Even though email authentication protocols have proven effective, some still have concerns about the integrity of emails passing through DKIM validation systems.
These email authentication protocols, SPF, DKIM, and DMARC, play a crucial role in preventing sender spoofing, a technique often exploited by malicious actors to make phishing emails appear as if they originate from trusted sources.
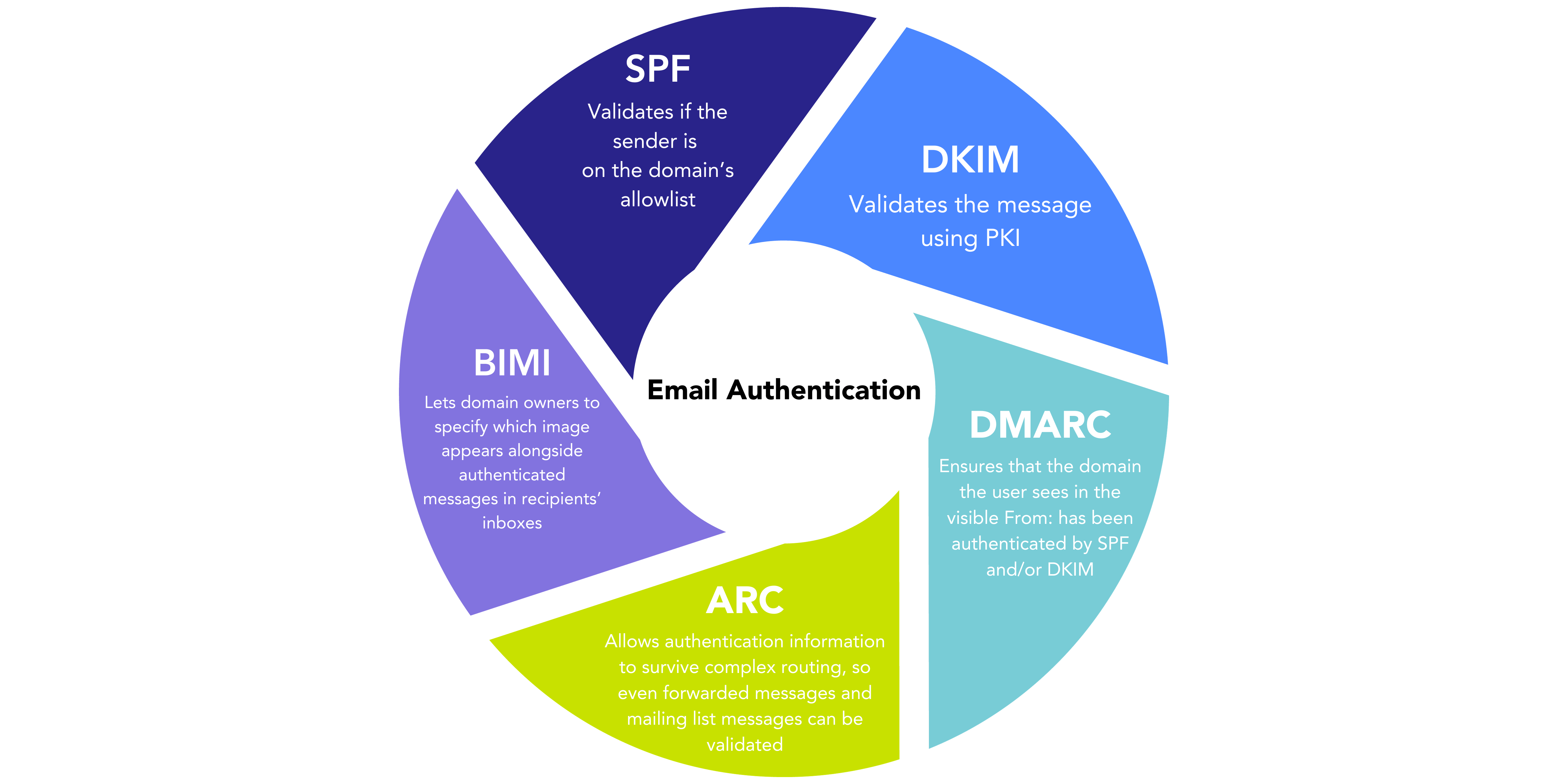
Domain spoofing, which is a common method employed by phishers, poses a significant threat in the absence of authentication measures. It allows cybercriminals to craft convincing phishing emails that can easily deceive recipients.
Despite recent claims regarding vulnerabilities in DKIM, it’s essential to put these concerns into perspective. Below, we’re going to debunk some of these fears and myths and give you the truth about DKIM’s vulnerabilities (and lack thereof).
Debunking DKIM vulnerabilities
1. Reusing DKIM-signed headers
The first supposed vulnerability is the possibility of inserting multiple Subject and other headers, giving an attacker the ability to reuse a DKIM-signed set of legitimate headers but have the mail include as alternate versions of these headers.
Even if successfully exploited, for almost all headers this simply has the effect of causing the message to display improperly—not very useful to an attacker.
The one header that may be hypothetically displayed to the recipient is an altered Subject. That’s more significant, but still of limited utility to an attacker.
But in practice, even this exploit isn’t much of an issue. Users might test this with an email client that has a very small user base. But that client may not be in the top 10 email clients worldwide.
Another mistake might be not using the DKIM signature result from Gmail. Modern mail services like Gmail, Office 365, and others are aware of these kinds of issues. So when they detect multiple Subject headers, they may fail authentication of the message, redirect it to spam, display a warning, or take other actions.
Moreover, if a sender is really concerned about this kind of edge-case exploit, and is concerned that the receiver will not be sophisticated enough to address it, the DKIM RFC provides clear guidance on how to use over signing to prevent this issue at the source.
2. Misusing optional attributes
A second potential vulnerability on the use of the optional “l” (lowercase L, for “length”) attribute in the DKIM signature, which can be used to limit how much of the message body is signed.
The l attribute is a vestige of an earlier era in Internet email when the majority of messages were short and text-only. The l attribute was meant as a way of allowing messages to pass DKIM authentication even if a forwarder or other service had appended a footer, which was once common practice.
Even the authors of the DKIM standard recognized that the l attribute was a risky and not particularly effective way to solve that problem.
As a result, almost no senders today use the attribute, and email best practices advise against it.
Those few senders that do use it should eliminate it, because they risk accidental authentication failure.
3. Errors during encoding translation
Finally, DKIM occasionally breaks when mail systems translate 8BITMIME-encoded messages into 7-bit ASCII. As he observes, this is only occasionally a problem, and only when such messages transit servers that don’t support 8-bit MIME, such as 1&1 or AOL.
It’s important to note that this issue (affecting a very small number of messages) isn’t a vulnerability of any kind— it’s just a case where DKIM signatures should pass, but may fail.
There are a few other such edge-case situations as well, and while they are unfortunate, they don’t impact the overall reliability of DKIM and related email authentication protocols.
Invest in email authentication
In reality, there are a few legitimate, real-world operational issues with DKIM, all of which the email industry has been aware of for some time and has been addressing.
However, there isn’t a workable vector that an attacker could actually exploit. The best protection for your domain is following best practices for SPF, DKIM, and DMARC.
Utilizing all three of these protocols will secure your domain and make it impossible for bad actors to spoof your emails. The first step is making sure you know who’s sending as your domain.
Our Monitor product gives you free visibility into your domain so that you can take the necessary precautions to protect it.


