Business email compromise (BEC) is a type of cyber security attack aimed at extracting valuable assets from an organization via its email.
Impersonating the identity of a company employee or trusted party, a fraudster deceives the email recipient into replying with information, money, or access codes to corporate assets.
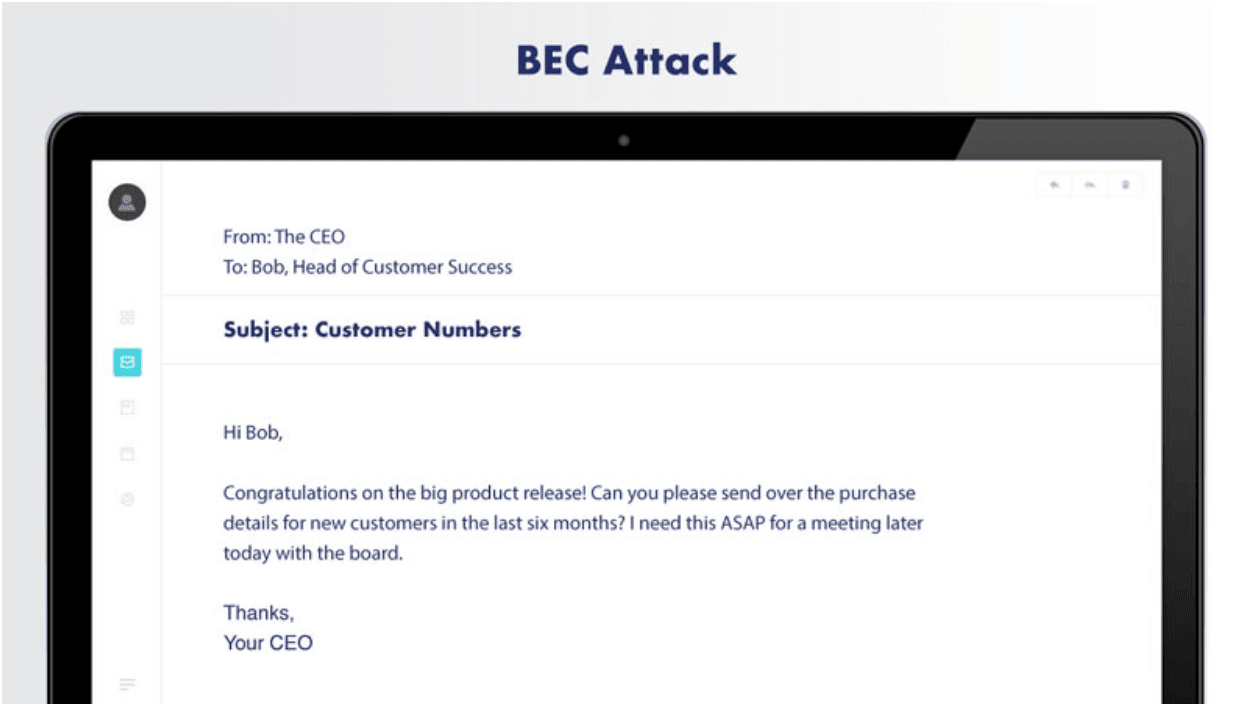
Image description: A cybercriminal posing as a company executive sends email to another employee with specific knowledge of the company.
When the criminal poses as a top officer, BEC is called a CEO fraud attack. If the attacker is attempting to get employee income information, the activity is called a W-2 attack. A BEC attack’s success is dependent on significant knowledge of the company and a few important employees. It also depends on the ease of impersonating someone the target trusts, such as an executive or trusted outside partner (like a law firm or accounting firm).
