Email impersonation attacks are on the rise.
The cost of business email compromise (BEC) totaled more than $50 billion over a nine-year period ending July, 2019, according to the FBI. Meanwhile, email security vendor Barracuda recently found that almost 90% of email attacks use impersonation, either of a brand (83%) or a person (6%). Another vendor found that phishing attacks that impersonate senders have increased by 25% over the last year.
These facts are connected. Learn how you can prevent email impersonation attacks so you don’t have to worry about the statistics.
What is an email impersonation attack?
An email impersonation attack, sometimes known as spoofing, is when a cybercriminal pretends to be someone you trust to trick you into giving up sensitive information, transferring money, or even clicking on malicious links. It’s like a digital wolf in sheep’s clothing.
BEC is a type of spearphishing attack that relies on impersonation to fool the recipient into believing that the message came from a trusted sender. Rather than convincing the recipient to click on a malicious link, enter a password on a bogus login screen, or download a Trojan horse document, BEC messages aim at direct extraction of value from their target.
They pose as fake invoices, bank instructions, or payroll direct deposit requests.
Imagine you get an email from your boss asking you to urgently transfer funds to a new vendor. The email looks legitimate, complete with a signature that matches your boss’s. But something feels off. This gut feeling could be your saving grace because you might be facing an email impersonation attack.
Almost all email attacks involve impersonation, as the Barracuda stat above shows, but BEC is unique in that these emails rarely contain malicious content detectable by most email security systems. Email impersonation attacks are BEC’s primary technique, and current email security systems aren’t very good at detecting impersonations.
These attacks often play on our emotions, using urgency or authority to create a sense of panic or trust. Imagine receiving an email that looks like it’s from your CEO, marked “URGENT,” asking for confidential company data. The immediate reaction is to comply without question, especially when it’s from someone high up the chain.
Attackers are exploiting this weakness in corporate defenses — and that’s leading directly to the rise in BEC losses.
Types of email impersonation attacks
We are seeing three main types of sender impersonation attacks: exact-domain, untrusted-domain, and open-signup attacks.
1. Exact-domain attack

Exact-domain attacks impersonate a known sender using their exact domain name in the “From” field (in the email’s headers). The Global Cyber Alliance estimates that, at a minimum, 5-15% of business email compromise attacks use exact-domain impersonation. This is a conservative estimate; other estimates vary between 20% to 60%.
These types of attacks spoof your domain directly. Attackers use this technique to impersonate someone like your CEO, compelling a colleague to do something “wrong”— like wire transfer large sums of money to third-party accounts or expose employees’ tax records for future identity theft. These impersonations are very effective because the sender’s address is actually on your company’s domain.
2. Untrusted-domain attack

Untrusted-domain attacks, otherwise known as lookalike or cousin domains, and sometimes called homograph attacks or typosquatting domains, imitate a legitimate return address, using subtle typographic changes to disguise their true identity. Careful inspection of the email header may reveal fake domain names such as “1bm.com” instead of “ibm.com”, for example — assuming that the end user thinks to look closely.
Keep in mind that, some of these faked domains may be entirely indistinguishable from the real ones, at least to the human eye. What’s more, the visible From: address may be hidden in some email clients, especially on mobile devices. So inspecting the sender is no guarantee that you’ll catch these.
3. Open-signup attacks
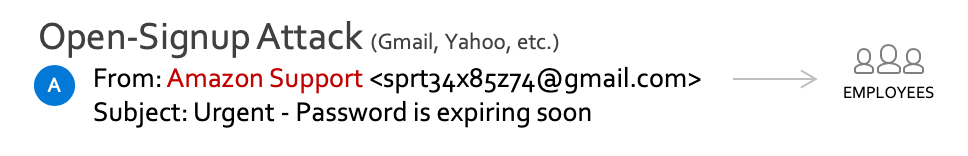
An open-signup attack is a fraudulent email that shows a legitimate sender name in the display field (the “Friendly-from”) but is sent from a random account created on free consumer webmail services like Gmail or Yahoo Mail. Sometimes these attacks are referred to as “Friendly-from attacks” because they rely on deceptive text in the “Friendly-from” field of the email header.
Open-signup attacks are difficult to block since the email domains themselves (like gmail.com or yahoo.com) are known and widely used — most organizations can’t just block these domains without cutting off legitimate senders who use them.
This type of attack is also very common because it’s so easy to execute. Anyone can sign up for an account and masquerade as a trusted contact (e.g. your CEO) or a trusted service (e.g. Amazon Support), with no restrictions. This type of attack can be surprisingly effective.
Put an end to impersonation emails
What’s needed to stop these three types of attacks is a robust approach to validating sender identity. That’s where Domain-based Message Authentication, Reporting, and Conformance (DMARC) comes in.
For exact-domain attacks, using DMARC at enforcement is critical: It ensures that only authorized senders can send email from your domain; all spoofs are blocked.
For untrusted-domain and open-signup attacks, enterprises need a way to allow only trusted senders access to corporate inboxes. Untrusted senders — whether they are using a deceptive domain or a throwaway account on an open-signup account — should not be able to deliver their messages into end-users inboxes.
To stop these attacks, a strong sender identity solution — in combination with other types of security — is essential. Without a strong approach to sender identity, impersonation attacks like these will continue to wreak havoc and cost companies billions of dollars.
Want to know more? Put an end to phishing and find out how Valimail blocks these attacks once and for all.

