to lack of alignment.
- 550-5.7.25: Blocked due to lack of PTR record or forward/reverse DNS mismatch.
- 550-5.7.27: Blocked due to SPF failure.
- 550-5.7.30: Blocked because it didn’t pass DKIM authentication.
- 550-5.7.1: Blocked for other reasons (like spam, reputation, RFC5322 non-compliance).
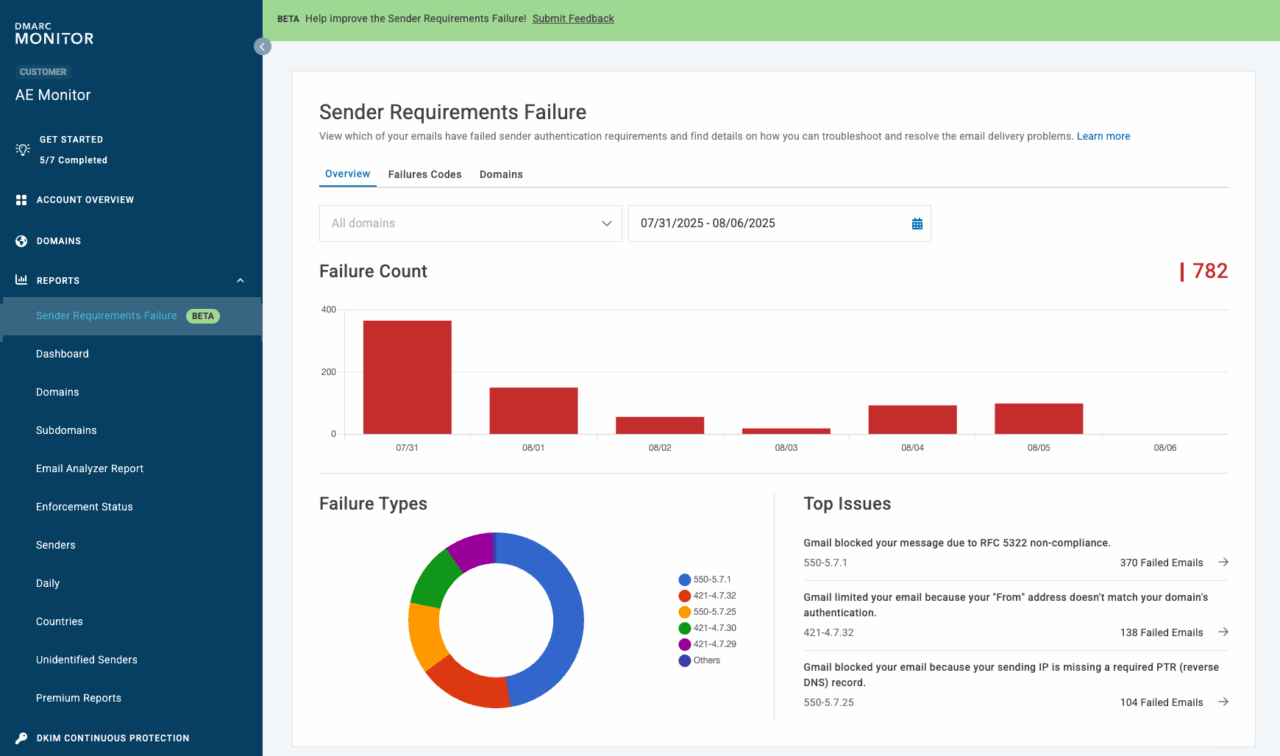
This new diagnostic detail (utilizing existing SMTP rejection and deferral codes defined here) allows email administrators and domain owners to quickly identify whether they’re failing SPF, DKIM, alignment, or running into deeper deliverability issues such as missing DNS records or RFC header non-compliance.
Use Valimail to break down these reports and errors
We are excited about this improvement because it aligns directly with our mission to bring clarity to email authentication. Valimail is already capturing this new error information in our backend systems and moving quickly to integrate it into our customer-facing dashboards and alerts.
All Valimail users are now able to access the new Sender Requirements Failure Report. This report helps organizations quickly pinpoint authentication gaps, infrastructure misconfigurations, and compliance issues that could be undermining deliverability. (Find more detail on the report here.)
Valimail remains committed to ensuring you have every possible resource to keep your sending domains aligned, authenticated, and trusted — now with even more information on your entire sending landscape, thanks to Google.
And if you are struggling to comply with Google’s email sender guidelines, reach out today to get a demo of Valimail Enforce, and we’ll be able to help you reach full sender compliance and DMARC enforcement quickly.



