DMARC (Domain-based Message Authentication, Reporting, and Conformance) is the protocol that keeps bad actors from impersonating your brand. However, setting up DMARC isn’t as simple as downloading an ad blocker; it’s got a bit more complexity and nuance to it.
And most of that complexity (and powers) centers around your DMARC syntax.
DMARC syntax is the strange-looking string of characters that defines your DMARC policy and enforcement status. Get it right, and your email program will be safe and secure. Get it wrong, and your email domain’s door will be wide open for attackers.
Whether you’re an email expert or newcomer, we’ve got you covered. Below, we’ll break down every element of your DMARC syntax, look at common examples, and provide you with the know-how to craft a DMARC record that’s effective and error-free.
The basics of DMARC syntax
Your DMARC record is a set of instructions for email servers. It tells them how to handle emails claiming to be from your domain. This record lives in your domain’s DNS (Domain Name System). It’s a TXT record with a special name: _dmarc.yourdomain.com.
When an email server receives a message claiming to be from your domain, it looks up this record to see how it should treat the email.
A DMARC record might look intimidating at first glance, but it follows a consistent pattern:
v=DMARC1; p=reject; rua=mailto:dmarc-reports@yourdomain.comLet’s break this down:
- It always starts with “v=DMARC1”. This is like saying “Hello, I’m a DMARC record” to any server that reads it.
- The record is made up of tags and values, separated by semicolons. In our example, “p=reject” and “rua=mailto:dmarc-reports@yourdomain.com” are two separate tag-value pairs.
- Each tag is a single letter or short abbreviation, followed by an equals sign and its value.
Think of it as a very condensed set of instructions. Each tag tells email servers something specific about how to handle your emails or where to send reports about what’s happening with your domain.
Breaking down the DMARC record (tag by tag)
Lets break down each element of the DMARC record so that you understand what every tag means (and how to use it). For starters, know that you don’t need to use all of these tags in every DMARC record. Start simple and add complexity as needed.
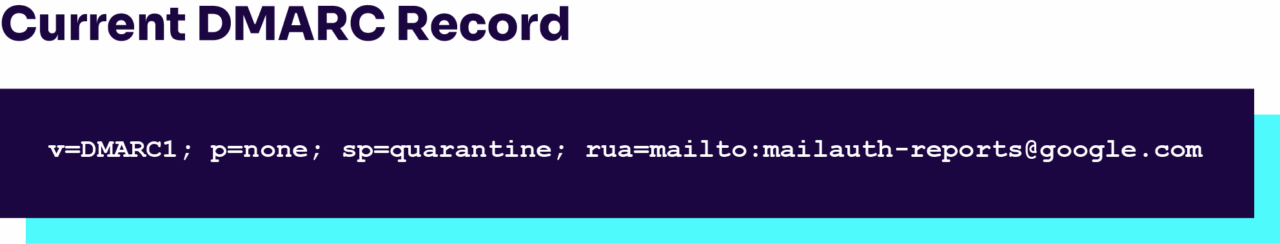
- Version tag (v=): This is always “v=DMARC1.”
- Policy tag (p=): It tells receiving servers what to do with emails that fail DMARC checks. You’ve got three options:
- p=none: Useful for monitoring without taking action.
- p=quarantine: Sends questionable emails to spam.
- p=reject: Flat-out rejects failed emails.
- Subdomain policy tag (sp=): Like the policy tag, but for your subdomains. If you don’t set this, subdomains inherit the main policy.
- Percentage tag (pct=): This lets you apply your policy to only a portion of your email. “pct=100” means apply to all email, while “pct=50” means only half.
- Reporting format tag (rf=): This specifies the reporting format you want to receive. The default is “rf=afrf” (Aggregate Failure Reporting Format).
- Reporting interval tag (ri=): How often do you want reports? This tag sets the reporting interval in seconds. The default is 86400 (daily).
- Failure reporting options tag (fo=): This tells receivers when to generate a failure report. Options include:
- 0: Generate a report if all mechanisms fail
- 1: Generate a report if any mechanisms fail
- d: Generate a report if DKIM signature fails
- s: Generate a report if SPF fails
- Aggregate report email tag (rua=): Where should aggregate reports be sent? Use “mailto:email@domain.com” format.
- Forensic report email tag (ruf=): Similar to rua, but for detailed forensic reports about specific failures.
- DKIM alignment tag (adkim=): How strict should DKIM alignment be? “r” for relaxed (default) or “s” for strict.
- SPF alignment tag (aspf=): How strict should SPF alignment be? Again, “r” for relaxed (default) or “s” for strict.
Common DMARC syntax examples
Now that we’ve broken down the individual tags, let’s see how they come together in real-world scenarios. Think of these examples as recipes: You can follow them exactly or use them as a starting point for your own DMARC record.
Basic DMARC record
v=DMARC1; p=none;=mailto:dmarc-reports@yourdomain.comThis is the simplest DMARC record you can have. It just starts monitoring sending behavior and receiving reports, but it takes no action yet. It’s perfect for dipping your toes in the DMARC waters.
Monitoring mode DMARC record
v=DMARC1; p=none; rua=mailto:dmarc-reports@yourdomain.com; ruf=mailto:forensic-reports@yourdomain.com; fo=1This record is still in monitoring mode, but it’s collecting more detailed information. The “fo=1” tag asks for forensic reports on any authentication failure, giving you a clearer picture of potential issues.
Strict enforcement DMARC record
v=DMARC1; p=reject; pct=100; rua=mailto:dmarc-reports@yourdomain.comThis record tells receivers to reject all emails that fail DMARC checks. The “pct=100” isn’t strictly necessary (it’s the default), but it emphasizes that this policy applies to all your email.
Complex DMARC record with multiple tags
v=DMARC1; p=quarantine; sp=reject; adkim=s; aspf=s; pct=100; rua=mailto:dmarc-reports@yourdomain.com; ruf=mailto:forensic-reports@yourdomain.com; fo=1; ri=86400Let’s break it down:
- Main domain policy is quarantine, but subdomains are set to reject
- Both DKIM and SPF alignment are set to strict
- The policy applies to 100% of emails
- It’s collecting both aggregate and forensic reports
- Forensic reports are generated for any authentication failure
- Reports are sent daily (every 86400 seconds)
Remember, more complex isn’t always better. Start simple and add complexity as you become more comfortable with DMARC and understand your specific needs.
DMARC syntax checkers and validators
Regardless of your DMARC experience, it’s always smart to double-check your implementation. That’s where DMARC syntax checkers and validators come in handy. These tools are like spell-checkers for your DMARC record, guaranteeing you haven’t made any typos or logical errors that could compromise your email security. They can:
- Catch syntax errors before they cause problems
- Verify that your DMARC record is correctly formatted
- Provide suggestions for improving your DMARC implementation
We have a free DMARC Checker you can use to validate and analyze your DMARC setup. Here’s how it helps:
- User-friendly interface: Simply enter your domain name, and the tool does the rest.
- Comprehensive analysis: It doesn’t just check syntax; it provides a full DMARC status report.
- Clear explanations: The tool breaks down each element of your DMARC record and explains what it means.
- Actionable insights: If there are issues with your DMARC setup, the checker provides clear guidance on how to fix them.
- Additional checks: Beyond DMARC, it also checks your SPF and DKIM configurations, giving you a holistic view of your email authentication setup.
The tool will show you your current DMARC record (if one exists), explain what each tag means, and highlight any issues or areas for improvement. It’s an invaluable resource whether you’re setting up DMARC for the first time or fine-tuning an existing configuration.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Your Domain
Not protected AGAINST IMPERSONATION ATTACKS
DMARC NOT AT ENFORCEMENT
exampledomain1.com
Authentication Status for January 10, 2025
DMARC at Enforcement
SPF Record Configured
BIMI Ready
exampledomain1.com
Authentication Status for January 10, 2025
DMARC at Enforcement
SPF Record Configured
BIMI Ready
How to troubleshoot invalid DMARC syntax
Even the most careful DMARC setup can sometimes go wrong. Here are a few common DMARC syntax errors and how to fix them:
- Missing required tags: The most frequent error is forgetting essential tags. Remember, every DMARC record must include:
- v=DMARC1 (version)
- p= (policy)
Always double-check that these tags are present and correctly formatted.
- Incorrect tag ordering: While most tags can appear in any order, the “v” tag must always come first. Double-check that “v=DMARC1” is at the beginning of your record.
- Invalid policy values: The “p” tag only accepts three values: none, quarantine, or reject. Check your policy tag. If it’s not one of these three, it’s incorrect.
- Malformed email addresses: In “rua” and “ruf” tags, email addresses must be properly formatted and preceded by “mailto:”. Confirm your email addresses look like this: mailto:dmarc-reports@yourdomain.com
- Invalid percentage values: The “pct” tag only accepts whole numbers from 0 to 100. If you’ve used decimals or numbers outside this range, adjust accordingly.
And this isn’t just a one-time practice. DNS entries can sometimes become corrupted, email sending practices might change, and new DMARC tags (or best practices) might evolve. You’ll need to regularly monitor and check your DMARC records to guarantee they’re performing as intended. Set a reminder to check your DMARC syntax monthly or quarterly. It’s a small time investment that can prevent big email delivery headaches down the road.
Best practices for DMARC syntax
Mastering DMARC syntax is like learning to play chess—sure, the rules are straightforward, but strategy makes all the difference. Let’s explore some best practices to keep your DMARC implementation robust and effective.
Keep it simple to start
When you’re just beginning with DMARC, resist the urge to use every tag in the toolkit. Start with a basic record:
v=DMARC1; p=none; rua=mailto:dmarc-reports@yourdomain.com
This simple setup allows you to monitor your email ecosystem without impacting delivery. As you gain confidence and insights, you can gradually increase complexity.
Regularly review and update your DMARC record
Your DMARC record isn’t a “set and forget” solution. Treat it like a living document that evolves with your email practices. Here’s a good review routine:
- Monthly: Check your DMARC reports. Are you seeing unexpected failures? It might be time to adjust your record.
- Quarterly: Perform a full DMARC health check. Are all your legitimate email sources properly authenticated?
- Annually: Reassess your DMARC policy. Can you move from “p=none” to “p=quarantine” or “p=reject”?
Remember, as your business grows and changes, so should your DMARC implementation.
Use a DMARC management platform for complex deployments
For larger organizations with multiple domains and complex email setups, managing DMARC manually can become overwhelming. A DMARC management platform like Valimail can help by:
- Automating report collection and analysis
- Providing clear visualizations of your email authentication status
- Offering guided remediation for authentication issues
- Simplifying DMARC record updates across multiple domains
While these platforms aren’t necessary for everyone, they can be a game-changer for complex email environments.
Align your DMARC strategy with your business needs
Your DMARC syntax should reflect your specific business requirements. Consider:
- How critical is email to your operations?
- What’s your risk tolerance for email-based attacks?
- Do you have the resources to handle potential customer inquiries if legitimate emails are blocked?
These factors should guide decisions like how quickly to move to stricter policies or whether to use features like the “pct” tag to gradually roll out changes.
Don’t forget about subdomains
Many organizations focus on their main domain but neglect subdomains. Remember the “sp” tag:
v=DMARC1; p=reject; sp=reject; ...This guarantees that your subdomains are protected even if someone forgets to set up DMARC for them specifically.
Get your DMARC syntax right (every time) with Valimail
Hopefully, you understand the basic structure of DMARC syntax now, but that doesn’t mean you need to become an overnight email expert. DMARC is powerful, but it can be complex, especially as your email ecosystem grows and evolves.
Fortunately, we can help. Valimail isn’t just another email solution—we’re the trusted partner that makes your DMARC manageable (and effective), regardless of how complex your email environment becomes:
- Expertise: We invented hosted DMARC in 2015. When it comes to email authentication, we don’t just follow best practices—we help create them.
- Automation: Our platform automates the heavy lifting of DMARC implementation and management, saving you time and reducing the risk of human error.
- Visibility: Get clear, actionable insights into your email ecosystem with our intuitive dashboards and reports.
- Scalability: Whether you’re managing one domain or thousands, Valimail grows with you to maintain consistent protection across your organization.
In the world of email security, you’re only as strong as your weakest link. Make sure your DMARC syntax isn’t it—get started with Valimail today.



