“DKIM alignment failed.”
If you’ve ever dug into your email authentication reports, you’ve probably seen this frustrating message. It’s like getting a rejection letter that doesn’t explain why you didn’t get the job. Your DKIM seems to be set up correctly, you’ve got valid signatures, but something still isn’t working.
DKIM alignment failures are some of the most common (and most confusing) email authentication issues. Alignment simply means that the domain in your email’s “From:” field matches the domain that signed the message with DKIM. When these don’t match, receivers get suspicious.
Think of it like showing up at a security checkpoint with a perfectly valid ID, but the name on it doesn’t match the name on your reservation. Your ID might be real, but the mismatch raises red flags.
Well, when it comes to your email program, why should you care? Because when your DKIM isn’t aligned, your emails are more likely to be marked as spam or rejected entirely. Plus, you won’t get the full protection DMARC offers against spoofing and phishing.
Below, we’ll explain what DKIM alignment means, why your signatures might be failing alignment checks, and step-by-step fixes to get everything working again.
What is DKIM alignment?
DKIM alignment means that the domain in your email’s “From:” header (the one your recipients see) matches the domain that digitally signed the message. That’s it. Two domains need to match, and when they do, your DKIM is “aligned.”
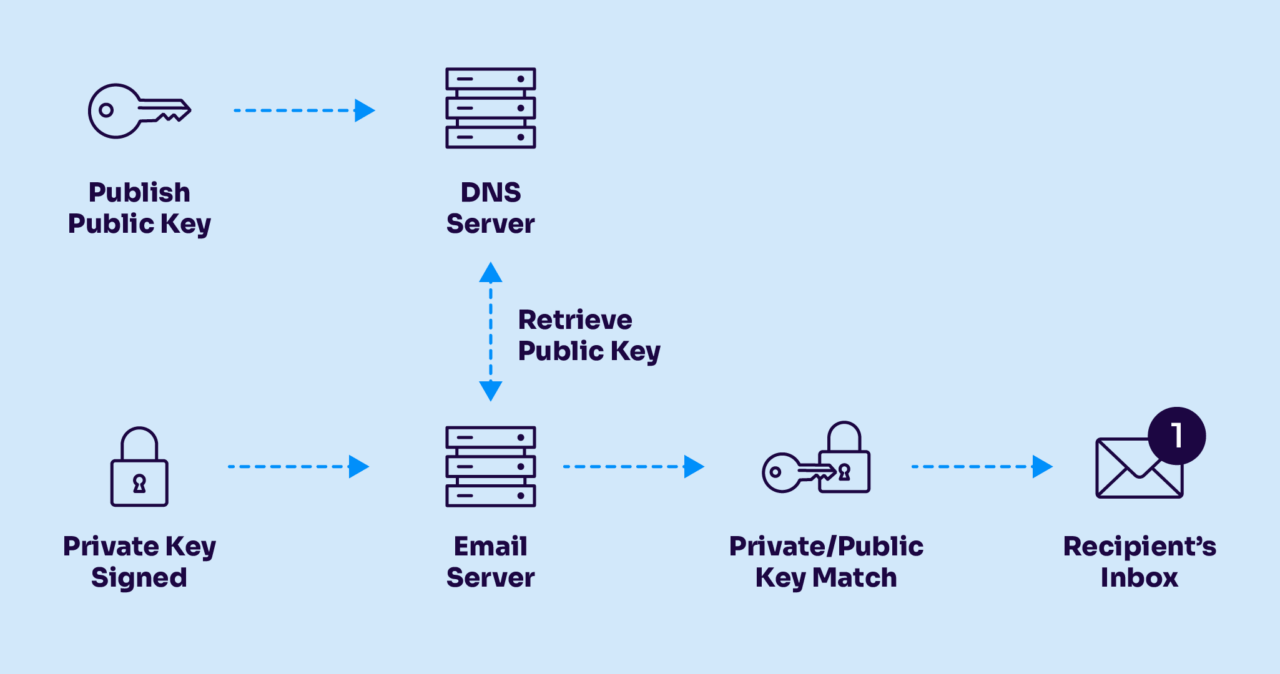
DKIM (Domain Keys Identified Mail) itself is a way for senders to digitally sign their messages, proving they actually came from their servers. It’s like a wax seal on an envelope that proves the letter inside hasn’t been tampered with and confirms who sent it.
DKIM alignment takes it further, though. It connects that digital signature to the sender that your recipients actually see in their inbox.
There are two key domains at play here:
- Header From domain: This is what everyone sees in their email client (like contact@yourbusiness.com).
- DKIM d= domain: This is the domain that created the digital signature.
When these two domains match exactly (or the DKIM domain is a valid subdomain of the Header From domain), congratulations—your DKIM is aligned! If they don’t match, that’s when you get those annoying “DKIM alignment failed” messages.
Without alignment, a legitimate digital signature doesn’t prove much. Someone could set up valid DKIM for their own domain but still spoof your company in the From field. Alignment closes this loophole by requiring that the domain you claim to be is also the domain that signed the message.
DKIM also plays a role in your DMARC authentication. SPF checks the sending server and DKIM verifies the message wasn’t tampered with. For your DMARC to pass, either your SPF or DKIM (or both) needs to be aligned.
DKIM alignment vs. DKIM verification: What’s the difference?
Many people confuse DKIM alignment with DKIM verification, but they’re actually checking two different things.
DKIM verification is about the signature itself—is it valid? Was it created with the proper private key? Has the message been tampered with since it was signed? This is the technical part that guarantees the integrity of your message.
DKIM alignment is about identity matching—does the domain that created the signature match the domain in the From field? This is the trust part that connects the technical signature to the sender identity that your recipients see.
Here’s how they differ in practice:
- DKIM verification can pass while alignment fails. You might have a perfectly valid signature from mailservice.com, but if your email appears to come from yourbusiness.com, the signature is valid but not DKIM aligned.
- Verification happens first, then alignment. If verification fails (meaning the signature is invalid), alignment isn’t even checked. A valid signature is the prerequisite for checking alignment.
- Verification is binary (pass/fail), while alignment has nuances. Alignment can be “relaxed” (allowing subdomains) or “strict” (requiring an exact match).
The anatomy of DKIM alignment failures
When DKIM alignment fails, it’s usually because of a mismatch between two specific domains. Alignment fails when these two domains don’t match or aren’t properly related. But what does a failure actually look like?
Here’s a real-world example: Imagine you send emails through a marketing platform like Mailchimp. Your emails show your domain in the From field (sales@yourbusiness.com), but the DKIM signature might contain d=servers.mailchimpsender.com. These domains clearly don’t match, so alignment fails.
Sometimes the alignment failure is more subtle. Maybe your marketing team sends from marketing.yourbusiness.com but the DKIM signature uses the parent domain yourbusiness.com. Whether this passes or fails depends on how strict your alignment requirements are set (we’ll cover that later).
In this case, the sender itself isn’t fake; the DKIM signature is just not aligned with where you’re trying to use it.
Why your DKIM signature is not aligned
So your DKIM signature is valid, but alignment is still failing. Let’s look at the most common reasons this happens:
- Third-party senders are the usual suspects
- Subdomain confusion
- Configuration mistakes
- Organizational quirks
- Email forwarding and mailing lists
| Curious where your DKIM is breaking down and how to fix it? The Valimail DKIM Continuous Protection Report highlights the most common alignment issues across thousands of domains. It’s an excellent resource for understanding the root causes behind DKIM misalignment, especially if you’re using third-party senders. Combine that insight with Valimail Monitor (free to use). You’ll get continuous visibility into how your DKIM is performing, where alignment is failing, and what steps you can take to fix it, without diving into cryptic XML files. Read more about the Valimail Continuous DKIM report |
1. Third-party senders are the usual suspects
The number one cause of DKIM alignment issues is using third-party services to send email. Marketing platforms, CRM systems, help desks, and other services often set up their DKIM in ways that don’t align with your domain.
Now, using these services isn’t a problem. You just need to know what you’re dealing with.
Many of these services sign emails with their own domain by default. So while your email shows up as from@yourbusiness.com, the DKIM signature contains their domain (a clear alignment failure).
Even when these services offer “custom DKIM” options, they might be implementing them incorrectly behind the scenes, leading to subtle alignment issues that are hard to spot.
2. Subdomain confusion
By default, DKIM uses “relaxed” alignment, which means a subdomain can be aligned with its parent domain. But this only works in one direction:
- DKIM d=marketing.yourbusiness.com can align with From: user@yourbusiness.com
- But DKIM d=yourbusiness.com does NOT align with From: user@marketing.yourbusiness.com
3. Configuration mistakes
Sometimes the problem is simply human error in your DKIM setup:
- Typos in your DNS records
- Using the wrong selector in your DKIM implementation
- Incorrect key rotation procedures
- Misconfigured mail servers that don’t properly sign outgoing messages
These technical issues can be tricky because the DKIM signature itself might validate correctly while still failing alignment.
4. Organizational quirks
Company mergers, acquisitions, and rebrandings can create alignment nightmares. You might be sending from your new domain name, but your email infrastructure still uses DKIM keys from your old domain. Or different branches of your company might have independently set up email authentication without coordination.
Some organizations also have challenges with email systems that weren’t designed with DKIM alignment in mind, like legacy on-premises email servers or custom applications that generate emails.
5. Email forwarding and mailing lists
When emails get forwarded or sent through mailing lists, they often lose their original DKIM signature, or the signature becomes invalid due to modifications. This isn’t strictly an alignment issue on your end, but it can affect how your messages are authenticated when they’re forwarded.
How to check if your DKIM is aligned
Here are a few ways to check your DKIM alignment:
DMARC reports
The most comprehensive way to check DKIM alignment is through DMARC reports. When you set up DMARC (even with p=none), receiving servers will send you regular XML reports showing authentication results for all emails from your domain.
When the DKIM domain differs from your header_from domain, you’ve found an alignment issue. The challenge with DMARC reports is that they’re not exactly light reading—they’re XML files designed for machines, not humans.
You can also use Valimail Monitor (it’s free) if you want to ditch the XML reports and get clearer insights.
Email headers
For a more immediate check, you can examine the headers of emails you send. Send a test email to yourself and check the full headers (most email clients have an option to view these).
Look for the “Authentication-Results” header, which shows both verification and alignment results:
The key parts to compare are:
- The domain in header.i=@sender.com (from the DKIM signature)
- The domain in header.from=yourdomain.com (from the DMARC check)
If these don’t match and DMARC still passes, it’s likely because your SPF is aligned even though your DKIM isn’t.
Testing tools
Several online tools can analyze email authentication for you:
- Mail Tester: Send an email to the address they provide and get a report on all authentication aspects, including DKIM alignment.
- Valimail’s Domain Checker: While this doesn’t check individual emails, it can identify potential alignment issues in your domain setup.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Your Domain
Not protected AGAINST IMPERSONATION ATTACKS
DMARC NOT AT ENFORCEMENT
exampledomain1.com
Authentication Status for January 10, 2025
DMARC at Enforcement
SPF Record Configured
BIMI Ready
exampledomain1.com
Authentication Status for January 10, 2025
DMARC at Enforcement
SPF Record Configured
BIMI Ready
Get your DKIM aligned with Valimail
Fixing DKIM alignment issues isn’t just about ticking a box for email authentication. Sure, it can feel that way sometimes, but it’s ultimately about guaranteeing your legitimate messages reach their destinations (while preventing others from impersonating your domain).
DKIM alignment can be tricky to diagnose and fix, especially when you’re using multiple email services across your organization. What seems like a minor technical mismatch can have major consequences for your email deliverability and security.
Fortunately, you don’t have to do all this XML reporting and email parsing on your own. We can help.
Start by running a quick check on your domain’s current authentication status with Valimail’s free Domain Checker tool. In less than a minute, you’ll know if your DKIM is properly aligned and if there are other authentication issues that need addressing.
For a deeper look into your email authentication (including ongoing monitoring of DKIM alignment across all your sending services), try Valimail Monitor. It transforms those confusing DMARC reports into actionable insights about exactly where your alignment is breaking down (and how to fix it).



