The who and what of email security
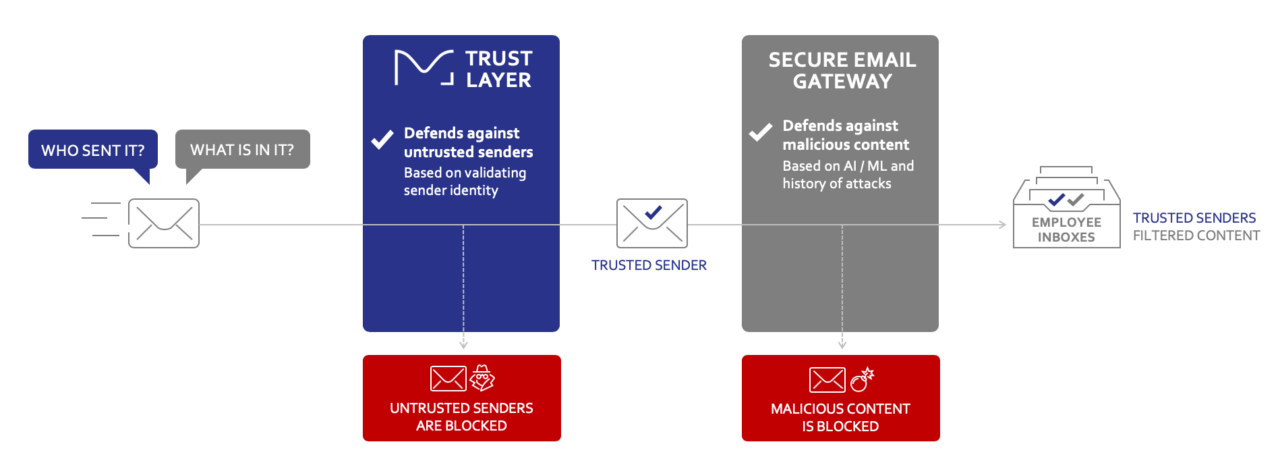
[Sassy_Social_Share] In the days of circuit-switched telephony, when Grandma dialed Grandpa, the phone company could easily determine that the caller’s identity was, in fact, Grandma. Such confidence melted away, however, with TCP/IP and the Internet. That is, when Kahn and Cerf decided to allow senders, instead of the network, to specify their identity, they created […]