Phishing Prevention Best Practices: How to Detect & Avoid
Phishing prevention best practices aren’t nice-to-haves—they are need-to-haves.
In an era defined by bigger and bigger cybersecurity attacks, phishing is a major business risk. According to a report from CyberTalk about phishing attacks in 2022,
“Forty-two percent of workers self-reported having taken a dangerous action (clicked on an unknown link, downloaded a file, or exposed personal data) while online, failing to follow phishing prevention best practices.”
– CyberTalk report, Top 15 phishing attack statistics.
Phishing is becoming the preferred means for gaining a foothold into a target—both for ethical pentesters and malicious cybercriminals. There’s a good chance that most readers have spam emails in their inbox right now containing some kind of phishing link.
The risks go way beyond those old Nigerian Prince money scams from the 90s. That’s because attackers are using sophisticated social engineering techniques to plant complex malware in victims’ computers.
However, the situation is not completely bleak.
Just as hackers have ramped up the complexity of phishing techniques, security engineers have also been hard at work. Whether it’s DMARC, advanced phishing protection filters, or warning users when emails come from outside their domain, there are a variety of phishing prevention best practices that help you reduce risk.
We’ll help you learn key phishing prevention best practices that can help you prevent threat actors from gaining a foothold in your network.
Foundational Phishing Prevention Techniques
Before we get into the details, here’s a quick overview of the main phishing defenses we’ll explore in this article. Along with each strategy, there’s a simple definition. We’ll dive deeper into each of these phishing prevention techniques later in the article.
Summary of Phishing Defense Techniques
| Phishing Defense Technique | Description |
|---|---|
| Spot red flags | Signs of an illegitimate email such as poor spelling, fishy attachments, and an unusual domain. |
| Internal phishing campaigns | Conduct phishing exercises to train employees in how to avoid victimization by phishing attacks. |
| Mark external domains | Make it easier to notice when a domain comes from outside of the recipient’s domain. |
| Advanced phishing protection | Mail providers often offer special security protection using sophisticated threat detection. |
| DMARC | Protects your domain from others using it in phishing attacks. |
How Phishing Emails Work
To help put phishing defenses in context, let’s analyze how a realistic phishing attack works. Phishing is a cyberattack where threat actors use fraudulent messages — often email — to trick users.
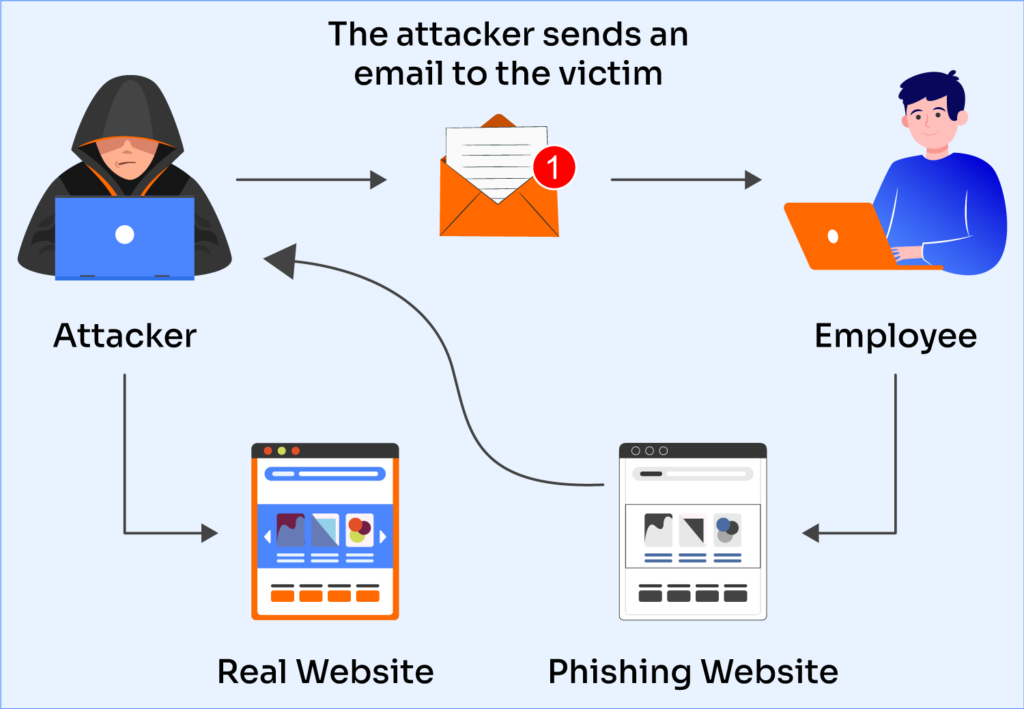
There’s no single template for what a phishing email looks like, but there are several common indicators of a phishing attack that can help detect them. The diagram below details a phishing attempt where the attacker sends the victim to a fake webpage to compromise sensitive data.
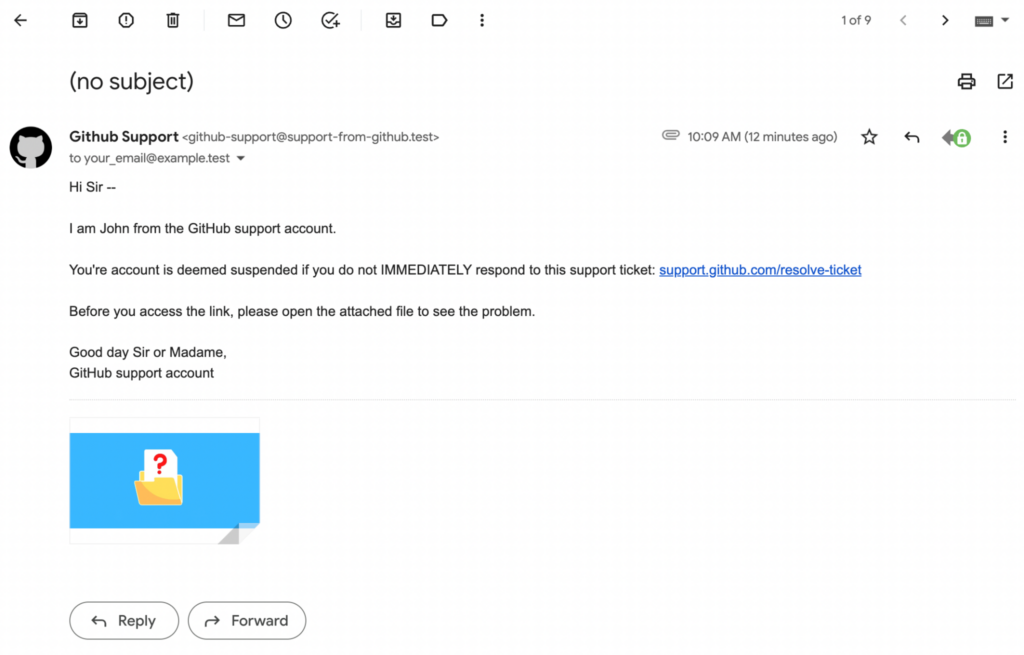
Now let’s dive into an example of a phishing email we can dissect and learn from. Here is a screenshot of a phishing email:
Perhaps you already see some signs of phishing. Of course, there’s much more to an attack than what we see on the surface. To show you what I mean, here are the raw email headers for the same email:
Did you catch any more red flags that something is wrong here? The email above has several signs that mean something might be wrong. Here we’ll go through each red flag and why it happens in the wild.
Typos and Odd Language
Although the sophistication of phishing attempts continues to increase, not every team is an advanced threat with nearly unlimited resources. Some attempts are lower effort. There are hackers all around the globe, and not all of them are fluent in English. Notice the use of unidiomatic language like “Dear Sir or Madame” in the email above, or the misspelling of the word “attached” (which appears in the email as “attachd”).
Platform | Success Rate | Success Rate Frame | Estimated FTEs | Maintenance | Marketplace Apps Identified |
|---|---|---|---|---|---|
DIY Manual | 20% | 12+ Months | 2-3 | Never ending | ~100 services |
Outsourced Manual | <40% | 9-12 Months | 1-2 | Never ending | ~100 services |
Valimail Automation | 97.8% | 0-4 Months | 0.2 | Automated | 6,500+ |
Incorrect Domain Name
Thanks to the widespread use of DMARC (more on that later!) to prevent impersonating a domain name, phishing attackers often must find different ways to make their email address’s domain name look more legitimate. So instead, they’ll use a domain that seems like it could be a domain owned by the supposed source of the message. Notice that in the message above, they do not use a real GitHub email address.
Malware Attachment
Phishing is the primary mechanism for malware delivery. It’s easy to spot obvious malware; for example, the phishing email above has an .exe file. However, a more realistic attack will be much sneakier. To give one possibility, sending a Microsoft Excel sheet that tricks the user into running code on their computer.
External Link
Of course, it’s not abnormal or even particularly suspicious for an email to include a link. However, due to the important role links tend to play in phishing attempts, you should treat the presence of external links as a sign to be on alert in case of phishing.
Phishing Prevention Best Practices
Now that we have an understanding of how attackers use phishing, let’s get into the most important part: how you can implement phishing prevention best practices to protect your organization from phishing attacks.
In this section, we’re going to go through the strategies outlined in the summary above in depth. Although phishing attacks can get pretty technical, the security industry has done a good job keeping up, and making it so even non-experts can implement these practices.
1. Spotting Typos and Grammar Issues
This is the simplest defense and the easiest to learn. Thanks to the early spam era of the 90s and early 2000s, even most non-technical people are generally familiar with these emails, and the knowledge has passed into folk wisdom.
The obvious signs to look for include:
- Misspellings
- Grammar mistakes
- Poor formatting
- Unusual language
Since most employees will already know that these are suspicious, the important thing to train them in is to not open the links or attachments in these emails. Sometimes, employees know an email is a likely phishing attempt, but think that they’re safe as long as they don’t send any confidential information or send money.
Opening links like these out of curiosity is common enough that this knowledge should form part of your company’s anti-phishing training.
2. Internal Phishing Campaigns
Do you know how you’d really fare during a phishing attack from malicious hackers? To find out, your best option is to organize a simulated phishing campaign. External auditors will do a full phishing campaign and let you know how your organization did and what you could do better.
If your security budget permits, this is a great way to stress test your anti-phishing defenses. However, it can be pricey. If that’s an issue, you’re in luck – the remaining best practices are much more affordable.
3. Mark External Domains
Whether you use a webmail interface or a desktop application like Thunderbird, most email software has a feature to warn you when an email comes from outside of your domain. This is particularly helpful for situations where the attacker tries to use a domain that looks nearly identical to your own organization’s domain, but with some tiny difference.
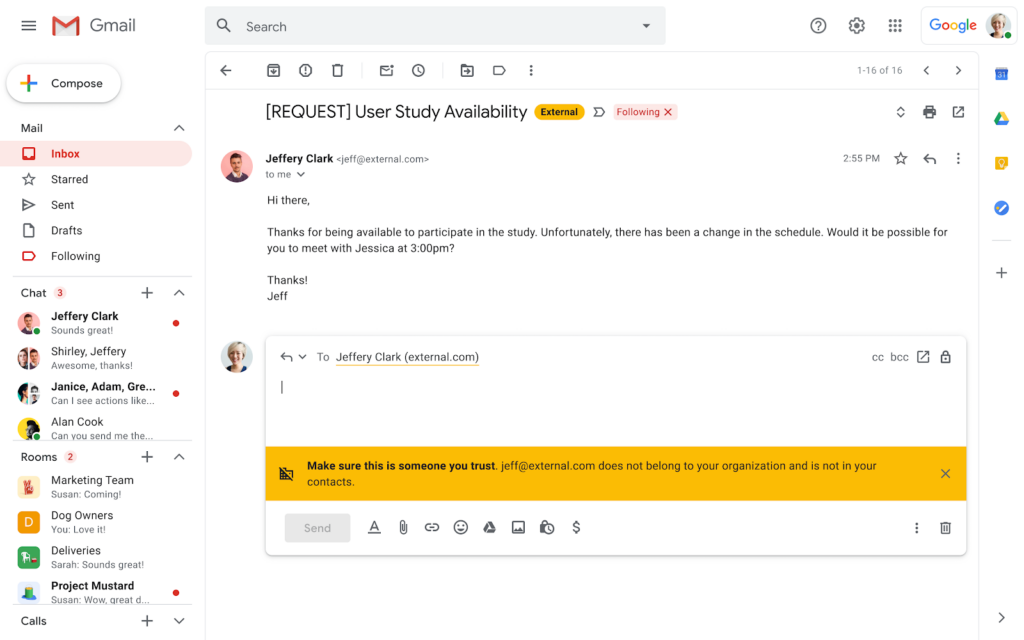
While that might get by a human, software isn’t so easily fooled.
4. Advanced Phishing Protection
If you use an established mail provider like Gmail or Office 365, then you have a huge advantage when it comes to advanced security features you can turn on that will help you detect phishy messages. Consult the list below to find instructions for doing this using the most popular mail providers:
Check out your provider’s security documentation to learn what options are available for you.
5. Digital Hygiene
Even if you do fall for a phishing attack, you can mitigate the damage by practicing good general cybersecurity practices. For example, multi-factor authentication (MFA) can make it harder for attackers to abuse stolen credentials. Separating your work and personal devices means that a phishing email that gets access to your gaming laptop won’t necessarily lead to a ransomware outbreak in your company.
There’s no simple solution for this, other than providing all employees within your organization with basic cybersecurity training. Additionally, the organization should enforce the lessons learned in this training by mandating good security practices.
6. DMARC
This best practice is a bit different. For example, it would not have helped prevent the phishing email we gave above. Rather, DMARC helps prevent other people from impersonating your domain. This matters for phishing because, if you enforce DMARC verification on incoming mail, you can discourage phishing attackers from pretending to be in your org by forging your domain.
Additionally, it’s a good practice for protecting your domain’s reputation from being trashed by abusers. Learn more about general email security best practices with our Email Security Best Practices guide.
7. Access Control and Privilege Management
Access control and privilege management are critical components of an organization’s cybersecurity strategy, especially in the context of phishing prevention.
These practices help ensure that employees have the appropriate level of access to resources and data needed to perform their jobs while minimizing the risk of unauthorized access and potential exploitation by attackers.
- Adhere to the principle of least privilege (PoLP), granting employees only the necessary access for their roles.
- Implement role-based access control (RBAC) and regularly review permissions to prevent overprivileged accounts.
- Enforce two-factor authentication (2FA) for privileged accounts and utilize privileged access management (PAM) tools for tight control over critical systems.
- Educate employees on access control’s importance and integrate it into incident response planning.
Prevent Phishing With DMARC
Hopefully, this guide has helped you understand the mechanics of a phishing attempt and how phishing prevention best practices can protect you from attacks. Even to organizations with excellent network security, regular pentests, and up-to-date tech, phishing can be extremely difficult to prevent.
Phishing is a particularly dangerous threat because it combines sophisticated technical innovation with complex social engineering. To properly protect yourself and your organization, good technical defenses must be combined with a vigilant security culture that equips everyone with the know-how to detect and fight phishing.
Some tactics, such as spotting red flags like typos and incorrect domain names, seem simple enough that a non-technical person sometimes can do this just using common sense and natural vigilance. Other defenses, like protecting your own domain from being used to phish with Valimail’s DMARC-as-a-Service technology, are more sophisticated and rely on more state-of-the-art technology to protect you. Nevertheless, a full security strategy means taking a holistic approach that takes advantage of all of the protections available.
As phishing attacks continue to grow in prevalence as well as sophistication, these practices can be the difference between surviving an attempted attack versus going under after a brutal ransomware siege.



