- Guide
What Is a Common Indicator of a Phishing Attempt?
Phishing is a cyberattack in which malicious actors send fraudulent emails disguised as emails from genuine and trusted organizations. According to IBM, phishing was the second most common — and second-costliest — attack vector in 2021.
Attackers use phishing attacks to steal valuable data or infect target systems with dangerous malware. A single, successful phishing attack can have devastating consequences for an organization.
For example, Reuters reported that Austrian aerospace firm FACC lost $47 million because of a hoax email — which appeared to be from the CEO (but wasn’t) — ordered a funds transfer. Similarly, hackers used phishing emails to breach Sony’s network and infect devices with “Wiper” malware.
Fortunately, with the right combination of policies, practices, and user awareness, organizations can mitigate the risk of phishing attacks and protect themselves from costly breaches and malware attacks. Understanding the common indicators of phishing attempts is a critical component in a strategy to combat phishing.
In this article, we’ll review 8 common indicators of a phishing attempt and how you can reduce your risk of becoming a victim.
Executive Summary: 8 Common Indicators of Phishing Attempts
The table below describes the 8 most common indicators of phishing attempts.
Common indicators of phishing attempts
| Indicator | Description |
|---|---|
| Unusual or generic greetings | Unusual greetings from a familiar sender or generic greetings from any sender |
| Subject lines with unusual words or phrases, odd punctuations, or spelling mistakes | Words like “free”, out-of-place punctuations, spelling errors, or unexpected emojis in serious emails |
| Offers that seem too good to be true | Unexpected or unsolicited offers that offer something for nothing |
| Unusual, unknown, or public domain | Emails from public domains, misspelled domains, or domains with an additional word |
| Urgent or threatening tone | Emails that promise dire consequences if the recipient doesn’t take a specific action |
| Grammatical or spelling errors | Emails from legitimate senders are normally spell-checked so messages with mistakes may indicate a phishing attempt |
| Suspicious links or attachments | Links may point to a site that steals information, and the attachment may be malware |
| Sender origin and request type | The email appears to come from a known celebrity or government agency and includes unexpected requests or information |
What is Phishing?
Phishing is a type of cyberattack where an attacker sends a fraudulent message — usually emails — disguised as a message from a legitimate sender, often with the intent to steal from or otherwise negatively impact the receiver.
Most phishing scams involve sending fake emails that look like they originated from a legitimate and trusted organization like a bank or government agency. They contain links to malicious sites that lure the target into entering sensitive data such as their login credentials.
Attackers can then leverage this information to access the victim’s protected account, steal their funds, or steal their identities. Attackers may also send phishing emails to infect a host system with malware via a malicious attachment.
The 8 Common Indicators of a Phishing Attempt
Below are the 8 most common indicators of phishing scams.
1. Unusual or generic greetings
A generic greeting from a sender who usually sends personalized greetings or vice versa is a common phishing red flag. Here’s an example from Netflix:
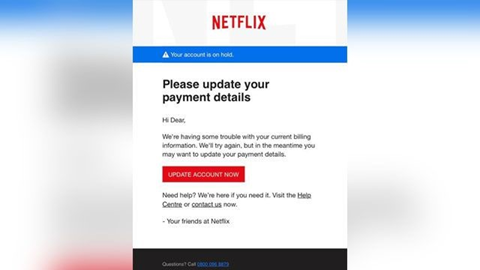
Similarly, an informal greeting from a user who usually greets recipients formally is also a good phishing indicator. For instance, if the company CTO always emails people as “Dear Mr. X” but suddenly sends emails with “Hey Johnny,” it should be viewed with suspicion.
Generic signatures and a lack of contact information are also strong indicators of phishing emails. Legitimate organizations generally provide their contact information. If there is no phone number, email address, or social media links in the signature block, the email is almost always fake.
2. Subject lines with unusual words or phrases, weird punctuations, or spelling mistakes
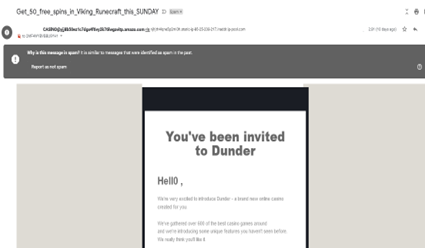
Subject lines with unusual or unexpected words like “Warning”, “Free”, “Your funds”, and “Casino” should set off alarm bells. Strange punctuation, like too many exclamation points or underscores, is also a common indicator of phishing.
Subject lines with spelling mistakes and unexpected emojis may also signal a phishing attempt, especially if the email is about a serious topic or apparently sent by a trusted sender.
|
Platform
|
Success Rate
|
Success Rate Frame
|
Estimated FTEs
|
Maintenance
|
Marketplace Apps Identified
|
|---|---|---|---|---|---|
|
DIY Manual
|
20%
|
12+ Months
|
2-3
|
Never ending
|
~100 services
|
|
Outsourced Manual
|
<40%
|
9-12 Months
|
1-2
|
Never ending
|
~100 services
|
|
Valimail Automation
|
97.8%
|
0-4 Months
|
0.2
|
Automated
|
6,500+
|
3. Offers that seem too good to be true
Any message containing an enticing offer in the subject line or copy should be viewed with suspicion, especially if:
- The offer provides something in return for nothing (or almost nothing)
- It is unexpected
- It originates from a source that usually doesn’t extend such offers
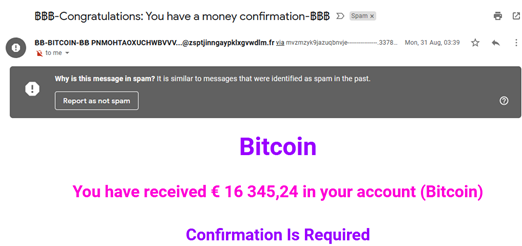
Further, any email that requires the recipient to click on a link or download an attachment to “complete” the offer is also likely a phishing scam.
Here are some examples of phishing emails with too-good-to-be-true offers:
- Starbucks: Free drinks for the holidays
- You are eligible for a free gift
- Earn money while working from home
- Get free Bitcoin in your account
- Get an all-expenses-paid trip to Fiji
4. Unusual, unknown, or public domain
A message from a legitimate organization will always come from its usual, official domain. These domain-related indicators usually point to a phishing email:
- The message is from a public email domain like gmail.com
- The email address contains unusual special characters
- The domain name is misspelled, e.g., bill@nicrosoft. com instead of bill@microsoft.com
- The regular domain includes an additional word, e.g., kathy@amazoncloud.com instead of kathy@amazon.com
Here’s an example. Notice how the email appears to be from Adidas. However, the email address contains strange characters and does not contain the official Adidas domain (adidas.com), which means it is a phishing email.
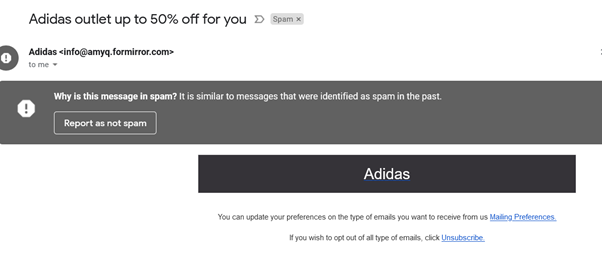
All such emails should be viewed and actioned with extreme caution. Also, if the user has received emails from a domain in the past, but the new domain doesn’t match the older domain, it could indicate that the new email is fake.
5. Urgent or threatening tone
Any email that promises dire consequences for the recipient or tries to create a sense of panic should be viewed with suspicion. These emails may contain subject lines or copy with words or phrases like:
- Your account will be locked unless you act now
- Please complete these steps to avoid account closure
- Your billing information is out of date. You will be fined!
- Dangerous new virus detected on your system
- Urgent attention required: unusual account activity detected!
With these emails, the scammer hopes the recipient will get flustered and immediately click the link or download the attachment.

Minimal resource requirement with only a single one time DNS change needed

DMARC Enforcement guarantee and 97.8%+ success rate

100% Automated service discovery and 1-click validation
6. Grammatical or spelling errors
Bad spelling and incorrect grammar are also common indicators of phishing attempts. Emails originating from legitimate sources will usually be free of such issues, especially if the sender is a native English speaker.
While grammatical or spelling errors may occur if a legitimate sender is not a native speaker, it’s good practice for a recipient to err on the side of caution. Recipients should consider emails riddled with grammatical or spelling errors as a potential indicator of a phishing attempt. Other common indicators of phishing attempts are:
- Data that doesn’t make sense
- Wrong synonyms
- Strange word choices
- Out-of-place capitalization
- Punctuation errors
- Inconsistent email body formatting
7. Suspicious links or attachments
Links and attachments are two of the most common tools in phishing attacks. Malicious links lead to web pages designed to steal sensitive information. If a link looks suspicious, hovering the mouse pointer over the link will show its path and whether it is going to a legitimate page.
Many scammers use Microsoft Office attachments to infect systems with malware. According to Graphus Kaseya, these files accounted for 38% of phishing attacks in 2020.
Other potentially malicious attachment types are:
- .zip
- .jar
- .exe
- .scr
Zip files are particularly suspicious, even if they are password-protected. In fact, an email that includes both a zip attachment and a password to open the attachment is almost always a phishing email.
A password is meant to prevent unauthorized users from accessing and opening the file. However, when the password itself is included in the email, it provides no extra security since the recipient can easily open the attachment, regardless of whether the attachment is legitimate or whether they are the “authorized” recipient.
At the same time, automated malware scanners cannot access or scan the contents of the zip, much less raise an alarm about it. For all these reasons, users must be extremely wary about opening emails that include zip attachments.
8. Sender origin and request type
Another common indicator of a phishing attempt is an email that appears to come from a:
- Government employee
- Celebrity
- Bank manager
These “senders” may make a request or share information that’s not usual for them. Some examples:
- John Smith has shared a whiteboard with you
- Correct address needed for your package delivery
- Please take a look at this invoice
- Your digital receipt is ready
- Confidential information about your account
- Please provide your password to retain access
- Often, these conversations are unsolicited or not started by the recipient.
Scammers may also pretend to be internal senders such as the HR department, IT team, or a C-suite executive to make requests like:
- Change your password immediately
- Install this program to retain access
- Download salary details
- View updated vacation policy
- Transfer $10,000 to this account within 1 hour
The message is likely fake and malicious if such requests or information-sharing are not the norm.
Recommendations to Avoid Phishing Attempts
Now that we’ve covered indicators of phishing attempts, let’s look at how you can reduce your risk of becoming a victim.
Train Employees to Detect Phishing
The most effective way to avoid phishing attacks is through anti-phishing awareness training for employees. Every employee should know how to identify the indicators of phishing attacks so they will be more cautious about clicking on links or downloading attachments. Phishing simulation programs are a fun and immersive way to raise awareness and train employees to avoid phishing scams and respond appropriately to a real-world attack.
Regularly Scan Your IT Infrastructure
Additionally, organizations must regularly scan their IT infrastructure to identify and patch vulnerabilities that may allow attackers to exfiltrate data or launch malware attacks. Cybersecurity controls and governance policies should also be reviewed and updated regularly to reflect emerging threats.
To stay ahead of determined scammers, a multi-layered security approach with all these elements is crucial:
- Antivirus and anti-malware software
- User behavior analytics (UEBA)
- Strong access controls with multi-factor authentication
- Strong web and email security controls
- Automated incident response
- Automated data backup and recovery
Use Email Authentication Protocols
Organizations should also adopt email authentication protocols to prevent threat actors from impersonating their legitimate domain for phishing purposes. Companies can protect their domains and prevent such impersonation with authentication protocols like Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting & Conformance (DMARC).
SPF is an authentication protocol that allows an enterprise domain to “announce” the servers and networks that are authorized to send email using that domain. Thus, SPF focuses on the origination point of an email. DKIM is also an authentication protocol, albeit one that enables a domain to attach a cryptographic signature to the email message. Through this act of “DKIM signing”, it allows the domain to take responsibility for the message. With DKIM, some messages are signed by the sending domain, others by third parties like ESPs, while still others have multiple signatures. DMARC leverages SPF and DKIM to prevent the unauthorized use of an organization’s domain in the visible From: header of an email message. With DMARC in place, the risk of a scammer ”spoofing” a legitimate domain to conduct phishing scams is dramatically reduced at those sites that do DMARC validation. DMARC ensures that a domain’s deliverability is truly based on its sending practices and protects legitimate domains from abuse in phishing or spoofing attacks.

Educate employees by sharing this guide with them

Implement email filtering tools including inbound DMARC validation

Publish a DMARC record for your domain
Conclusion
The first phishing emails went out in the early 90s to only a handful of users. Since then, phishing has evolved into a dangerous and widespread cybercrime. It can be challenging for organizations to avoid phishing attempts. However, by recognizing the common indicators of phishing attempts, organizations can reduce their risk and improve their overall security posture.
Explore the chapters:
- 1. Introduction - Complete Guide to Phishing
- 2. Spear Phishing vs. Phishing
- 3. Clone Phishing: How it Works and Defenses
- 4. What Is a Common Indicator of a Phishing Attempt?
- 5. Executive Phishing
- 6. URL Phishing: Real World Examples & Strategies
- 7. Phishing Prevention Best Practices
- 8. Phishing vs. Pharming
- 9. Payment Confirmation Spam Emails
- 10. Phishing vs. Spoofing
- 11. Domain Hijacking
- 12. What does BEC stand for
Get started for free
with Monitor
Start your path to DMARC enforcement with a panoramic view of the traffic being sent on your behalf.
No trial offers, credit cards, or obligations.
Explore all Valimail
has to offer
Go one step further than visibility…Take action! Reach DMARC enforcement faster. Stay compliant with evolving sender requirements. All while protecting your brand.