- Guide
URL Phishing: What It Is, Real World Examples & Strategies
URL phishing is on the rise, and it’s a scary threat to businesses and consumers.
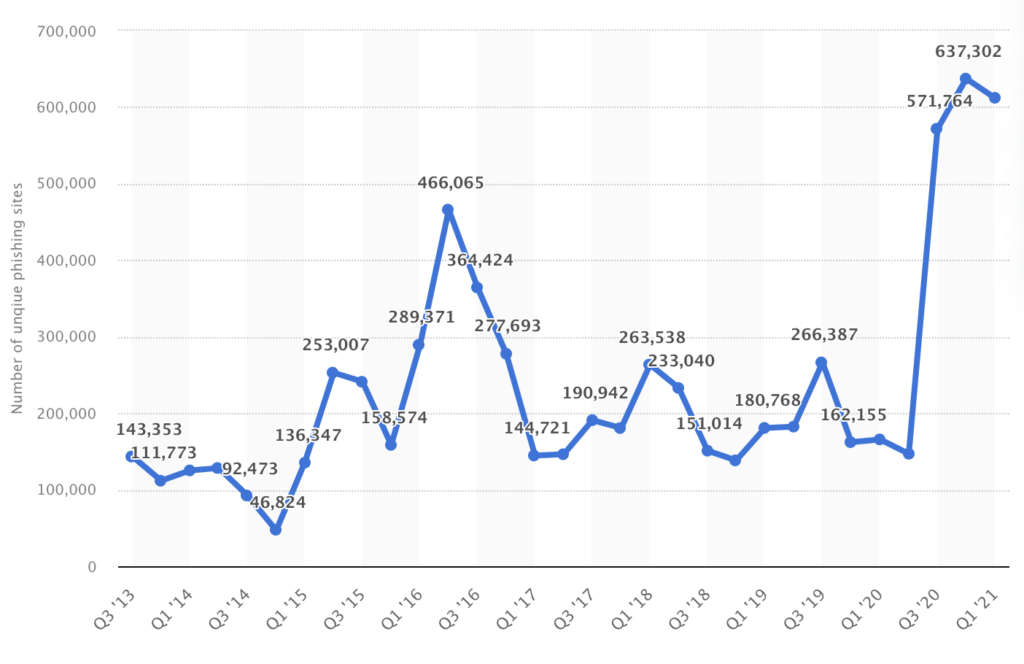
A 2022 Statista report indicates that the number of unique base URLs of phishing sites has increased in Q1 2021 by almost 3.7 times compared to Q1 2020. URL phishing is a popular vector of infection attackers use because it has a relatively high success rate and low cost.
Although URL phishing poses a significant risk, good cybersecurity hygiene and best practices for preventing phishing and combating malicious URLs can help organizations protect themselves.
In this article, we’ll look at the telltale signs that let you know a URL phishing attack might be going on. After that, we’ll explain how to harden your security posture to mitigate this attack and protect your organization.
What Is URL Phishing?
URL phishing is a type of phishing in which the attacker manipulates a URL to trick the victim into visiting the webpage and unwittingly doing the attacker’s bidding. For example, they might coax you into providing sensitive information, downloading malware, or sending them money.
URL phishing tends to occur alongside brandjacking, where cybercriminals design their phishing webpage to mimic known and trusted websites. Often, they try to look like popular social media services, official government domains, or banking websites.
One of the most famous URL phishing incidents occurred in 2016 when security researchers reported that thousands of readers were tricked into browsing on a fake version of Google News. According to Cyware News:
Researcher Avi Lumelsky noted that the URL uses a homographic character as its first character: ‘ɢoogle.news’ to phish users’ This looks similar to the original URL i.e ‘google.news’. Lumelsky further explained that a few years ago in 2016, someone had bought the impersonated site ‘Google.com’ to use it for phishing purposes.
…Upon further investigation, the researcher found that there were several fake URLs that impersonated other original Google domains. Some of the examples includes ‘ɢoogle.company’’; ɢoogle.email’; ‘ɢoogle.tv’; ‘ɢoogle.life’ and even ‘ɢoogletranslate.com’.
– Here’s How ‘google.news’ Becomes ‘ɢoogle.news’ to Phish Users
Types of URL Phishing
Before we decode the clever tricks that URL phishing attackers use to entrap their victims, here’s a quick overview of some common types of URL phishing attacks.
Common Types of URL Phishing
| Type of URL Phishing | Descriptions |
|---|---|
| Masked Links | Link text looks like it points to one domain but really points to another. |
| Open Redirect | The domain is legitimate, but when you open it, the site immediately redirects to the attacker’s domain. |
| Typosquatting | The hacker buys a domain that is a typo of the real domain. |
| IDN Homograph Attack | Unicode allows a domain that is effectively visually identical to the real thing, using similar characters from other languages. |
| Doppelganger Domains | The domain is identical to the legitimate one, but missing a dot. |
How URL Phishing Works
URL phishing is a blanket term that refers to a variety of specific kinds of phishing attacks. What these attack vectors all have in common is using URLs to trick users into doing something that potentially harms them.
Whether this means tricking a user into clicking a masked link, abusing typos to catch hapless users, or any other attack that hijacks a user’s browsing activity to get them onto a phishing page, we’ll cover the ins and outs of this increasingly prevalent form of attack in the sections below.
|
Platform
|
Success Rate
|
Success Rate Frame
|
Estimated FTEs
|
Maintenance
|
Marketplace Apps Identified
|
|---|---|---|---|---|---|
|
DIY Manual
|
20%
|
12+ Months
|
2-3
|
Never ending
|
~100 services
|
|
Outsourced Manual
|
<40%
|
9-12 Months
|
1-2
|
Never ending
|
~100 services
|
|
Valimail Automation
|
97.8%
|
0-4 Months
|
0.2
|
Automated
|
6,500+
|
URL Phishing with Masked Links
One of the oldest tricks in the URL phishing playbook, this attack works by mismatching the text of a link and the URL it points to. For example, consider the following link: https://www.google.com. It looks like a link to Google. Yet, when opened, you go to Valimail’s website! To explain, let’s learn a little bit about HTML. Here’s what a link looks like in HTML code:
<a href="http://this-is-the-domain-the-link-points-to.example">This is the text the user sees</a>
By making the text look like a legitimate domain, the user will often assume that the actual domain the link points to is the same. The code for the trick link we used earlier looks like this:
<a href="https://www.valimail.com">https://www.google.com</a>Pretty clever, right? To learn more about how links work in HTML, check out Mozilla’s excellent guide, Creating hyperlinks.
URL Phishing with Open Redirect
When an attacker can get a site to redirect them to any URL they supply, security professionals call this an “open redirect”. It’s useful for phishing because they can supply a legitimate domain that then redirects you to the attacker’s page.
However, even without this exploit, there are tricks an attacker can use to get a similar benefit. For example, due to the rules of URL parsing, a link to the URL http://google.com-redirect@valimail.com will send you straight to Valimail’s website.
This isn’t even a redirect – rather, the part before the “at sign” represents the username part of the URL. Firefox will at least warn you, but only if the attacker’s phishing page doesn’t accept credentials. It’s a somewhat technical attack, but the point is that attackers can use an attack similar to an open redirect even if no such vulnerability exists on the target domain’s website.
URL Phishing Using Similar-Looking Domains
This simple-sounding trick encompasses an entire category of vulnerabilities. For example, the domain name could be an IDN homograph of the real thing. Alternatively, it could be a subtle typo so that if a user misspells Valimail by saying Vakimail, they’ll unwittingly browse to a phishing page.
There are many ways to make two domains hard to distinguish, but the important thing is how to defend yourself and others when this inevitably occurs. So let’s move on to the most important information and what you probably came here to find: specific, actionable strategies for combating URL phishing.

Minimal resource requirement with only a single one time DNS change needed

DMARC Enforcement guarantee and 97.8%+ success rate

100% Automated service discovery and 1-click validation
How Attackers Deliver URL Phishing Attacks
For a URL phishing attack to work, the attacker needs a way to present the malicious link to you. The most classical way to go about this would be via a phishing email. However, phishing scams are becoming ever trickier, and a variety of more novel attack vectors exist.
For example, phishing scams often use social media phishing to lure you to their URL. The dating site Tinder is a common target. The attacker creates a fake profile designed to acquire as much attention as possible. In their profile, they tell potential dates to message them on Instagram, followed by a link to their Instagram profile.

However, something is wrong with the Instagram link above. The first letter of the URL is actually a lowercase L. This is a homograph that looks very similar to the letter that should appear. If a victim copies and pastes this URL into their browser, they would be taken to a phishing URL that lures them into giving up their Instagram credentials.
The imagination is an attacker’s only limit, as there are many ways to get a URL in front of a target’s eyes.
Best Practices for Preventing URL Phishing
Luckily for security engineers out there who wish to protect their teams from this sort of URL phishing, there are several tactics you can use to mitigate URL phishing threats drastically. Like most defensive security topics, there are practically infinite strategies that could help. However, below we’ve organized a few simple things you can do that have a disproportionately large impact against URL phishing.
URL Filtering
The strongest method for defeating URL phishing is to enforce a company-wide list of allowed URLs. Restricting users to only an approved list of domains is known as “whitelisting”. Admins can add other domains on request. For users who might need a more flexible setup, admins can add exceptions. However, most users should be protected behind the filter.
However, whitelisting is often too cumbersome to manage because IT staff spends too much time evaluating candidates for the whitelist and investigating domains requested by employees. So one compromise is to use a blacklist of known phishing URLs. Check out the phishing-sites and phishing-domains topics on GitHub for up-to-date databases of known phishing URLs. This won’t protect you from spear phishers who will buy a custom domain just to attack your organization, but it will prevent a lot of less sophisticated attacks using generic phishing domains.
Due to the extent that the attack tends to rely on tricking the victim into visiting an attacker’s malicious domain, filtering specific domains like this is an important component in mitigating URL phishing. Popular security tools like Microsoft Defender on Windows make it even easier to deploy this kind of policy across your entire network. For an example of how to configure URL filtering on Windows, see Web content filtering with Microsoft Defender.
Warnings for Suspicious Domains
The open source cybersecurity ecosystem has grown extensively in recent years. As a result, the quantity and quality of free, open-source databases have grown to impressive degrees. As such, anti-phishing tools exist that take advantage of this knowledge.
Web browser extensions like Netcraft and PhishDetector alert users when they are on a known phishing site. As a Windows Domain Admin, you can even automatically install this extension for all users.
Google pioneered this strategy by creating Password Alert. Even though it hasn’t received many updates since it was created in 2015, it works like a charm to protect your Google credentials from phishing pages. Similar tools exist for Firefox, such as the highly-rated Zelda Anti-Phishing addon. You can even implement something like this yourself using the many online databases that exist of known phishing domains.
Security Hygiene
This is a pretty big “other” category, but even if you apply the tactics above, there are always techniques for an attacker to get through. That’s why it’s good to have generally good security. This is more than a high-level truism, and we would love to give you specifics on how to build out your cybersecurity defense strategy to become bulletproof against phishing.
Specifically, check out our Email Security Best Practices, as well as the series this article is a part of, Guide to Phishing.

Educate employees by sharing this guide with them

Implement email filtering tools including inbound DMARC validation

Publish a DMARC record for your domain
Prevent URL Phishing With
Cybersecurity risks continue to threaten businesses and individuals around the globe, making it more important than ever to have a strong security posture. Considering the massive role of phishing, it’s an attack vector that you’d be wise to pay attention to. Malicious links are a primary strategy for phishing attackers to pilfer your credentials and other private data.
The information above should provide you with a solid foundation of knowledge on URL phishing and how it works. Even more important, we hope you’ve understood what routes you can take to improve your defense against this form of attack.
A world with less phishing is safer, and it’s up to us as IT professionals to reduce the effectiveness of URL phishing by implementing excellent, state-of-the-art protection. Whether it’s setting up a URL filter for your staff, implementing a good password policy mandating the use of password managers, or simply educating employees by conducting a phishing campaign and training, we hope you take the next step by actively fighting against URL phishing.
Explore the chapters:
- 1. Introduction - Complete Guide to Phishing
- 2. Spear Phishing vs. Phishing
- 3. Clone Phishing: How it Works and Defenses
- 4. What Is a Common Indicator of a Phishing Attempt?
- 5. Executive Phishing
- 6. URL Phishing: Real World Examples & Strategies
- 7. Phishing Prevention Best Practices
- 8. Phishing vs. Pharming
- 9. Payment Confirmation Spam Emails
- 10. Phishing vs. Spoofing
- 11. Domain Hijacking
- 12. What does BEC stand for
Get started for free
with Monitor
Start your path to DMARC enforcement with a panoramic view of the traffic being sent on your behalf.
No trial offers, credit cards, or obligations.
Explore all Valimail
has to offer
Go one step further than visibility…Take action! Reach DMARC enforcement faster. Stay compliant with evolving sender requirements. All while protecting your brand.