You get an urgent email from your CEO asking for a wire transfer. Seems legit—it’s from their email address, uses the right language, and mentions details only an insider would know. However, it’s actually a Business Email Compromise (BEC) attack, and it could cost your company millions.
Also known as CEO fraud or whaling, BEC attacks have become cybercriminals’ favorite way to target businesses. Why? Because they work. And they were 33% more effective in 2024 than in 2023.
In 2024 alone, these scams cost companies over $16.6 billion, with 256,256 complaints with actual loss, making BEC attacks more expensive than ransomware, data breaches, and other cyber threats combined. That’s an average of $129,000 per incident.
Here’s what makes BEC so dangerous:
- These aren’t your typical “Nigerian prince” scams—they’re sophisticated attacks that combine social engineering with deep research
- Unlike regular phishing emails, BEC attacks rarely include suspicious links or malware that security tools can catch
- Attackers might spend weeks or months studying your company’s communication style and business relationships before striking
- They often target organizations during their busiest times when people are more likely to miss subtle red flags
Bad actors know email can be a powerful and sensitive channel, and they look to exploit it whenever possible. It’s low-hanging fruit for them, and if you’re vulnerable, they will attack.
It’s a matter of when, not if.
Fortunately, you’re not at the whim of cybercriminals. You can protect your business from business email compromise and other forms of cyberattacks. Below, we’ll walk you through everything you need about BEC attacks to protect your brand and customers.
What is business email compromise (BEC)?
BEC is a type of scam where cybercriminals impersonate trusted parties, such as the CEO, business partners, or other executives in a company. The goal is to try and defraud companies of important assets by successfully tricking email recipients into handing over sensitive information and/or data.
BEC attacks typically target businesses, government agencies, or organizations that handle substantial funds or sensitive information.
BEC isn’t your typical “click this suspicious link” scam. These attacks are more like a sophisticated con where criminals study their targets, learn how your business operates, and then strike when you least expect it. What makes BEC particularly dangerous is that these emails often look completely normal—no sketchy attachments, no obvious spelling errors, and no suspicious links that traditional security tools can catch.
BEC vs. email phishing: what’s the difference?
While regular phishing casts a wide net hoping to catch anyone, BEC is more like spearfishing—targeted, precise, and deadly effective. Here’s what makes it unique:
- Requests usually involve large financial transactions or sensitive data transfers
- The attackers do their homework, sometimes monitoring your company’s communications for months
- Emails appear to come from legitimate business contacts you trust
- Messages often reference real projects, vendors, or business operations
- The language and tone match your company’s communication style
The FBI considers BEC one of the most financially damaging online crimes—and for good reason. While a typical phishing scam might net criminals a few thousand dollars, successful BEC attacks regularly result in millions in losses.
And while large corporations might seem like the obvious targets, BEC attackers go after organizations of all sizes. If your business:
- Makes wire transfers
- Works with overseas suppliers
- Has access to sensitive customer or employee data
- Uses public email addresses for executives
Then you’re on their radar.
How do cybercriminals launch BEC attacks?
Attackers typically impersonate a trusted individual or entity, such as a high-ranking executive, business partner, or vendor. They craft impressively deceptive emails to appear legitimate, using techniques like email spoofing, social engineering, or spear-phishing.
They aim to convince the recipient to take specific actions that benefit the attacker, such as making wire transfers, sharing sensitive information, or initiating fraudulent transactions.
BEC attacks often exploit human vulnerabilities rather than relying solely on technical vulnerabilities in computer systems. The attackers may research their targets, gather information from publicly available sources, or even compromise email accounts to gain insights into ongoing business operations and relationships.
Why do bad actors use BEC attacks?
These scams are often financially motivated, with attackers asking you to do an urgent wire transfer. It’s also common for attackers to pose as the CEO or vendor and ask personnel with financial access to re-route a wire transfer to a fraudulent bank account. If you have foreign suppliers, this scenario might be even more common.
Although usually there’s some financial transaction involved, attackers might also use BEC to retrieve sensitive data that they can use in another attack or sell on the dark web.
For example, cybercriminals might aim for your login credentials instead so they can take over your accounts and use them in a later attack.
Additionally, sensitive information, such as Personal Identifiable Information (PII), is also a tangible good to attackers. They can often sell this information to buying parties.
To see if you’re leaving your domain open to these types of attacks, check out our free domain checker. You’ll be able to download a report on the protection status of your domain and take the necessary steps to correct it.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Your Domain
Not protected AGAINST IMPERSONATION ATTACKS
DMARC NOT AT ENFORCEMENT
exampledomain1.com
Authentication Status for January 10, 2025
DMARC at Enforcement
SPF Record Configured
BIMI Ready
exampledomain1.com
Authentication Status for January 10, 2025
DMARC at Enforcement
SPF Record Configured
BIMI Ready
The massive cost of BEC to businesses
In 2023, the FBI determined BEC is the costliest cyber attack.
This annual FBI report also shares that there were 277,918 BEC international and domestic incidents recorded, with an adjusted loss of approximately $50 billion.
“The growing number of attacks and reported losses indicate that these bad actors are not slowing down. Focusing on encrypting data, halting impersonations, and multi-factor authentication have proven to be highly effective in this environment.
Outcomes show that implementing DMARC is one of the highest ROI solutions available. Just make sure to insist on enforcement (activation) and that the process is automated – otherwise DMARC can be daunting.”
Alexander Garcia-Tobar, CEO of Valimail
Email account compromise vs. BEC
Email Account Compromise (EAC) involves advanced techniques that hackers use to gain unauthorized access to a legitimate email account.
Often, EAC is thought to be synonymous with BEC. A considerable portion of BEC attacks is launched from compromised email addresses, which might be where the confusion stems from.
That said, a BEC attack doesn’t have to be done from a compromised account. Sending emails from a legitimate address adds another layer of authenticity.
However, attackers must first infiltrate the email, which requires deep technical knowledge and more resources than hackers may be willing to exert.
BEC itself doesn’t require hackers to have such expertise. Resources are usually spent more on the research portion of the attack. Plus, there are easier techniques to gain trust from a target, like email spoofing and lookalike domains.
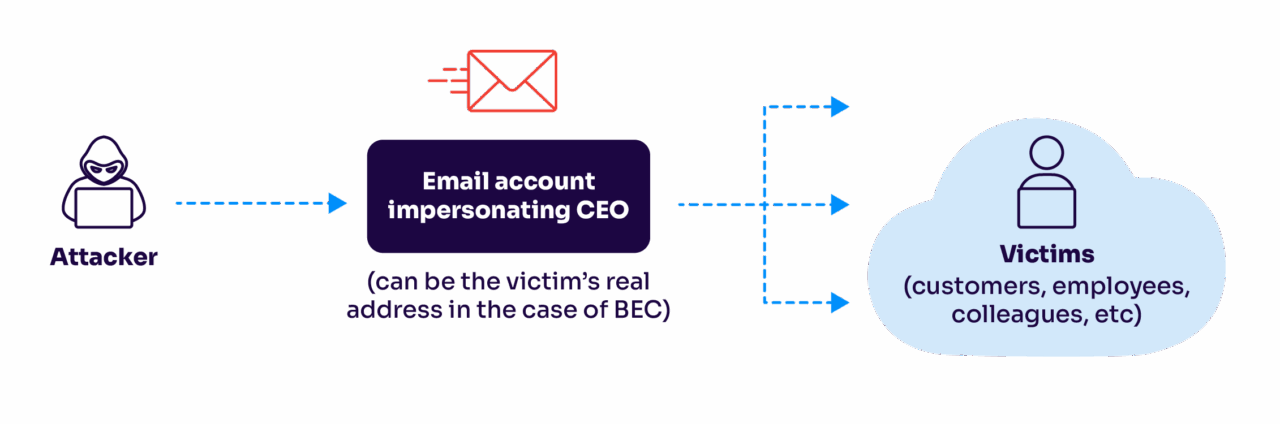
Email spoofing
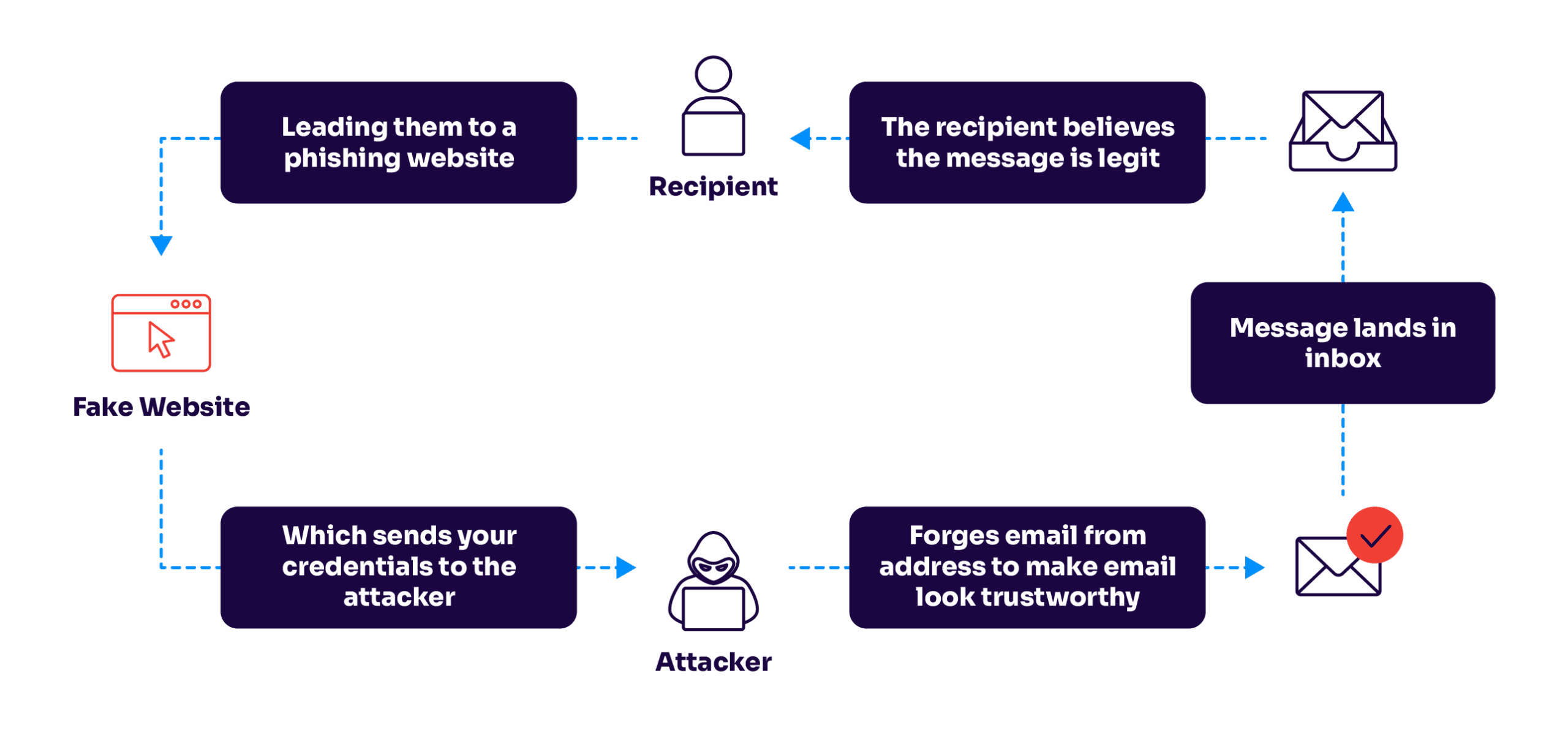
SMTP, the protocol used to send emails, doesn’t have authentication protocols built into it. To do this, email service providers usually do authentication checks by checking the email’s:
These protocols will help you weed out spoofed emails. Without these authentication protocols, or unless you pay careful attention to the sender details, attackers can fake the display name and sender address of incoming email messages.
Lookalike domains
Dozens of domains look like yours; it’s hard to track them all. Attackers take this opportunity to buy these lookalikes and appear legitimate to unsuspecting users. For example, if your domain is called
securityfirm.comthe attacker might purchase:
security-firm.comThis is an easily missable detail that helps them pull off a successful BEC attack.
Common types of business email compromise attacks
There are five types of BEC attacks according to the method used in the attack. Let’s take a detailed look at them below.
1. CEO fraud
In a CEO fraud attack, scammers impersonate someone with executive authority within the company, such as the CEO or other C-suite executives with an official business email account. These two are the most prominent signals of a BEC attack:
- A sudden, unexpected, and urgent request
- A scenario where you can’t verify the transaction with anyone else
CEO fraud takes advantage of the power dynamic within the company. Combined with social engineering tactics like urgency, scarcity, and specificity, that is frequently enough for attackers to persuade the target to do what they request.
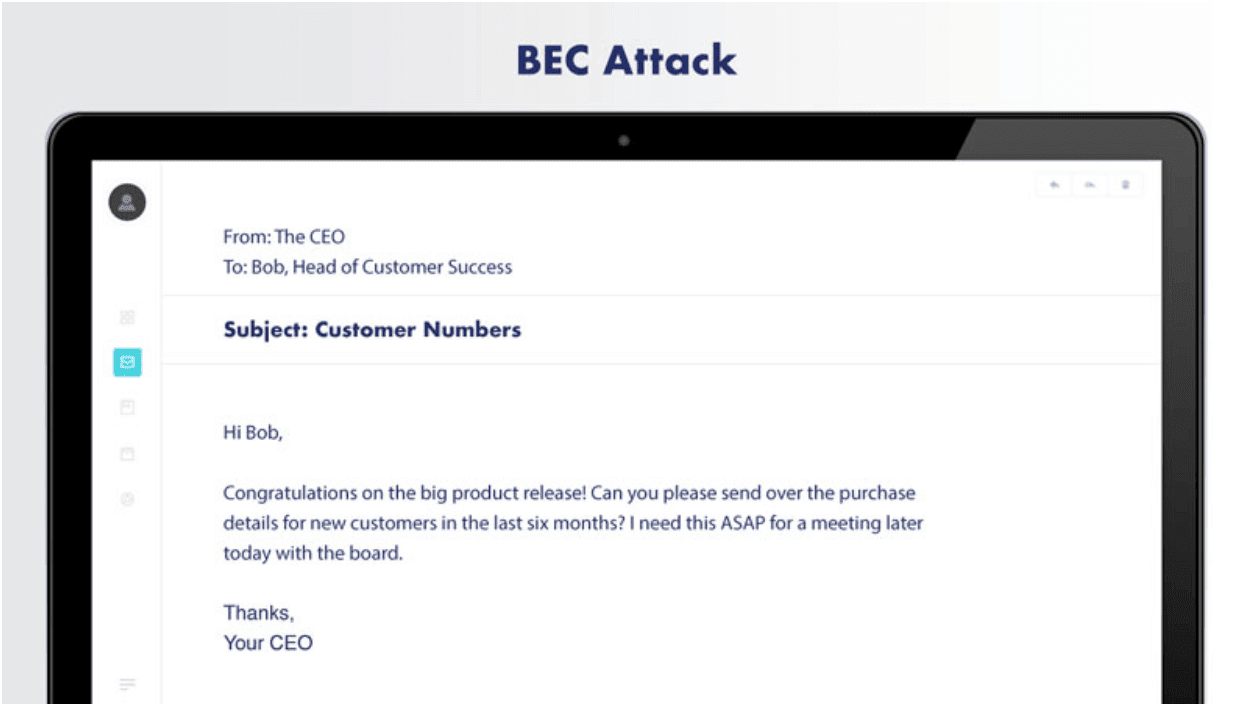
A typical scenario for CEO fraud is when an attacker poses as a CEO and sends an urgent request for a transfer of funds to someone in the finance department.
The CEO could say they’re meeting with a vendor and discovered that the last payment didn’t go to their new account. The CEO might then request a junior-level accountant to pay right now so they can maintain a good relationship with the vendor.
Another common play is posing as an executive and mentioning that they’d like to appreciate employees with gift cards. Then, they’d ask the target to help them purchase the gift cards using company funds but to keep it a secret because they want it to be a surprise.
2. Account compromise
With email account compromise or account takeover, attackers use a compromised account to launch their attack. Given that it comes from a legitimate email address, it won’t trigger any security notification from the target’s email security tools. Additionally, if it’s an email address the recipient is familiar with, they might let their guard down.
Attackers might launch this attack against a client and ask them to update the payment details they have on hand with a fraudulent bank account instead.
A legitimate email account also makes it easier for hackers to request sensitive data internally, especially if the compromised account has high-security permissions.
3. Attorney impersonation
As the name suggests, hackers impersonate the legal professionals you work with. People often panic when they hear about legal troubles, which might be why attorney impersonation works so well.
The target for attorney impersonation is low-level employees with no way to validate the request. The “legal” or administrative request usually comes at the end of the workday when recipients don’t have anyone to consult. And since it appears confidential and urgent, the unwitting employee obliges the request anyway.
4. Data theft
Instead of money, attackers in data theft aim for personal or sensitive information that can be used for future attacks. The main target for these attacks is often the HR and bookkeeping department, which collects and stores employees’ most sensitive personal data, such as social security numbers or tax IDs.
Fraudsters might use this to augment future attacks, but they’ll also likely sell this information on the dark web. Beware of identity theft if sensitive employee details are recently leaked this way.
5. False invoice scheme
Most often seen when working with foreign suppliers, this type of BEC attack involves attackers posing as a vendor to send a fake invoice with fraudulent account information attached.

The attachment often doesn’t contain any malware either, so it won’t set off your anti-malware scans.
The supposed vendor might send this to your finance department, mentioning that they have moved to a new bank account and attaching the fraudulent bank details.
Phases in a business email compromise attack
Although there are not many similarities between each type, the general steps attackers take during a BEC scam are similar.
Here’s how a hacker might carry out BEC. Don’t worry—we’ll discuss steps to protect yourself next.
1. Email account targeting and research
Most experienced hackers invest a significant portion of their resources into identifying their target and then conducting thorough research about the company.
Beyond public info available on the internet, like social media posts, press releases, or the news, hackers will try to find more confidential business information about the company in mind.
This kind of reconnaissance includes familiarizing themselves with some of the following:
- Specific business processes
- Workflows involved in different employees’ day-to-day responsibilities
- Who is responsible for making payments
- Details about payments made to vendors (schedules, banks, etc.)
2. Commencing the cyberattack
After gathering enough information, fraudsters decide whom they will attack and what believable scenario they will craft to ensure the best chance of success.
They decide on the method they’re going to use and prepare accordingly. They’ll start to:
- Craft phishing emails
- Gain access to the email address they’re going to use
- Eventually, start sending the personalized, specific phishing email to the target
3. Social engineering
At this stage, fraudsters start doing what they do best—persuading the target and earning their trust.
Hackers are already halfway there by impersonating trusted figures and using various social engineering techniques. At this point, they’ll try to get the target to do the task they want and prevent them from checking with another person who might recognize this as a scam.
4. Data breach
This is the end goal for most hackers.
After successfully convincing the target, this is where fraudsters essentially “collect” and where you might realize you’ve fallen victim to an attack.
The reward for hackers might be financial gain, such as a transfer of funds, but it can also be a data breach that leaks private information to the hacker. In this case, they’d be able to use this data for future attacks, distribute them, or, again, sell them.
What to do if you’re a victim: Ideally, hackers shouldn’t reach this stage, and you’d be able to protect against any data loss. However, if they did, immediately call your bank and see if you can dismiss the funds transfer. Additionally, file a complaint with the FBI’s Internet Crime Complaint Center (IC3) to ensure the incident has been recorded so it can be investigated.
How to prevent BEC attacks
Protecting against BEC attacks requires a combination of technical measures and employee awareness. Here are some steps you can take to safeguard your organization:
- Email Authentication: Implement email authentication protocols such as SPF, DKIM, and DMARC (Domain-based Message Authentication, Reporting, and Conformance) to verify the authenticity of incoming emails and prevent email spoofing.
- Employee Education and Awareness: Conduct regular security awareness training to educate employees about BEC attacks, phishing techniques, and social engineering tactics.
- Strong Passwords and Multi-Factor Authentication (MFA): Enable multi-factor authentication or two-factor authentication (2FA) for email accounts and other systems to add an extra layer of security.
- Secure Processes: Establish strict procedures for authorizing and verifying financial transactions, especially large payments or changes to payment details.
- Security Monitoring: Deploy advanced email security solutions that can detect and filter out suspicious emails, including those associated with BEC attacks.
- Incident Response: Establish an incident response plan to guide employees on how to report and handle suspected BEC attacks promptly.
As BEC emails rarely contain malware, it’s hard to detect these types of phishing scams if you rely on endpoint security solutions alone.
The key in a BEC scam is that there’s usually a sense of urgency built into the messages, and it doesn’t allow you to follow up with the people involved in the process.
For emails with markers like these, you should trust your gut and ask yourself: Does the email request make sense? Did you expect the email?
Real-world BEC attack examples
You might think falling for a scam email would never happen to your company. But when some of the world’s savviest organizations have lost millions to BEC attacks, it’s worth paying attention. Here are some eye-opening examples of how these scams play out in the real world.
Notice that each attack succeeded because it:
- Exploited normal business processes
- Came from what looked like a trusted source
- Made a reasonable-sounding request
- Created a sense of urgency
- Caught people during busy or stressful times
The scariest part? None of these attacks needed sophisticated malware or hacking tools. They just needed a convincing email, and someone was too busy to double-check. Seriously. That’s it.
The $60 million mistake at Orion
In August 2024, carbon-black manufacturer Orion S.A. discovered that a non-executive employee had been tricked into sending multiple wire transfers to attacker-controlled accounts. The company told the SEC it expects a one-time charge of $60 million after recovery efforts.
A $3.4 million lesson for one school district
While juggling new curriculum funding, Johnson County Schools (Tennessee) got an email in 2024, supposedly from textbook giant Pearson, asking for updated banking details. Two transfers later, $3.36 million in state education funds were gone; less than $750k has been clawed back.
The $6.4 million “Beneficiary Change” request
In January 2023, a Massachusetts workers’ union received what looked like a routine note from its investment manager: please use this new account for the upcoming $6.4 million transfer. It wasn’t the manager—it was a BEC gang. Federal investigators later seized $5.3 million but warned that the remaining funds had already been laundered through accounts in Asia and crypto exchanges.
Hijacked construction invoice worth half a million dollars
Government agencies aren’t immune either. In June 2024, the Town of Arlington, MA, lost nearly half a million dollars when scammers hijacked a construction invoice thread and redirected four payments.
$2.1 million lost to vendor email compromise
That same year, a New South Wales government department in Australia wired AU $2.1 million to crooks posing as a trusted vendor. Both cases prove that if an email looks legitimate and DMARC doesn’t protect the domain at enforcement, even public-sector funds are an easy target.
Protect against BEC and scams with Valimail
BEC emails will fail regardless of the hacker’s social engineering skills if the email never reaches your inbox in the first place.
This is where DMARC can help.
Having DMARC enforcement for your domain helps your employees identify spoofed emails sent on behalf of your domain. If you’re looking for the most cost-effective way to reach DMARC enforcement without overloading your IT team with more requests, Valimail Monitor can get you up and running quickly.
Frequently asked questions about business email compromise (BEC)
How does DMARC stop BEC?
It lets receiving email servers verify that messages using your domain are genuine and reject spoofed look-alike domains.
Is BEC the same thing as phishing?
No, phishing casts a wide net, but BEC is spear phishing that impersonates a known contact and doesn’t typically contain malicious links.
Who investigates BEC losses?
In the United States, the FBI investigates BEC attacks. If you think you were attacked, file with the FBI’s IC3 portal within 48 hours. The faster you report it, the higher the success rate is for freezing funds.


