- Guide
Phishing vs. Spoofing: What’s the Difference?
Phishing vs. spoofing can often trip up businesses. What’s the difference between spoofing and phishing, and do you need to use varying prevention methods for each?
Phishing and spoofing are categories of cyberthreat that both involve deception. A phishing attack fraudulently impersonates a legitimate source, typically via email, to trick the recipient into an action that benefits the attacker. Spoofing allows the attacker to mask their origin and appear to be someone or something else, which is often used to aid phishing and other attacks.
A well-planned phishing attack will often spoof an email address or domain name that the target trusts to make the message seem legitimate. According to a 2022 report from Rhine-Waal University, spoofing is still an integral part of many phishing attacks.
“Over a third of phishing emails in the first two quarters of 2022 involved conventional spoofing tactics. Most such spoofing would easily be defeated by obvious defenses like DMARC [resulting in] over 354 million dollars in cost to defend against related attacks in the first half of 2022.”
– Rhine Waal “Cybercrime Study Group”, Emerging trends in phishing tactics.
In this article, we’ll review phishing vs. spoofing in-depth, showing you the ins and outs and all the differences. After that, we’ll walk you step-by-step through an actual attack that uses spoofing to aid a phishing campaign. Finally, we’ll wrap things up with an overview of recommendations for defending against these twin threats.
Phishing vs. Spoofing: Summary
Before we dissect these two attacks, let’s start with a handy reference table for understanding the differences between phishing vs. spoofing.
The difference between spoofing and phishing:
| Characteristic | Spoofing | Phishing |
|---|---|---|
| Target | Deceives computers, often for the purpose of bypassing security mechanisms that protect people. | Deceives humans, often using spoofing to bypass automated detection mechanisms and reach a person’s inbox. |
| Prevention | Strong security engineering culture and security best practices like DMARC. | Email security best practices and thorough anti-phishing awareness training. |
| Delivery | Social engineering-based attack that targets users. | Technical attack that targets computer software. |
| Purpose | Retrieve information from the target. | Send (impersonated) information to the target. |
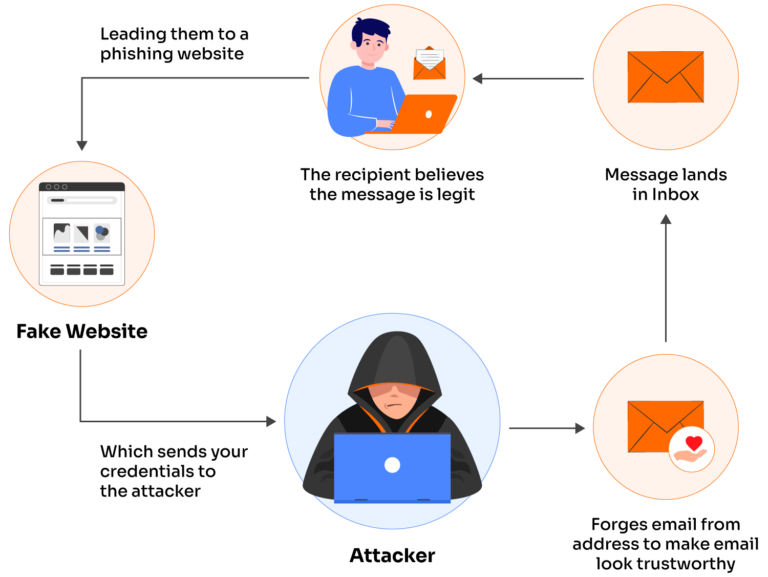
How phishing and spoofing work
Attackers use phishing as a social engineering attack to trick their victims into giving up money, login credentials, or other sensitive data. This attack is so common that even non-technical people know of it. In fact, if you go into your email spam folder, there’s a good chance that a few poorly crafted phishing emails are hoping to get your attention.
Spoofing, on the other hand, is an entire category of attacks that involve pretending to be something or someone else. For example, you could spoof your IP address to appear to be a different computer in a network.
In the context of phishing, spoofing usually refers to “email spoofing” attacks that spoof the From: address of an email. Since this article specifically compares phishing vs. spoofing, email spoofing will be our primary focus.
|
Platform
|
Success Rate
|
Success Rate Frame
|
Estimated FTEs
|
Maintenance
|
Marketplace Apps Identified
|
|---|---|---|---|---|---|
|
DIY Manual
|
20%
|
12+ Months
|
2-3
|
Never ending
|
~100 services
|
|
Outsourced Manual
|
<40%
|
9-12 Months
|
1-2
|
Never ending
|
~100 services
|
|
Valimail Automation
|
97.8%
|
0-4 Months
|
0.2
|
Automated
|
6,500+
|
Simulating a realistic attack with spoofing and phishing
Now that you have a conceptual background for these terms, let’s get hands-on. We are going to spoof a domain to send a phishing email. The email will impersonate an address we do not own.
For the example attack, we’ll use a test domain (trusted-domain.test) that doesn’t exist on the Internet. I made it available on my machine using a local DNS server. This avoids pointing readers to a real domain that someone else might own. However, feel free to test this with a domain you own for even greater realism.
First, we’ll need to verify that the domain we want to impersonate is not protected against spoofing. This involves a protocol known as DMARC. We can check for DMARC using the cross-platform nslookup command.
$ ~ nslookup -type=txt _dmarc.trusted-domain.test
Server: 10.240.80.238
Address: 10.240.80.238#53
Non-authoritative answer:
Authoritative answers can be found from:
$ ~The result is: nothing! In other words, the domain is completely open to spoofing. Let’s start trying to spoof it. You can use many programs to create an arbitrary From: address. For our example, we’ll use the free and open-source Sendmail program.
$ ~ sendmail target@trusted-domain.test
To: target@trusted-domain.test
From: ceo@trusted-domain.test
Subject: Test Send Mail
Hey it’s me, your caring CEO! Please send $5,000 in Monero to this address:
4BJ8ue2vM3N9UrYdDrPueEd3b2jGR...
Thanks!
^D
$ ~
That’s it! Now we can check our inbox. Now I’ll open the email in Thunderbird and see if it came through.
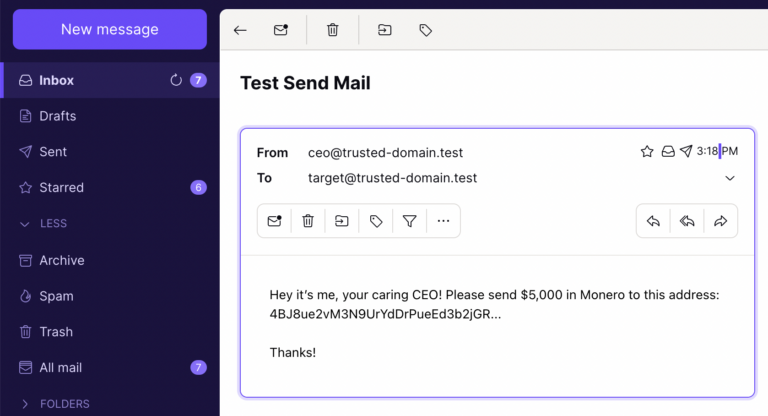
There it is – right in our normal inbox. Pretty scary, don’t you think? The good news is there are proven tools and techniques to help you combat email spoofing and phishing.

Minimal resource requirement with only a single one time DNS change needed

DMARC Enforcement guarantee and 97.8%+ success rate

100% Automated service discovery and 1-click validation
Recommendations for protection against spoofing and phishing
Now that we’ve seen how an attack works, it’s time for the most important piece of the puzzle: what you and your team can do to protect your organization from spoofing and phishing threats.
Prevent spoofing with DMARC
DMARC is the top solution for preventing email spoofing. Email spoofing is significantly more difficult for would-be fraudsters when administrators implement DMARC. You should also ensure that your email provider enforces DMARC so you can detect when other DMARC-protected domains are being forged. Check out Valimail Enforce – an effective solution for eliminating domain spoofing and implementing DMARC enforcement.
DMARC is not the only protocol for making email safer from attacks. In our Guide to Email Security Best Practices, you can learn more about a variety of defenses to harden your email.
Detect phishing
Phishing is a broad category. It ranges from the low-effort scams in your spam folder to elite teams spear phishing executives of billion-dollar enterprises.
Because phishing is an attack geared at humans, several non-technical mitigations can have a significant positive impact. For example, paying attention to these basic red flags can go a long way.
- Misspellings and poor grammar.
- Usage of a non-official lookalike domain name.
- Urges you into an action that usually doesn’t merit immediacy.
- Suspicious attachments.
If you want a more sophisticated and scalable solution, you can hire external auditors to do a phishing campaign against your organization. This will help you find the weak links in the chain, and the auditors usually follow up with extensive training and consulting on improving whatever went wrong during the assessment.
Build a threat model
Ideally, every network would be airtight and every system locked down from any possible attack. In practice, however, cybersecurity budgets are limited. We must prioritize hardening certain systems over others and putting extra effort into mitigating attacks that would cause the most harm.
Threat modeling helps enable this sort of prioritization. It involves analyzing the specific risks that cyber threats present to your organization and hardening systems based on business context.
A threat model might help you determine that email is your top priority. However, you need to model the threats you expect your organization to face to make a contextualized decision.

Educate employees by sharing this guide with them

Implement email filtering tools including inbound DMARC validation

Publish a DMARC record for your domain
Better prevent phishing and spoofing
Phishing and spoofing are complex attack categories with many tactics and strategies that have emerged over the decades. However, security researchers have been diligent in creating new defenses every time cybercriminals and fraudsters expose a new threat vector.
DMARC and phishing awareness are becoming more common by the day, and organizations of all sizes are scrambling to draft coherent threat models to prioritize the attacks that put their data and infrastructure at the most risk.
Software security protections have become more powerful than ever. Yet more complexity means more openings for attackers to sneak through. Additionally, people are more connected to the internet than ever before. The combination of these facts means that spoofing and phishing will remain a threat for years to come.
However, now that know the difference between spoofing vs. phishing, you’re better prepared to prevent attacks and defend your business.
Explore the chapters:
- 1. Introduction - Complete Guide to Phishing
- 2. Spear Phishing vs. Phishing
- 3. Clone Phishing: How it Works and Defenses
- 4. What Is a Common Indicator of a Phishing Attempt?
- 5. Executive Phishing
- 6. URL Phishing: Real World Examples & Strategies
- 7. Phishing Prevention Best Practices
- 8. Phishing vs. Pharming
- 9. Payment Confirmation Spam Emails
- 10. Phishing vs. Spoofing
- 11. Domain Hijacking
- 12. What does BEC stand for
Get started for free
with Monitor
Start your path to DMARC enforcement with a panoramic view of the traffic being sent on your behalf.
No trial offers, credit cards, or obligations.
Explore all Valimail
has to offer
Go one step further than visibility…Take action! Reach DMARC enforcement faster. Stay compliant with evolving sender requirements. All while protecting your brand.