This post is an excerpt from the Valimail research report, 2020 Election Infrastructure Remains Vulnerable to Email Hacking, which was released last week — receiving coverage on NPR and elsewhere.
U.S. elections happen largely at the local level, with elections administered by local boards of elections or registrars of voters. Those elections are usually conducted with voting and tabulation equipment sourced from a small number of manufacturers whose technologies have been vetted and approved by the Election Assistance Commission.
To check the email security of these organizations, Valimail compiled two lists. One represents domains used by the three most populous counties in every state, a list of 187 domains that we last examined almost a year ago, noting that email security remains a weak link in election infrastructure. The second is a list of domains used by the eight election systems manufacturers approved by the EAC.
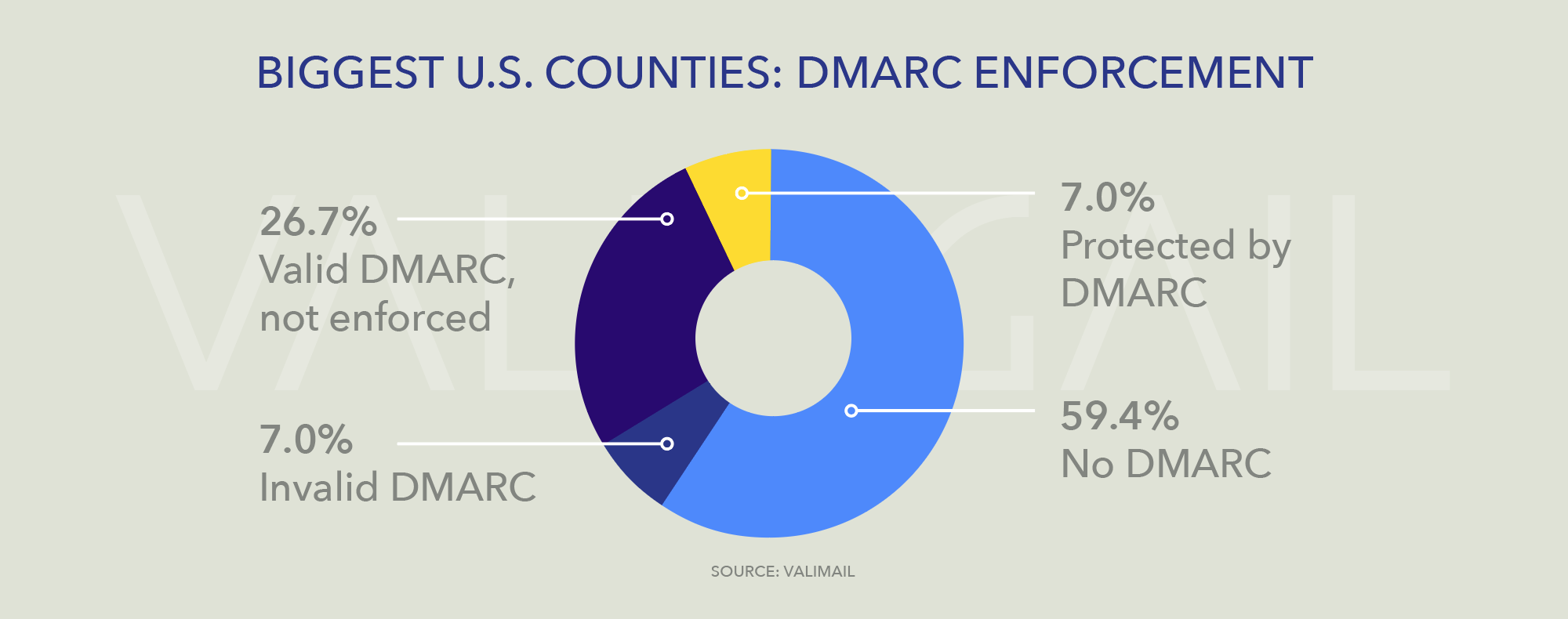
For the top counties in the U.S., the picture is only slightly better than we found in 2019. Today, 7% of the country’s largest counties are protected by DMARC that is properly configured and set to a DMARC enforcement policy of p=reject or p=quarantine, up from 5% in December 2019. Almost 27% have DMARC records but have set them to an unenforced, p=none policy, which does nothing to stop email impersonating them from being delivered. And the rest, 111 counties — 59.4% of the total — have no DMARC records at all.
SPF usage among these counties is at a higher level than among state domains, perhaps reflecting the fact that these domains are more heavily used for sending email to local citizens. 67.4% of these domains have valid SPF records, and 24.6% have no SPF at all. Having a valid SPF record published in DNS can help improve deliverability of the emails a domain does send, but it does nothing on its own to protect the domain from being spoofed by imposters.
This lack of protection by DMARC is cause for concern, because it means that the vast majority of America’s largest counties can easily be impersonated by spammers or bad actors. Bogus voter registration notifications, impersonated communications from boards of elections, faked announcements of voting results — all are possibilities that could be executed by a careful adversary, leveraging the implicit trust people are likely to place in a message that appears to come from an official domain.
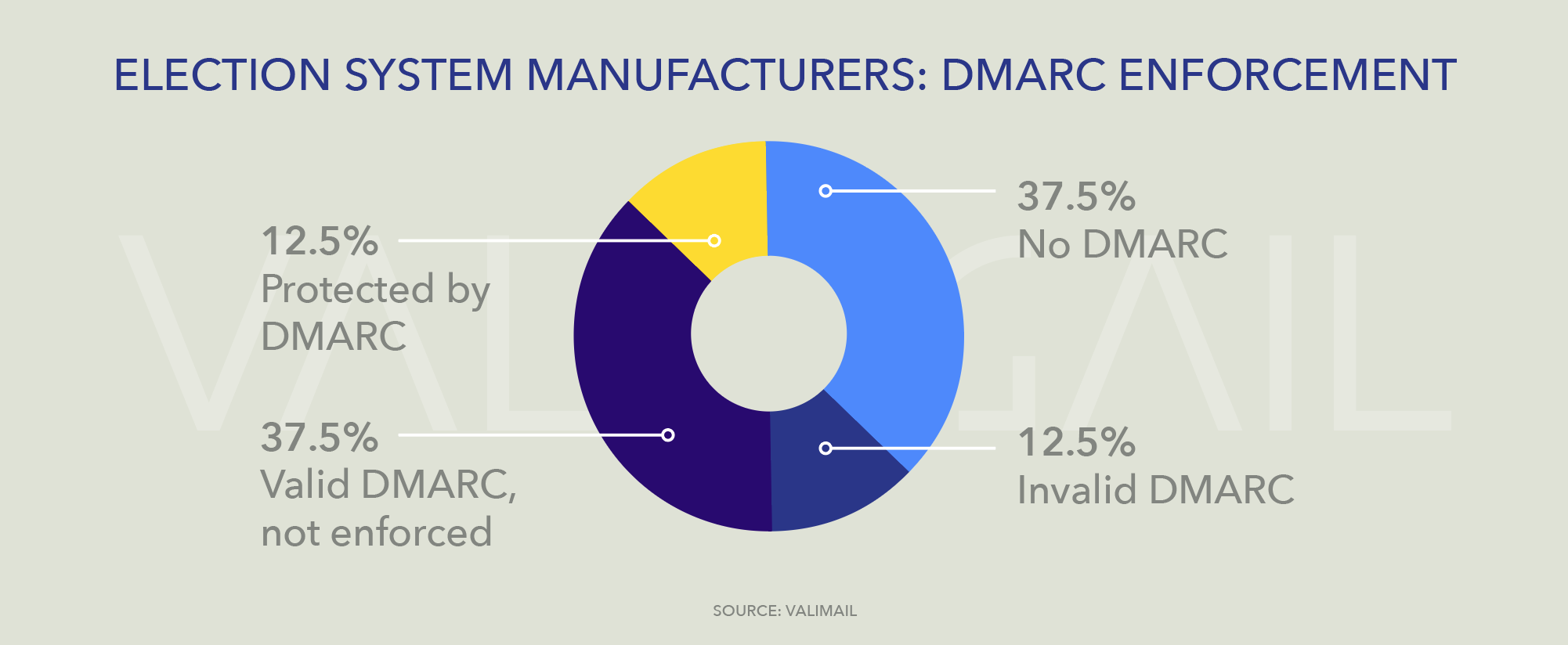
There is also cause for concern among the manufacturers of election equipment used throughout the country. Only one manufacturer, Smartmatic, has a domain that is protected from impersonation with a correctly configured DMARC record at enforcement. The rest can easily be spoofed.
Takeaways
It is not difficult to imagine a scenario in which attackers impersonate election officials, state governments, campaigns, or even election systems manufacturers, via spoofed domains, in order to spread disinformation, conduct voter misdirection or vote-suppression campaigns, or even to inject malware into government networks.
For this reason, Valimail urges all organizations involved in elections, from state and local boards of elections to manufacturers to campaigns, to configure their domains with DMARC at enforcement. This step is both feasible, effective, and inexpensive.
For instance, the U.S. Department of Homeland Security issued a directive in late 2017 (BOD 18-01), mandating that civilian executive branch agencies use DMARC at enforcement on all of their domains by early 2019. As a result, nearly 80% of the federal government’s domains are now protected from impersonation, according to Valimail’s research.
The American Bar Association recently called on the U.S. federal government to “empower the National Institute of Standards and Technology (NIST) to establish standards for election software, develop a certification process, and review the private sector role in election systems.” Valimail supports this call, and we would add that DMARC enforcement should be a requirement for all domains involved in elections, just as the DHS mandated it for executive branch agencies.
The U.S. Election Assistance Commission offers resources on improving election security, for voters and for election officials, which provides a wealth of useful, actionable information.
Governments and organizations that want to take the first step on their journey to DMARC enforcement can check the status of their domains using Valimail’s free, instant domain checker, at valimail.com. This will tell you exactly how your SPF and DMARC records are configured, and what needs to be fixed, if anything.
As a guide for getting started with DMARC, we also provide a free, 44-page Email Authentication Handbook, a detailed, step-by-step guide to implementing email authentication using SPF, DKIM, and DMARC.
DMARC enforcement is a crucial best practice for stopping the largest attack vector into any organization. The low rates of deployment of this open standard among domains involved in elections is a signal that best practices to protect democracy are missing in many key places. It is time to direct funding toward implementing such best practices, with DMARC at the top of the list, across state and local infrastructure.
As we wrote last year, the playbook on how to achieve that is well known, and funding is available. It’s past time to get it done.
