Payment Confirmation Spam Emails
In the early 2010s, scammers developed a new spam email strategy. Cybercriminals started sending phishing emails claiming to be payment confirmations for services that the targets never ordered. The emails are intended to lure targets into attempting to cancel the service either by clicking on a phishing link or opening an attachment.
This kind of attack is called payment confirmation email scam, and it continues to be a real issue for online safety. Even if most users apply good defenses, the attack is spammed to so many targets that the attackers only need a small percentage to fall for it. Worse yet, the recipients of the spam emails are not the only victims: The businesses that these attackers impersonate also suffer from the loss of trust that the attacks create.
When someone reads that they have been charged for something – especially if it is unfamiliar – they are prone to panic. Scammers prey on the desperation that this kind of phishing attempt inspires in the recipient. That is why these attacks work: Increased anxiety may inhibit your better judgment. How effectively do scammers employ their manipulation tactics? According to the IC3’s Annual Crime Report, over $44 million USD was lost to phishing scams in 2021 alone (source).
Of course, the cybersecurity community has developed remediations and preventative measures in the years since this attack burst onto the scene. In this article, we present the accrued wisdom about recognizing payment confirmation email scam and defending against it. We provide instructions for individuals to notice red flags and show how businesses can help mitigate impersonation so that their reputations are less likely to be abused to attack their customers.
Identifying email confirmation phishing
Below are some quick tips for flagging scams and discerning legitimate payment confirmations from malicious scams.
| Red flag | How it works |
|---|---|
| Charge not recorded in bank account | Check with the bank: Did you order something by accident, or is someone actually making fraudulent charges against your account? |
| Odd attachment file extensions | The most popular of these scams often send fake PDFs that are really HTML files with the extension .pdf.html. |
| Unofficial domain name | The email wants you to click a link to a domain other than the service’s official domain, or the email originates from a domain that looks different than the service’s normal one. |
| Sketchy content | Spelling mistakes or inconsistent formatting should make you question an email’s legitimacy. |
| Attachment protected with your account password | Often, the attack will include a file that asks for your account password before opening. |
Understanding the attack
When spammers send out phishing emails, they want to entice recipients into performing an action that benefits the spammers. In the case of payment confirmation email scam, the attackers scare you into thinking you have been charged for a service you did not intend to purchase, so you will take action that will help the spammers, like compromising your login information.
To gain a more concrete understanding of this, let’s look at some of these attacks as they have occurred in the real world.
Case studies from the wild
On September 10, 2021, the University of Minnesota announced that its students and faculty were receiving a barrage of fake payment receipt spam emails.
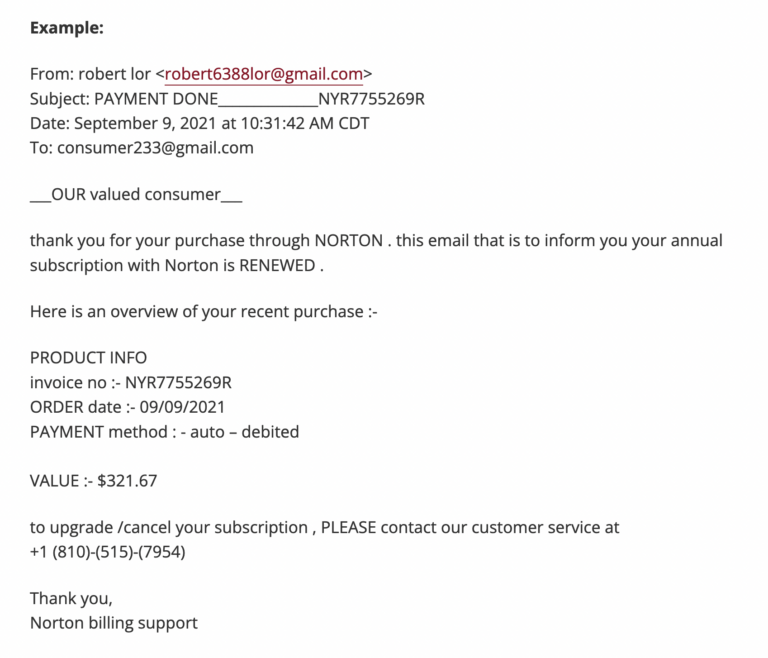
Here, we see a fairly unsophisticated version of this attack. The email claims to come from Norton, a well-known anti-malware program, yet the visible origin of the email is a Gmail address. In response, the university’s advisory gives great advice:
- Do not reply, click the link(s), call the phone number, or log in (if you do click the link).
- Report it as spam to Google.
- Forward the notice to phishing@umn.edu.
- Check your bank statement to confirm whether the charges are real or not.
- For more information, please see: How to Manage Spam Emails
Platform | Success Rate | Success Rate Frame | Estimated FTEs | Maintenance | Marketplace Apps Identified |
|---|---|---|---|---|---|
DIY Manual | 20% | 12+ Months | 2-3 | Never ending | ~100 services |
Outsourced Manual | <40% | 9-12 Months | 1-2 | Never ending | ~100 services |
Valimail Automation | 97.8% | 0-4 Months | 0.2 | Automated | 6,500+ |
We’ll explore these defenses and others shortly. For now, we can look at a similar attack that also affected a college, this time the University of Vermont.
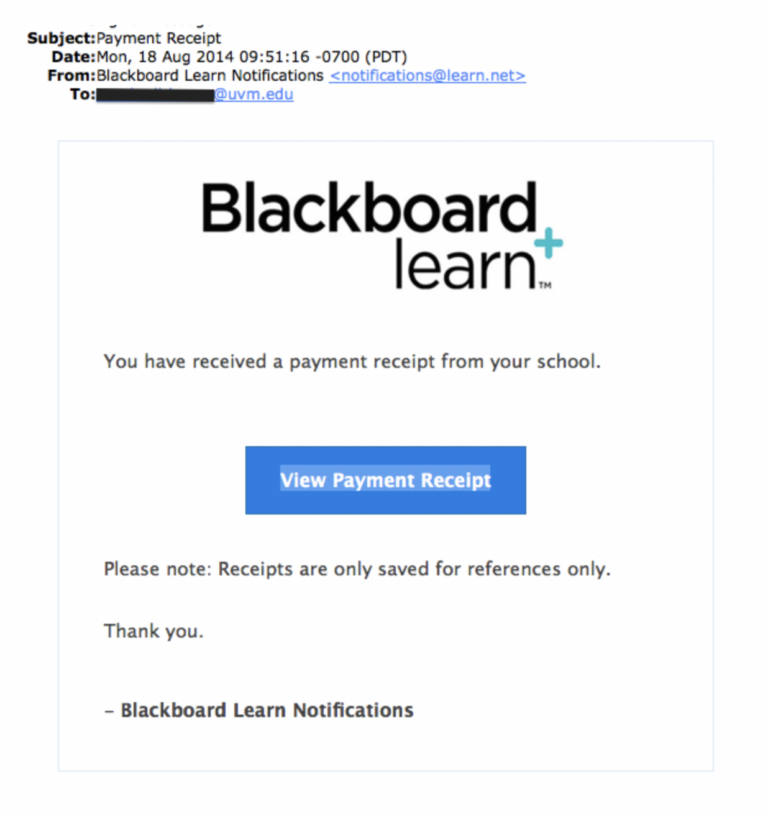
This attack takes the trickiness up a notch compared to the previous example in three ways:
- It forges a legitimate-seeming business domain (rather than using a Gmail address).
- It uses graphics and formatting to appear more professional and thus trustworthy.
- It links to a phishing document controlled by the attackers.
This attack also changes the approach by making the recipient believe they have received money, lowering their defenses by manipulating hope instead of fear.
Countless other variations of this attack have been documented online, but these two examples should give a general picture of the kinds of tactics typically employed.
Recommendations
Awareness is important, but what really matters is prevention. Let’s look at some ways that you can prevent, or at least mitigate, the threat of payment confirmation email scam.
DMARC and BIMI
DMARC is a protocol that powers authentication in email to make it harder for attackers to forge the visible From: address of an email. You should protect all your domains with DMARC and also enable DMARC on incoming mail so you can tell when From: addresses are forged. You can learn more about DMARC with our guide: A step-by-step guide to getting DMARC done right.
Brand Indicators for Message Identification (BIMI) allows a brand owner to capitalize on the work they’ve done to protect their domain with DMARC by choosing a logo to display next to their emails. A logo makes your email stand out in the recipient’s inbox and gives them confidence that it’s mail that they want. Tools like Valimail Amplify even make BIMI readiness quick and easy.
General anti-phishing best practices
Although payment confirmation spam has its own quirks, the best defenses against most kinds of phishing also apply to this attack:
- Look for sloppy content and basic mistakes in spelling, grammar, and language.
- Make sure the email originates from an official domain.
- Enforce email security best practices.
- Conduct internal phishing campaigns to find weak spots and educate workers.
- Never interact with suspicious content (e.g., by opening links or downloading attachments).
- Implement security in layers so that even if an attack occurs, your organization still has some protection.
- Mandate multi-factor authentication and the use of password managers whenever possible.
Sophisticated phishing can be hard to beat, but with basic security hygiene and general phishing awareness, you can be a lot safer.
What if I suspect an attack?
If you receive a confirmation email for an order that you suspect may be a phishing attempt, the first step is to determine if the order is real. If it is not, you will want to tip off the relevant team in your organization. Follow this simple process for handling suspected payment confirmation email scam.
- Determine if the payment might be real (either the result of fraud or an accident):
- Consult your financial institution to verify that the charge isn’t real.
- You may also want to let your bank know to reject the charge if it does come through.
- Once you’ve confirmed that the email is spam, flag it;
- Report it to your mail client, if possible.
- Forward it to your organization’s security leadership.
- Do not respond to the email itself, click on links, or open attachments.
These attacks often aim for strategic targets throughout an organization, so you can help defend your entire organization by increasing awareness quickly.
Summary of key points
We hope the information above has equipped you with the requisite understanding to thwart this attack. Payment confirmation email scam is nefarious, but equipping yourself and your team with the right defenses makes it possible to remain unscathed.
Let’s briefly go over the key techniques we learned about above:
- Examine all emails for signs of phishing.
- Use and enforce DMARC and BIMI.
- Communicate to security leadership if you identify a suspicious email.
- Practice good cybersecurity hygiene, such as using multi-factor authentication and a password manager.
Hopefully this article becomes a resource that you can consult and reference whenever the topic of this attack vector comes up. Good luck, and stay safe!
