- Guide
Spear Phishing vs. Phishing: Differences & Mitigations
In the mid-90s, with the rise of the Internet came the rise of phishing. The Internet enabled new digital communication methods like email and attracted many users. Unfortunately, it also attracted malicious attackers who started tricking legitimate users into disclosing their passwords.
Similarly, the 2010s saw social media explode in popularity. Around the same time, a variant of phishing attacks known as spear phishing became common.
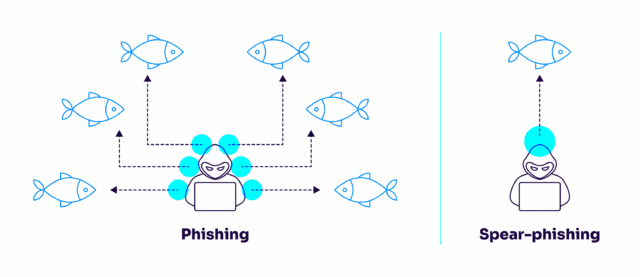
Fundamentally, the difference between spear phishing vs. phishing is targeting. Phishing attacks are broad and generic, while spear phishing targets specific people or organizations. From the attacker’s perspective, phishing is a “spray-and-pray” low-effort attack with a low probability of success against any given user. On the other hand, spear phishing takes more work but is more likely to succeed against a specific target.
Because humans often remain the weakest link in cybersecurity, these attacks remain popular among threat actors well into the 2020s. In fact, according to Verizon’s 2022 Data Breach Investigations Report, the leading cause of data breaches is phishing(both bulk phishing and spear phishing).
This article will take a closer look at spear phishing vs. phishing, explore mitigation techniques to help organizations reduce risk, and describe the steps you can take if you fall victim to a phishing attack.
Spear Phishing Vs. Phishing: Differences and Similarities
The table below details the key similarities and differences of phishing vs. spear phishing.
Spear Phishing Vs. Phishing
| Phishing | Overlap | Spear phishing |
|---|---|---|
| Multiple emails spammed to unknown recipients. | Try to obtain valuable information from the victim. | Few emails sent to specific persons or groups of people. |
| Does not require target research. | Writing style involves urgency or scarcity. | Requires target research. |
| Quick to deploy. | Impersonate someone else. | Takes time to pull off. |
| Impersonates banks, services, or very unlikely senders. | The most common channel is email. | Impersonates people the target would know or believe. |
| Poor grammar and multiple typos make it easier to spot. | Well written, making it more challenging to detect. |
What is Phishing?
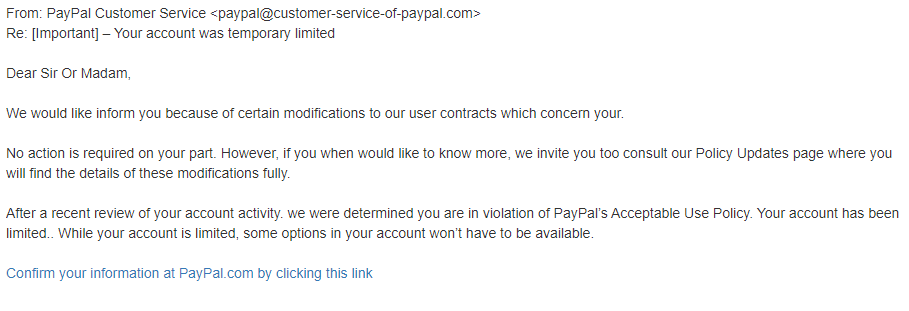
Phishing is a type of cyberattack that uses email to deceive victims into performing an unwanted action. These actions commonly involve clicking a suspicious hyperlink or disclosing personal information. Regular phishing is sent in bulk to unknown targets, with no personalization, hoping some of the recipients will be compromised.
Attackers do not invest much time or thought in bulk phishing attacks. They expect a low response rate, but at scale, that means there will be some victims who act on their request to disclose personal information.
Phishing emails are sometimes written in poor grammar, perhaps because the authors are often non-native speakers or sloppy writers. This aspect ought to tip sophisticated readers to their falsehood but leaves less sophisticated and inattentive recipients as common victims.
Phishing kits are a suite of tools that instantly deploy a web page and phishing script with little to no knowledge, making them attractive to inexperienced attackers. The fake web pages usually go for what are the most used services at any given moment, such as Facebook, Netflix, or clothing brands.
|
Platform
|
Success Rate
|
Success Rate Frame
|
Estimated FTEs
|
Maintenance
|
Marketplace Apps Identified
|
|---|---|---|---|---|---|
|
DIY Manual
|
20%
|
12+ Months
|
2-3
|
Never ending
|
~100 services
|
|
Outsourced Manual
|
<40%
|
9-12 Months
|
1-2
|
Never ending
|
~100 services
|
|
Valimail Automation
|
97.8%
|
0-4 Months
|
0.2
|
Automated
|
6,500+
|
What is Spear Phishing?
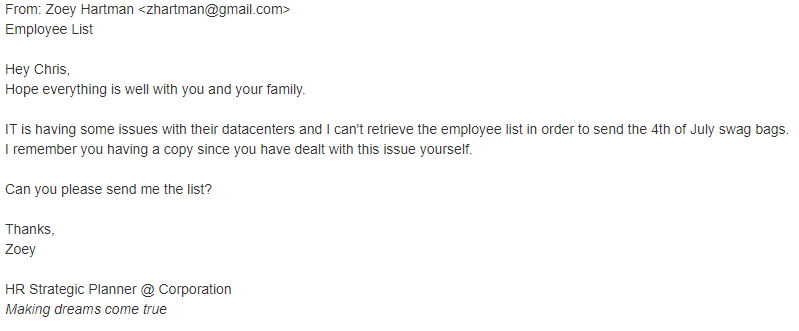
Spear phishing is a targeted phishing attack with content tailored to deceive specific individuals or organizations. Often spear phishing attacks target larger “prizes” such as business secrets or confidential information from a large enterprise. Orchestrated spear phishing attacks often use text messages, social media communication, and phone calls to increase their chances of success.
Research to gather intelligence about the victim is crucial to effective spear phishing. Attackers can often find personal information using OSINT (Open Source Intelligence), such as LinkedIn profiles, social media accounts, or company public pages.
Spear phishing emails are well written and try to look like legitimate emails. For example, these are common characteristics of spear phishing emails:
- Clear, sharp logo images of a reputable brand Logo pictures
- Appropriate greetings that aren’t generic
- Text that sounds organic, not suspicious.
What is Business Email Compromise (BEC)?
Business Email Compromise (BEC) is a specific type of spear phishing attack in which a cybercriminal impersonates a high-level executive and convinces the victim to transfer large sums of money or disclose trade secrets. BEC emails do not rely on malicious links or payloads. Instead, they rely on content targeted to manipulate an organization’s financial assets.
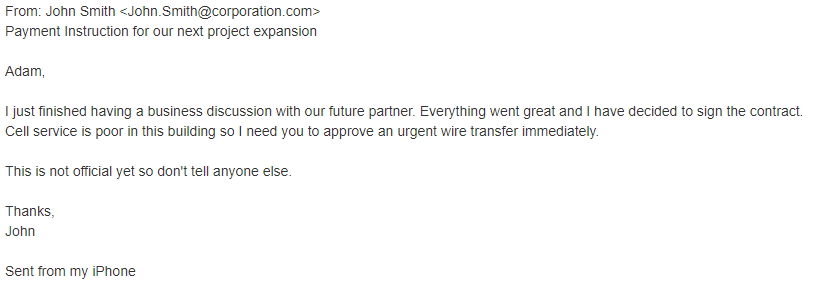
Stats on Phishing and BEC
To get an idea of how prevalent phishing and BEC are, let’s review some key takeaways from FBI’s 2021 Internet Crime 3 (IC3) Report:
- Phishing was the most common type of cybercrime
- The estimated losses generated by BEC account for almost $2.4 billion.
- Ransomware losses were 49 times lower than BEC
- Compared to 2020, BEC complaints increased by 3%, but the financial losses increased by nearly 30%
- Phishing affected about 300.000 victims, while BEC complaints total about 20.000
Mitigation Techniques for Phishing and Spear Phishing
Now that we’ve covered what phishing and spear phishing are, let’s take a look at how you can mitigate risk.
Perform User Training
Defense against phishing begins with training and user awareness to avoid common mistakes. Security awareness training programs help employees identify and report suspicious emails, and it works. According to the SANS 2022 Security Awareness Report, training frequency is the number one indicator of a successful security awareness program.
Since the employees are the first to interact with a spear phishing email, making them part of the organization’s security makes sense. These trainings help users better identify phishing threats and reduce their chances of becoming victims.
Test Users With Simulated Phishing Attacks
Effective user training should include phishing simulations that test a user’s ability to identify a phishing attack. Additionally, organizations should perform simulated spear phishing attacks against valuable resources. Because organizations are aware of current business situations and have up-to-date information about their employees, even spear-phishing simulations should be easy to set up.
Use Password Managers
A password manager helps you safely store all your credentials in one place. This tool encourages using strong, unique passwords for your accounts. With weak, reused passwords for multiple accounts, it’s only a matter of time until an attacker gets ahold of one of your passwords. Once that happens, they can compromise other accounts using the same password.
Enforce MFA Across Your Organization
Multi-factor authentication (MFA) secures login by requiring additional information besides a password, such as a code generated by a third-party app. Even if the attacker steals the login credentials, they will be useless without the token or PIN provided by the app.
Protect Your Domain With DMARC
Domain-based Message Authentication, Reporting, & Conformance (DMARC) can reduce the risk of an attacker spoofing your domain in an email. DMARC is an email authentication protocol. Having a DMARC record published discourages cyber criminals from trying to spoof emails from your organization. Email providers can publish a DMARC policy which informs the recipient server how to handle email which is not DMARC compliant.
When a domain owner publishes a DMARC policy, they are requesting specific handling for any message using their domain that does not pass DMARC validation checks. Handling sorts the received mail in one of the 3 following categories: none (treat the message no differently than if DMARC validation had not been performed), quarantine (route the message to the Spam folder) or reject (refuse to accept the message). DMARC accomplishes this by employing two other protocols: SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail).
DMARC validation is another layer of defense that aims to protect the inbox from phishing emails. If a network does DMARC validation on inbound mail and fulfills the domain owners’ requests to quarantine or reject mail that does not bypass DMARC validation exams, then many phishing emails might be prevented from reaching the end users’ inboxes.
Know Common Indicators of Bulk Phishing
Bulk phishing emails often have characteristics that make it clear they are not legitimate. Familiarizing yourself, and your users, with these characteristics can reduce your risk. Here are some of the most common characteristics of bulk phishing emails:
- Suspicious email addresses: Always check the email header for the “from” and “reply-to” information to confirm the actual sender address. Administrators can enable automatic verification to have a pop-up message alert the sender when emailing addresses outside the organization. For example, see how Google implements this.
- Unidiomatic greetings: Since most phishers are not fluent in English, they will use peculiar greetings such as “Dear Sir or Madam”, “Greetings of the day”, and “Good day to you”.
- Suspicious links: Do not rush to click a blue hyperlink. Instead, hover your mouse over the link to check the actual destination it points to.
- State of urgency: Attackers are aware of the human tendency to act quickly in urgent situations. Legitimate emails rarely use an urgent tone or hurry users into taking action.
- Typos: Generic phishing emails do not strive for perfect grammar or spelling and may even use poor writing as a filter to attract less sophisticated users.
- Offers that are “too good to be true”: Be suspicious of emails indicating you won — or could easily gain — something you did not expect. For example, a phishing email may attempt to entice action with a free smartphone, a large donation from a prince, or an inheritance from a long-lost relative. Offers like these are often too good to be true.
Be Wary of Unfamiliar Tones
Spear phishing attacks are more difficult to detect due to their targeting. However, a strange tone from a regular contact can be a spear phishing indicator.
A spear phishing email may be well crafted to bypass security systems, but it cannot know the relationship between the two parties. Understanding how people communicate or usually express themselves can be vital in detecting a spear phishing attempt. If the tone in a message from a known sender is questionable, call the sender to verify its legitimacy.

Minimal resource requirement with only a single one time DNS change needed

DMARC Enforcement guarantee and 97.8%+ success rate

100% Automated service discovery and 1-click validation
Use OSINT Tools to Protect Against Phishing
Many OSINT tools can help you improve your security posture. Below are some of the most popular OSINT tools to help you reduce your risk of falling victim to a phishing attack.
VirusTotal
VirusTotal can validate a suspicious URL from a potential phishing email. VirusTotal checks the URL against multiple databases provided by security vendors and returns a verdict. A “Phishing” or “Malicious” indicator should make you reconsider clicking the URL.

VirusTotal displays results for a phishing webpage.
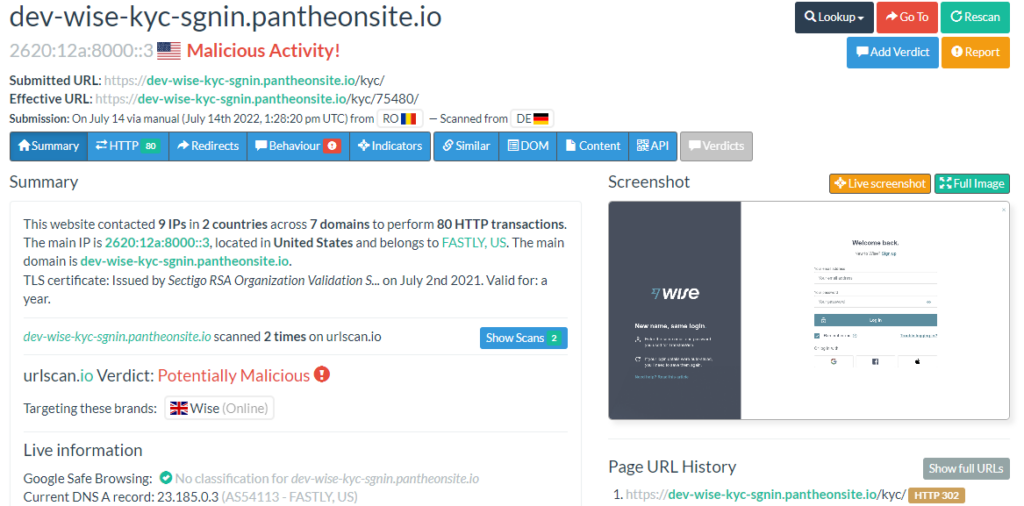
URLscan.io
URLscan.io is another helpful tool for scanning suspicious URLs. URLscan provides a snapshot of the webpage you check, displays the URL you will be redirected to, and points out what brand or service the phishing webpage is trying to mimic.
Haveibeenpwned.com
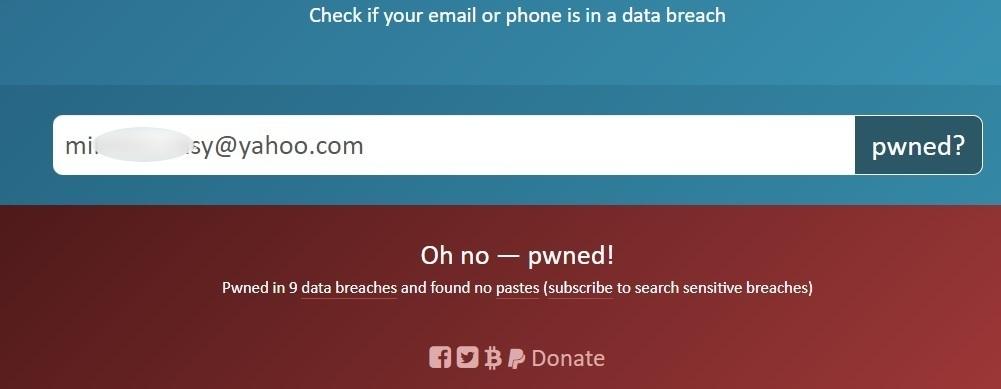
Haveibeenpwned.com is the work of a cybersecurity researcher who gathers all known breaches that affect online accounts. Data breaches are occurring more often than ever. Trying to stay up-to-date with all data breaches is a cumbersome task for an end-user.
Haveibeenpwned lets users check their email address and see if any of their accounts linked to that address have been compromised in an attack, making it easier to change credentials for that service.
Steps to Follow If You Have Been Phished
If you have become a victim of a phishing attack, take these steps to limit damage and prevent others from falling victim.
- Note as many details as you can remember about the attack. Remember if you entered your credentials, shared your card details, or anything suspicious that occurred on your device.
- Change the password of the compromised account and any other accounts with similar passwords. An option to change your password is usually found on a service’s login page. For corporate environments, calling the IT helpdesk can speed up the process. Use a password manager if possible.
- Check if MFA is enabled and working. If not, consider activating it.
- Assess if the possible damage affects any other parties and notify them of the situation. Cybersecurity teams can limit threats the sooner they are informed.
- If you are a US citizen and have suffered financial damage after a phishing attack, contact the FBI’s Internet Crime Complaint Center and fill out the form.
It may seem that the relationship between an attacker and the victims may seem like a one-way street, but that is not the case. One can hinder a phisher’s activity by reporting the suspicious URLs used by the cybercriminals. Reporting is easy, and you can report suspicious URLs using any or all of these methods:
- Google’s Report Phishing Page
- Microsoft’s Report Unsafe Site
- Forwarding the suspicious email to the Anti-Phishing Working Group, partners of US-CERT (Computer Emergency Readiness Team) at phishing-report@us-cert.gov

Educate employees by sharing this guide with them

Implement email filtering tools including inbound DMARC validation

Publish a DMARC record for your domain
Conclusion
Phishing has and will continue to dominate the cyberthreat landscape in the following years to come. While the attacks may vary, phishing affects both consumers and businesses alike. The individuals and organizations that prepare themselves to detect and prevent phishing will be less likely to fall victim.
Explore the chapters:
- 1. Introduction - Complete Guide to Phishing
- 2. Spear Phishing vs. Phishing
- 3. Clone Phishing: How it Works and Defenses
- 4. What Is a Common Indicator of a Phishing Attempt?
- 5. Executive Phishing
- 6. URL Phishing: Real World Examples & Strategies
- 7. Phishing Prevention Best Practices
- 8. Phishing vs. Pharming
- 9. Payment Confirmation Spam Emails
- 10. Phishing vs. Spoofing
- 11. Domain Hijacking
- 12. What does BEC stand for
Get started for free
with Monitor
Start your path to DMARC enforcement with a panoramic view of the traffic being sent on your behalf.
No trial offers, credit cards, or obligations.
Explore all Valimail
has to offer
Go one step further than visibility…Take action! Reach DMARC enforcement faster. Stay compliant with evolving sender requirements. All while protecting your brand.