Fake email sender identity remains one of the most potent tools in a hacker’s arsenal. Despite investments in email security tools (SEGs, filters, threat engines), attackers still successfully impersonate brands and individual senders. Why? Because most defenses don’t address the root problem: broken email identity.
Unfortunately, many email attacks are now malwareless, and the attack vector has shifted to faking sender identities. Most phishing attacks are brand impersonations, but some do impersonate specific people. In other words, about 9 out of 10 phishing attacks now use fake sender identity.
In this post, we’ll explain what fake sender identity actually is, why traditional security tools struggle to stop it, and how modern sender identity authentication (SPF, DKIM, DMARC, managed enforcement) is the only reliable defense. You’ll also see how Valimail’s approach differs, and what steps your organization should take now.
| Key takeaways: – Fake email sender identity remains one of the top tactics in phishing and BEC attacks – Traditional email filters and SEGs can’t reliably block messages sent from fake mail sender domains – Tools that let bad actors send from a fake email address are freely available and widely used – The best defense is enforcing email authentication standards like SPF, DKIM, and DMARC |
What is a fake email sender?
When using a fake email identity, cybercriminals spoof unsecured domains to send phishing emails to employees, customers, and partners. These messages appear to have originated directly from the impersonated domain and often bypass most secure email gateways because they lack the malicious content or other characteristics that these gateways can detect.
For example, the World Health Organization issued warnings that scammers were impersonating the organization’s officials with emails that appeared to come directly from the WHO’s own domain. This story from Vox explains how coronavirus scammers send fake emails from real domains, and why it’s so easy for them to get away with this.
How easy is it to send a fake email?
Spoofing a fake email sender isn’t just possible, it’s practically effortless. Bad actors can utilize online fake mailer tools, open-source scripts, or public SMTP servers to send emails from a fake email address and impersonate your brand.
Here are just a few ways attackers launch fake email sending campaigns:
- Free fake mailer websites that let users input any “From” address
- Open relay servers that aren’t configured with strict DMARC, SPF, or DKIM rules
- PHP scripts that allow bad actors to send email fake from compromised or misused systems
If your domain lacks enforced email authentication, anyone can send from a fake email address that appears legitimate.
Why traditional email security solutions might not catch them all
Messages with fake sender identities often raise no red flags and pass right through most secure email gateways (SEGs), particularly if they lack malware or identifiable links. Business email compromise (BEC) messages often employ this approach, avoiding malware that might trigger an SEG to block the message while taking advantage of the implicit trust that people tend to place in email messages that appear to come from their employer or someone with whom they do business.
When these messages utilize exact-domain spoofs, no amount of training can help as it is impossible to tell the good email from the bad.
Exact-domain attacks are the messages that use your domain name in the From: field but are not originating from your organization or one of the cloud services you’ve authorized. Because companies today tend to have many cloud services, and most of those need to send email on their behalf, some messages coming “from” your domain are legitimate. Your HR tool, marketing automation service, or CRM sent them.
Other messages are unknown in origin. Some may even come from a malicious sender attempting to impersonate you.

The consequences of fake mail sender identity
The risks are obvious when attackers use your organization’s email domain to phish your employees. Employees may be duped into thinking that the messages come from their boss, the CEO, or even someone in IT, and then click on links, enter passwords on malicious sites, or install Trojan horse software.
But it’s also a problem when those messages are sent to recipients outside your organization:
- Customers and partners who learn they have been phished will stop trusting your brand
- Messages will get flagged as spam
- Legitimate emails won’t get delivered
Most organizations don’t see the problem until someone lets them know about a phishing email they received. When these spoofed emails are being sent to partners or customers, that notification may never happen, and if the company is not monitoring how its domain is being used, it will never know.
Why DMARC enforcement creates a layered solution with SEGs and traditional filtering
Together, SEGs and email authentication are the perfect match. If SEGs are the front gate, DMARC enforcement i your blocked badge reader to make sure no fake mailer gets through your defenses. Here’s how they compare and work together:
| Feature | SEGs / Filters | Valimail with DMARC enforcement |
| Stops malware | Often | Not the goal |
| Stops a fake email sender | Limited | Yes, when DMARC enforcement is active |
| Authenticates sender identity | No | Yes, DNS-based verification |
| Works with trusted senders | Sometimes | Validates cloud services and vendors |
| Blocks email spoof | Can miss exact-domain spoofs | Fully blocks domain spoofing |
| Sends spoofed email to spam | Can be missed | With p=quarantine or p=reject |
| Visibility into senders | Limited | Full, human-readable reports |
TL;DR: You need both SEGs and email authentication. SEGs catch content-based threats. Valimail stops fake mail sender attacks by fixing email identity.
How to stop fake email sending with email authentication
To stop spoofing, phishing, and fake email senders, the email ecosystem leans on three core standards as the foundation:
- SPF (Sender Policy Framework): Defines which IP addresses can send mail for your domain
- DKIM (DomainKeys Identified Mail): Cryptographic signature proving message integrity
- DMARC (Domain-based Message Authentication, Reporting & Conformance): Tells receivers what to do when SPF or DKIM fails (report it, quarantine it, or reject it)
Some organizations are more proactive and start the process of monitoring their domain using DMARC’s reporting capabilities. This gives them visibility into how their domains are being used for email, regardless of whether recipients are inside the company.
In monitoring mode, we set a DMARC policy of p=none, which allows all outbound traffic to arrive at its destination uninhibited. Mail receivers then send daily reports to the address listed in your DMARC record, aggregating information about what senders were using your domain and whether they passed the authentication rules you set up in SPF or DKIM.
DMARC aggregate reports are a rich store of data, but they can be difficult to parse. Valimail Monitor aggregates these reports and displays them in an intuitive, graphical format that makes it easy to see trends over time. Monitor also helps because, unlike other DMARC tools, it doesn’t present inscrutable lists of IP addresses — it translates those into readable, named senders, so you can see exactly which cloud services are sending on your behalf.
Stop fake email messages from your domain
Another Valimail customer started by monitoring their domain to identify all the services sending email from the domain and validated the ones they wanted to keep.
Once the institution validated all the sending services they wanted to keep, they moved their DMARC policy from monitoring (p=none) to a quarantine enforcement policy (p=quarantine). This quarantine policy told the receiving mail providers to put any unvalidated messages into their recipients’ spam or junk mail folders.
Within two months, the financial institution had identified all the services they wanted to approve, updated DMARC records and DNS using Valimail’s automated solution, and were ready to turn their enforcement policy to p=reject, which instructs receiving mail providers to delete unvalidated messages completely.
Once at p=quarantine or p=reject, attempts to spoof the domain typically taper off as attackers realize that their spoofed messages aren’t getting through to inboxes anymore. In other words, the volume of domain spoofing declines once you implement DMARC enforcement.
Reaching DMARC enforcement requires careful work to ensure no good email gets blocked. The process can be painful without excellent visibility and automation.
Check your DMARC policy for free with Valimail’s domain checker:
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Your Domain
Not protected AGAINST IMPERSONATION ATTACKS
DMARC NOT AT ENFORCEMENT
exampledomain1.com
Authentication Status for January 10, 2025
DMARC at Enforcement
SPF Record Configured
BIMI Ready
exampledomain1.com
Authentication Status for January 10, 2025
DMARC at Enforcement
SPF Record Configured
BIMI Ready
What makes Valimail different in stopping spoofed emails?
Valimail is purpose-built to stop email spoof attempts that bypass traditional security layers. Here’s how we do it differently:
- Real-time visibility: See every sender using your domain with human-readable, not raw IPs
- Intelligent automation: Identify and approve legitimate services quickly
- Enforcement acceleration: Go from p=none to p=reject confidently, without disrupting good email
- Free solutions: Set up Valimail Monitor in under 5 minutes, no email interruption, zero risk
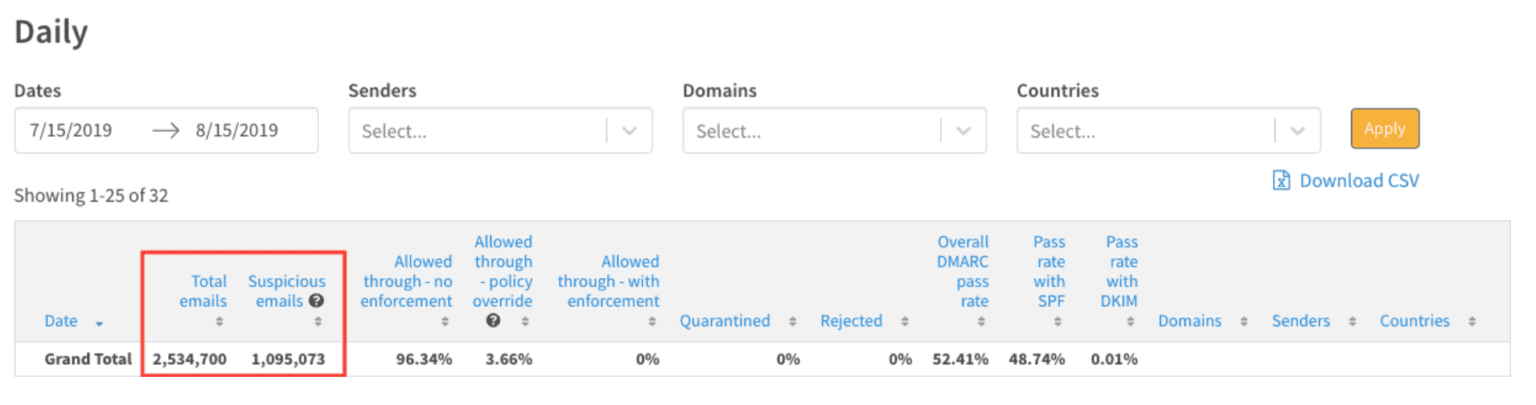
Valimail lets you see at a glance the total number of messages sent “from” your domain, how many passed authentication with DMARC, how many failed, and how many came from suspicious senders.
Valimail Enforce shows the total number of suspicious emails sent “from” a customer’s domain. The number of emails appearing in the “Suspicious emails” column is surprisingly large for most unsecured domains. For example, an insurance company using Valimail discovered half of its outbound emails were coming from suspicious sources.
Start your journey towards identifying and blocking fake senders using your domain: Set up Valimail Monitor. It’s free, takes five minutes, and has zero impact on your email flow.
Frequently asked questions about fake email sender identity
Can somebody really send a fake email from my domain?
Yes, if your domain lacks DMARC enforcement, anyone can use a fake mailer to send from a fake email address that appears to come from you. This is how many phishing and impersonation attacks start.
What’s the difference between spoofing and a fake email sender?
Email spoofing is the broader tactic of forging headers to mislead recipients. A fake email sender specifically targets the “From” field, making the email look like it came from a trusted person or brand.
How can I stop fake email sending from my domain
Use email authentication standards like SPF, DKIM, and DMARC and enforce a DMARC policy of quarantine or reject. If you need help, Valimail can help your domain reach enforcement safely and quickly.