Whaling attacks target the “big fish” of the business world—the high-ranking executives, the decision-makers, and the influential. They’re a highly targeted form of phishing tailored to deceive the most senior individuals within an organization through meticulously crafted emails, messages, or even phone calls.
These attacks don’t just cast a wide net—they use a finely sharpened spear to pierce through the defenses of the most cautious and discerning individuals. And the bait? Often, it’s a mixture of trust, personalization, urgency, and seeming legitimacy.
The stakes in a whaling attack are high. For businesses, it’s not just about financial loss, though, that can be substantial. The reputational damage, erosion of client trust, and potential legal ramifications can ripple from a successful attack.
Below, we walk you through the ins and outs of whaling attacks, outlining how they work, who they tend to target, and best practices to prevent them.
What is a whaling attack?
Whaling attacks describe a sophisticated and highly targeted subset of phishing schemes. They are named after the concept of “hunting big fish,” which in the cyber world refers to high-profile targets like CEOs, CFOs, or other senior executives.
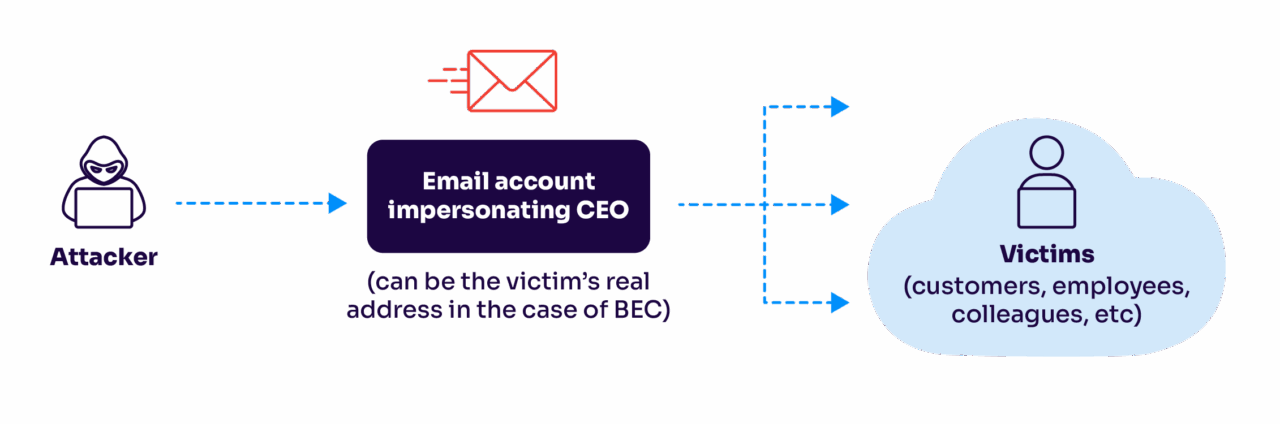
Unlike standard phishing attempts that might target wide arrays of recipients with generic lures, whaling attacks are tailored to their specific victims, leveraging detailed knowledge about their targets to craft believable and compelling traps. Here’s how whaling attacks are different:
- Targeted Individuals: They specifically aim at high-profile targets with substantial authority or access to critical company resources.
- Sophistication and Personalization: The level of detail in these attacks is significantly higher. Attackers may use information from social media, company websites, and other public sources to craft believable messages.
- Nature of Requests: The requests in whaling emails often align with the executive’s role, such as wire transfers, confidential data sharing, or urgent decision-making.
Common whaling attack tactics
Cybercriminals use a variety of sophisticated techniques to trick high-profile targets, but there are a few general themes for these attacks:
- Social Engineering: Attackers often gather detailed information about their targets through social media, company websites, and other public sources. This information is then used to craft highly relevant and personalized messages to the recipient.
- Email Spoofing: Attackers may use an email address that closely resembles a legitimate one, often by altering just a few letters. This technique relies on the victim not noticing the slight discrepancies in the email address.
- Spear Phishing: Whaling attacks use tailored messages specific to the individual’s role, interests, or ongoing projects within the company. Attackers often impersonate CEOs, CFOs, or other high-ranking officials, lending credibility to their requests.
- Communication Manipulation: In some cases, attackers gain access to an actual executive’s email account, making their fraudulent communications even more convincing. For phone-based attacks, techniques like caller ID spoofing can make calls appear to come from a known, trusted number.
- Fake Assets: Attackers might use forged documents, like fake subpoenas or contract agreements, which require the target’s immediate attention or action. Sometimes, the attack involves directing the target to a fake website that looks identical to a legitimate site, where they are asked to enter sensitive information.
Whaling vs. phishing vs. spear phishing
Phishing attacks come in different shapes and sizes, like fishing lures designed to catch different types of fish. They all share the goal of tricking victims into revealing sensitive information or taking harmful actions, but knowing the differences between these attack types can help you better protect yourself and your organization.
| Aspect | Standard Phishing | Spear Phishing | Whaling |
| Target | Mass audience | Specific individuals or departments | C-suite executives and high-profile targets |
| Research Level | Minimal | Moderate | Extensive and in-depth |
| Personalization | Generic | Somewhat personalized | Highly personalized with executive-specific details |
| Content Quality | Often contains errors | More polished | Very sophisticated and professionally crafted |
| Goals | Credentials, malware installation | Access to specific systems or data | High-value wire transfers or critical data theft |
| Example | “Your account needs verification” email to thousands | Email to HR staff requesting W-2 information | Email appearing to be from CEO to CFO requesting urgent wire transfer |
Standard phishing casts a wide net—sending thousands of generic emails hoping a few recipients will take the bait. Think of those “Your account has been compromised” messages that land in everybody’s inbox. They’re often filled with spelling errors and suspicious links.
Spear phishing narrows the focus. Attackers research specific targets (like your marketing team) and write messages relevant to their work. These emails might reference current projects or use the right company terminology, making them much more convincing than standard phishing attempts.
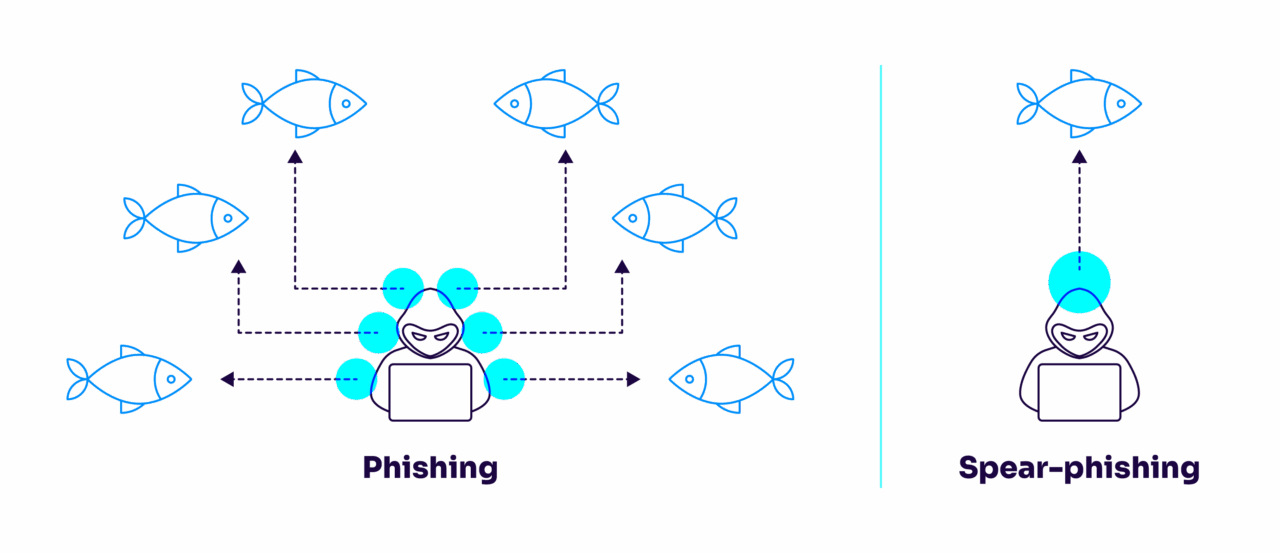
Whaling takes targeting to another level entirely. These attacks aim for the “big fish”—your C-suite executives with access to the most valuable company assets. What makes whaling particularly dangerous is the meticulous research attackers conduct. They’ll study the executive’s communication style, current business dealings, and even personal interests to write nearly perfect impersonations that can fool even security-conscious leaders.
Examples of whaling attacks
Whaling attacks aren’t necessarily new, but there have been plenty of high-profile stories with some big names in the news over recent years. Without pointing any fingers at exact names or companies, let’s look at a few to see how they differ and what they might have in common:
Popular social media company whaled
Bad actors targeted a well-known social media network’s high-ranking employee in human resources. The scam was executed through a carefully crafted email sent to one of the company’s employees in the payroll department. The email appeared to come from the CEO, asking for employee payroll information, and it was convincing enough that the employee complied, sending the attacker confidential payroll information.
Major tech corporation’s data breach
Bad actors targeted a high-ranking finance executive at a renowned technology company, crafting a deceptive email that perfectly mimicked the style and tone of communication from the company’s upper management. The email requested the W-2 forms of all current and former employees, a request that the executive, believing it to be a legitimate internal inquiry, fulfilled.
This breach exposed the sensitive tax information of nearly 10,000 employees, leaving them vulnerable to potential income tax refund fraud and identity theft.
CEO falls victim to whaling attack
A high-profile whaling attack made headlines when the CEO of a prominent aerospace manufacturer fell victim to a sophisticated scam. The attackers posed as senior executives in a series of deceptive emails, leading the company’s finance department to believe they were conducting a legitimate transaction.
As a result, the finance team wired a staggering $56 million to an account controlled by the fraudsters—and the CEO lost his job.
How to prevent whaling attacks
There’s no silver bullet when it comes to dealing with whaling attacks. You’ll need to implement a mix of technical safeguards and general training. Here’s how to get started:
1. Organizational measures
Your organization’s internal policies and practices are the foundation of your cybersecurity measures. Establish robust security efforts and foster a culture of awareness to create a solid first line of defense.
- Security Policies: Develop and enforce comprehensive security policies that address the specific risks of whaling attacks.
- Incident Response Plan: Build a clear and tested incident response plan in case of a security breach.
- Regular Audits: Conduct security audits and risk assessments to identify and mitigate vulnerabilities.
- Limited Access: Implement a policy of least privilege to ensure employees have access only to the information necessary for their roles, limiting the damage in case of a breach.
2. Technical protection
Technical safeguards complement your organizational strategies to stop whaling attacks in their tracks. With the proper email authentication protocols and security standards in place, bad actors might not even get the chance to test your organization or its employees. These safeguards involve deploying state-of-the-art technology solutions that detect, prevent, and respond to sophisticated phishing attempts.
- DMARC: Implement Domain-based Message Authentication, Reporting, and Conformance (DMARC) to authenticate emails and prevent domain spoofing.
- Email Validation Software: Use advanced email security solutions that can detect and filter out phishing attempts.
- Secure Communication Channels: Encourage the use of safe, verified channels for transmitting sensitive information.
- Encryption: Encrypt sensitive data (both in transit and at rest) to protect it from being intercepted or misused if an employee is tricked into sharing it.
- Regular Software Updates and Patch Management: Keep all software up to date with the latest patches to close security vulnerabilities that attackers might exploit.
3. Training and awareness
Ultimately, employees are the target behind any whaling attacks. Training and awareness measures equip your employees with the skills and know-how to recognize and respond to these sophisticated threats. Regular, interactive training sessions (along with a continuous emphasis on cybersecurity awareness) empower employees at all levels to become proactive participants in your organization’s overall security posture.
- Regular Training Sessions: Conduct regular training for all employees, with specialized training for high-risk positions.
- Simulated Attacks: Run simulated phishing and whaling attacks to test employee awareness and response.
- Continuous Education: Keep staff updated on the latest phishing tactics and encourage a culture of security awareness.
- Phishing Reporting Mechanisms: Establish an easy-to-use system for reporting suspected phishing attempts to help quickly identify and mitigate threats.
Protect your organization from whaling attacks with DMARC
Now that you understand the dangers of whaling attacks and how they work, it’s time to take action. As you’ve seen, the consequences of these sophisticated phishing scams can be devastating, leading to financial losses, reputational damage, and even legal repercussions.
While there’s no single solution to prevent whaling attacks, implementing a layered approach that combines organizational measures, technical protection, and employee training is crucial.
However, one key technical safeguard stands out from the rest: DMARC.
DMARC is a powerful shield against whaling attacks by authenticating emails and preventing domain spoofing. It works by:
- Verifying Sender Identity: DMARC ensures emails claiming to come from your domain actually originate from authorized sources.
- Protecting Your Brand: By preventing unauthorized use of your domain, DMARC protects your brand reputation and instills trust in your customers and partners.
- Providing Actionable Insights: DMARC reports offer valuable information about email traffic, helping you identify potential attacks and improve your overall security posture.
Ready to get started with DMARC? We can help. We’ve blocked 8.6 billion bad actors and counting. For companies like Travers Smith, we’ve stopped an average of 95,000 phishing emails monthly.
Prioritizing our DMARC implementation with our management team was easy once we explained the risk and how we could eliminate the risk – and protect the Travers Smith brand, our customers, employees, and partners.
Darragh Macken, Head of Information Security at Travers Smith
Valimail streamlines your DMARC implementation and gives you control of your email security. Our user-friendly platform and expert guidance simplify DMARC deployment while robust enforcement stops email fraud cold. Gain valuable insights with detailed reporting and enjoy expert support every step of the way.
See what bad actors are using your domain and uncover other security risks with Valimail Monitor. You can create a free account without any free trials or credit cards.


