Email threats have moved past a content-centric approach (aimed at delivering malicious links and attachments) to more sophisticated gambits. These days, nearly all email attacks manipulate sender identity to fool recipients and initiate social engineering attacks.
A comparable percentage are malwareless: They don’t even contain attachments or files that would ordinarily set off malware-scanning alarms because they’re trying to get other valuable information. These emails’ lack of identifiably malicious content means they can easily bypass most current email defenses.
As a result, the problem of preventing malicious attacks isn’t getting any easier to solve. Many attacks take advantage of the fact that employees are working from home, in environments where they may be more distracted, and with potentially less-secure networks and computer hardware.
Meanwhile, phishers continue to iterate their attacks with extreme rapidity. According to Google, 68% of phishing attempts have never been seen before — and the average phishing campaign lasts only 12 minutes. That’s because criminals have automated phishing to avoid detection.
The end result means that phish are getting through existing defenses.
Email has been dealing with unwanted messages and fraud for decades at this point. Originally, those messages were just spam, but scammers quickly learned that email was a great channel for defrauding recipients. The tactics these bad senders use have changed over time:
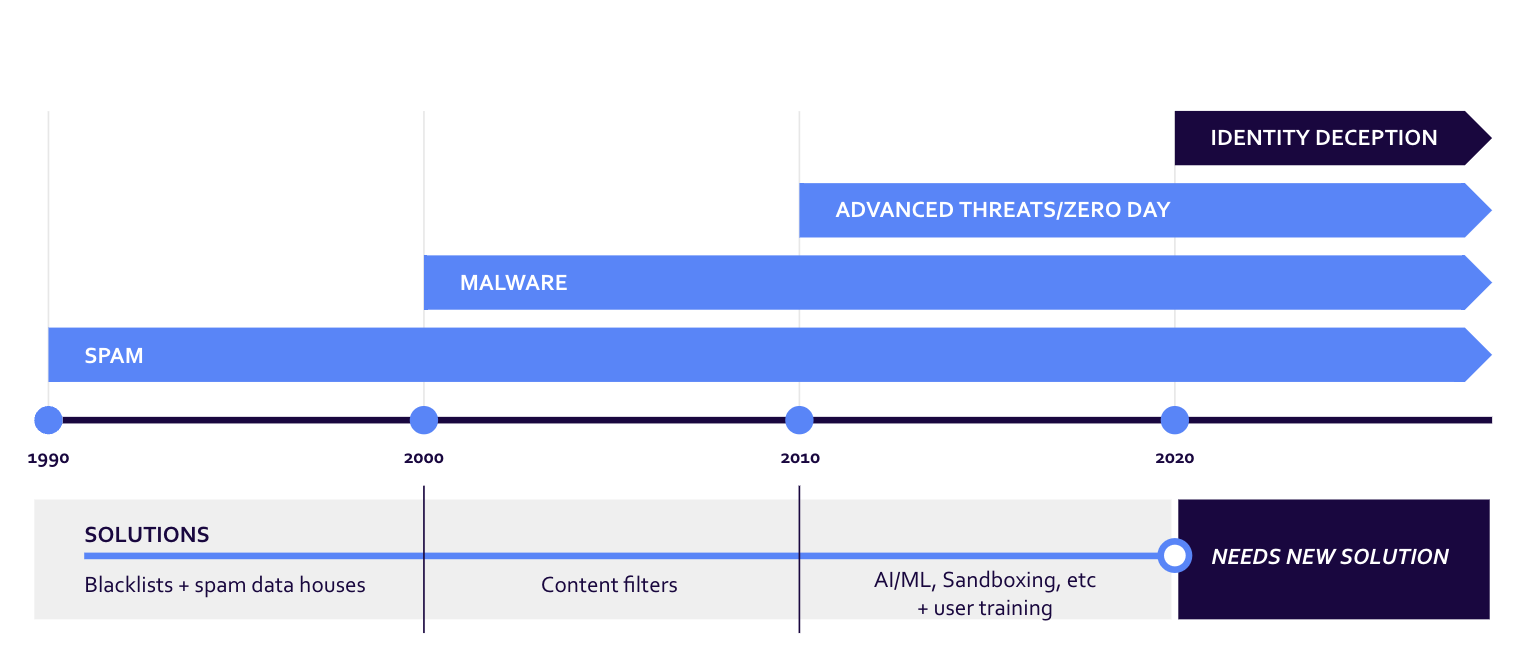
Types of identity-based email attacks
Today, one of the most common forms of email frauds is centered around identity deception. There are three types of identity-based attacks, each of which exploits a unique vulnerability in content-centric email defenses:
- Exact-domain attacks (aka domain spoofing): Emails that directly impersonate a trusted sender by putting their domain in the “From” field of a message
- Untrusted-domain attacks (aka domain impersonation): Emails that are sent from slightly altered “lookalike” or “cousin” domains
- Open-signup attacks (aka user impersonation or friendly-from): Emails that show a legitimate sender name in the “friendly from” field but are sent from an account created on a free consumer webmail service like Gmail or Yahoo
The problem with many security softwares is that they can only identify and block fraudulent emails if they’re encountered similar scams in the past with content analysis, pattern matching, or attachment scanning. Scammers, however, are constantly attempting new and different ways to beat these systems.
Why we need a zero-trust approach to email security
For email, the zero-trust model means not allowing delivery of messages unless they originate from a sender who can be authenticated and who has been granted explicit permission to deliver messages to that inbox.
Artificial Intelligence and machine learning solutions can be effective when it comes to identifying trends in social engineering and malicious content, but they don’t provide much usable information when it comes to sender identity, due to the rapidity with which email attackers mutate their identities.
Instead, with a zero-trust approach, you focus on definitively identifying trusted senders. Once you do that, you can flag or block everything else: You don’t have to worry about finding, analyzing, or scoring the infinite variety of possible malicious senders.
Think of it this way:
- A traditional login system positively identifies known, trusted users (and doesn’t make you worry about analyzing the infinite variety of possible bad logins).
- Similarly, a zero-trust email security system positively identifies known, trusted senders (and doesn’t make you worry about analyzing the infinite variety of possible bad senders).
Zero Trust is going to be the new normal in the very near future. In fact, the Department of Defense (DoD) released their Zero Trust Strategy, and the implications highlight that ensuring information is always verified will be a requirement of any organization, and not just a nice-to-have that impacts things like email deliverability.
In their strategy, the DoD highlight that zero trust is much more than an IT solution:
This “never trust, always verify” mindset requires us to take responsibility for the security of our devices, applications, assets, and services; users are granted access to only the data they need and when needed. We all must play a role in combating our adversaries by acting quickly and correctly to address security threats wherever and whenever they arise.
DoD Zero Trust Strategy, 2022
Benefits of the Valimail approach
Valimail offers a unique, market-leading solution that provides email security through a zero-trust approach to sender identity.
Built on open standards like DMARC, DKIM, SPF, and BIMI, as well as proprietary, patented technology, Valimail validates every message in real time, with powerful automation, to make sure every message originates from a known, trusted sender.
When you have the right DMARC policy in place, you’re telling recipient inboxes that your mail should be delivered correctly, and that any imposters should be rejected (or quarantined at the very least). This means you no longer have to worry about the infinite number of ways a bad actor can attempt to spoof your domain:
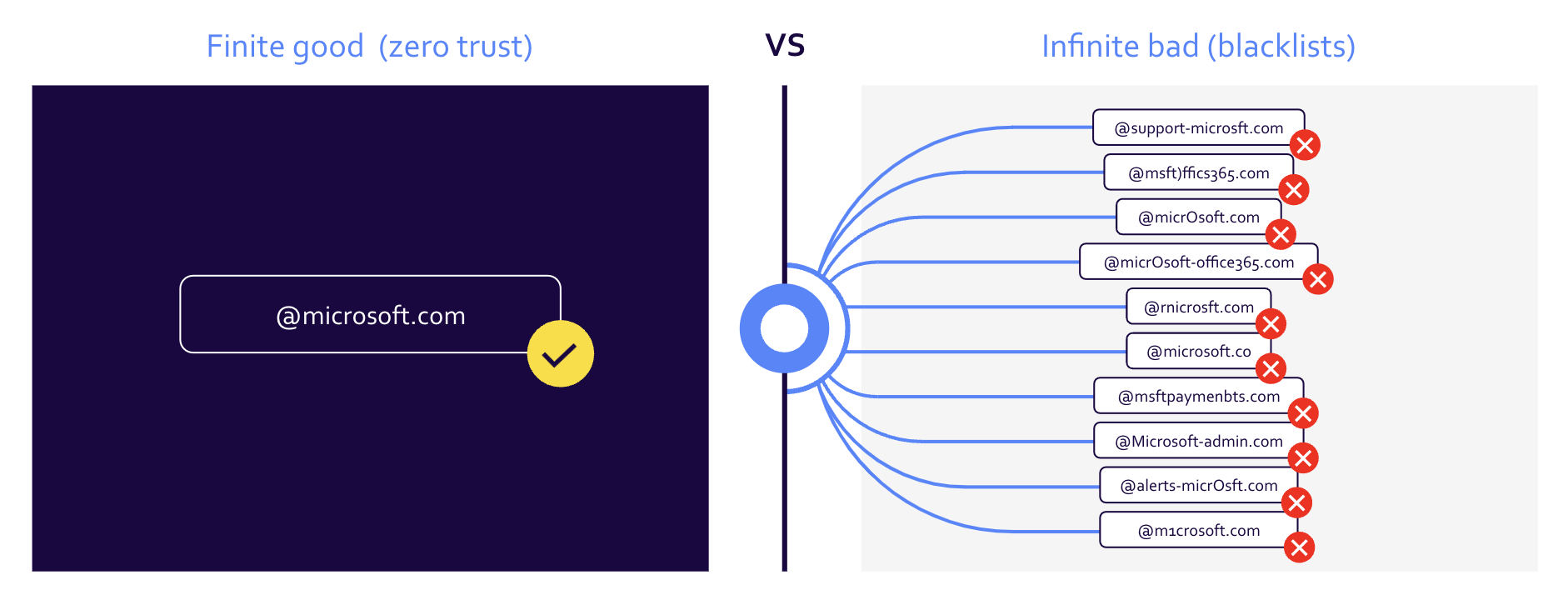
Valimail provides granular, policy-based controls based on roles and risk appetite for your organization, so you decide how you want to handle untrusted services, senders, and contacts — quarantine, delete, or simply monitor. For inbound email, policy controls can be applied company-wide or on an individual or group basis, depending on your organization’s and each group’s particular needs.
To learn how you can implement a DMARC policy at your organization and truly prevent fraud emails, contact us today to schedule a demo, or visit our Pricing Page to select a package that best fits your needs.



