DMARC quarantine and reject policies tell inbox providers how to handle your emails, but they have slight (yet important) differences. We’ll help you understand why they both exist.
Valimail’s mission has been consistent since the day we started back in 2015: We want to keep fraudulent emails out of the inbox.
We’ll walk you through choosing which DMARC policy is best for your domain.
What are the DMARC policies?
Domain-based Message Authentication, Reporting, and Conformance (DMARC) is a powerful tool for accomplishing a major part of that aim because it enables domain owners to eliminate spoofed messages that misuse their domains in the From field. Because DMARC is a global standard with virtually universal support among the world’s largest email providers, it eliminates them from everyone’s inboxes, not just the domain owners’.
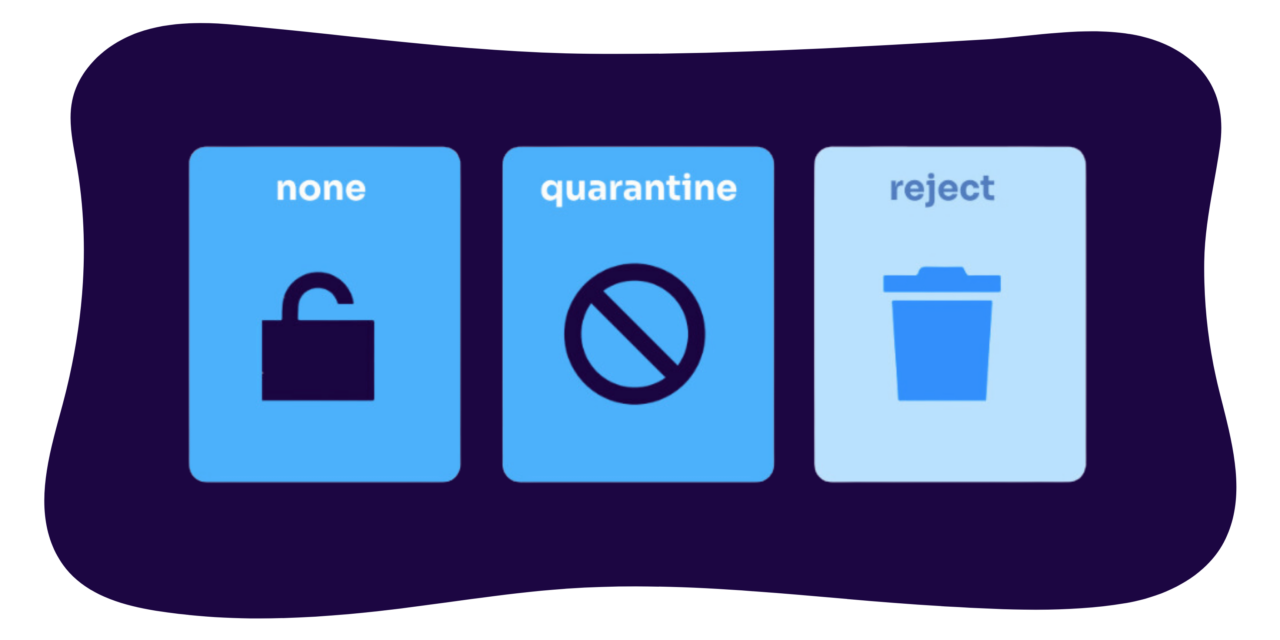
To be effective as an anti-phishing solution, domain owners need to set their DMARC records to a policy of “reject” or “quarantine” — otherwise known as DMARC enforcement. If you don’t do that, those receiving mail servers will see a policy of “none” and will continue to deliver the spoofs. These are the three primary DMARC policies:
- p=reject: Messages failing authentication should be rejected (deleted)
- p=quarantine: Messages failing authentication should be sent to spam or otherwise quarantined from the inbox
- p=none: No special handling; messages failing authentication should be delivered as normal

DMARC quarantine vs reject: Which is ideal?
he ideal state is a reject policy, and that is what we recommend to our customers. However, there are use cases where this isn’t feasible, either because the customer has mail flows they need to preserve that aren’t yet authenticatable (e.g., high corporate usage of mailing lists that have not yet been implemented Authenticated Received Chain (ARC)) or because of political considerations at the organization.
Sometimes, an organization wants to implement quarantine to convince themselves that things are working as expected before moving to reject. With the visibility that Valimail Enforce provides, quarantine is not usually necessary — but some customers still require it, and that’s why we support it when it’s needed.
The biggest danger to an organization that has just deployed a DMARC record is staying at a p=none or sp=none position for years on end.
NOTE: the sp tag lets organizations set a separate policy for subdomains of the main domain; at p=reject and sp=none, messages from ‘example.com’ that fail to authenticate will be rejected, but messages from sub.example.com will be delivered as normal. In practice, this means that your domain is still abusable: An attacker can just pick any subdomain and go to town phishing your customers or employees.
The inadequate alternative to quarantine and reject
If we were to reject the option of quarantine and instead opt for no precautions whatsoever, or a policy of none at best, we would view it as highly concerning. Regrettably, this is exactly the advice some of our competitors offer to their clients and, in some instances, even follow themselves. We strongly believe this approach is both negligent and poses a significant risk.
The vast majority of DMARC’s benefits come from keeping fraudulent messages out of the inbox, which a quarantine policy accomplishes. The material benefits are obvious to any organization that gets to and stays at quarantine: Their customers don’t see brand impersonation attacks, their partners don’t see fraudulent invoices, and their employees don’t see spear phishing attacks.
Yes, fraudulent emails can be dug out of the spam folder, but that requires a heightened level of awareness by the recipient and vastly reduced frequency.
This is especially true given that at least one major consumer and enterprise email receiver treats a reject and quarantine policy identically: Regardless if the domain’s policy is set to reject or quarantine, this receiver puts messages failing authentication in the spam folder.
In other words, for messages sent to this receiver, switching from quarantine to reject will make absolutely no difference. For all other receivers that respect DMARC policies, the switch will delete messages that were formerly confined to the spam folder.
Check your DMARC policy with our free domain checker.
How to lock the door against spoofing
To use an analogy from physical security: A quarantine policy is like a wooden door, and a reject policy is like a steel door. Yes, a steel door is more secure — but a wooden door is better than no door at all.
And maybe all you really need is a wood door.
If the vendor trying to sell you a door can’t even get the door installed properly or quickly, who cares what their opinion is on steel vs. wood?
Speed is key. Time to enforcement — even if it’s quarantine — is far more impactful for the security of your organization than anything else. Think of it this way: Given a choice between wood or steel today, choose steel. But if it’s wood today or steel next year, the wood is worth its weight in gold.
In short, if your domain has a DMARC record with a policy of “none,” you need to move to enforcement as quickly as possible to prevent impersonation of your domain. Thanks to Google and Yahoo’s new sender requirements many domains now have a policy of none. However, now’s the time to take that next step, especially since both Google and Yahoo have hinted that stronger requirements will be in the future. The difference between quarantine and reject is relatively small compared to the protection you’ll gain by moving from p=none to either enforcement policy.
Move to DMARC enforcement with Valimail
The journey from a DMARC policy of “none” to a posture of “quarantine” or “reject” is not just a step but a leap towards securing your domain’s integrity and the trust of those you communicate with. The distinction between quarantine and reject policies, while significant, pales in comparison to the vast security chasm that separates a “none” policy from any form of enforcement.
Do not let the complexity of DNS and the nuances of DMARC policies deter you from securing your email ecosystem. Valimail’s platform empowers you to move beyond the vulnerabilities of a “none” policy, offering clarity, support, and the technological prowess needed to implement a “reject” or “quarantine” policy efficiently.
Valimail customers are 2x more successful at reaching DMARC enforcement. Our customers also reach that goal 4x faster than working with other vendors and 8 times faster than doing it on your own.

We’re building the future of trusted email inboxes. To learn how you can take advantage of these benefits: