Email security isn’t what it used to be. Today’s cybercriminals are armed with AI tools that can create phishing emails so convincing they’d fool your CFO…and maybe even your CSO.
For enterprises running sprawling, multi-cloud environments with dozens of SaaS platforms, legacy MTAs, and newly acquired domains, those emails also have a far wider attack surface to exploit.
Scary, right?
Many of the Fortune 500 security teams we interviewed are already struggling with the “10 DNS lookup limit” baked into Sender Policy Framework (SPF). When your organization relies on twenty-plus third-party sending services, basic authentication advice won’t cut it.
We wanted to learn more about this phenomenon (both because we’re email nerds and because we want to better protect you), so we put together our 2025 Disinformation and Malicious Email Report—and that’s what we’re using to guide our recommendations for creating better enterprise email security for your business.
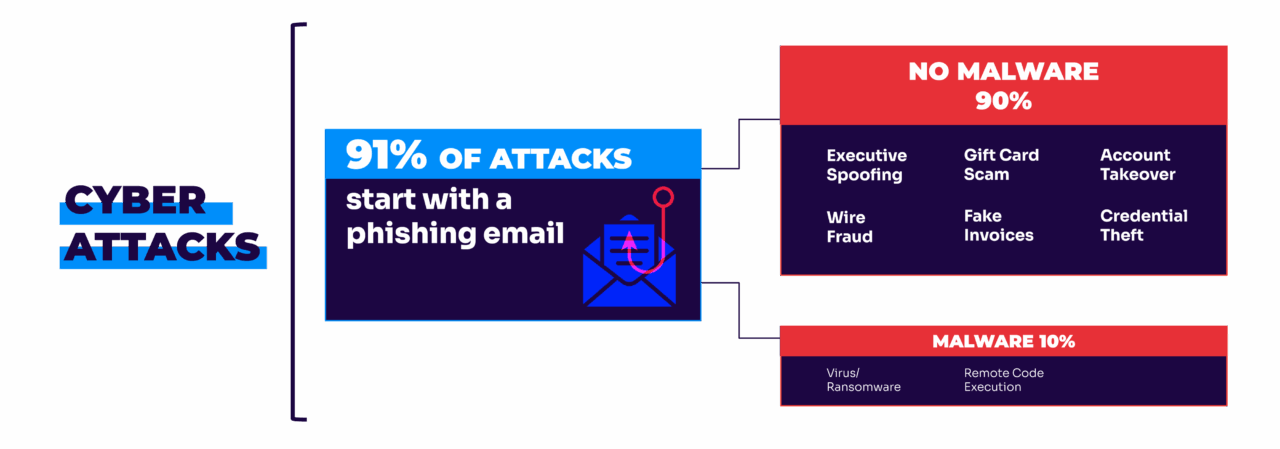
91% of all cyber attacks begin with an email, but 90% of those phishing emails contain no malware whatsoever. Why? Well, they’re just really good at social engineering. These aren’t amateur scammers. They’re playing the long-game (or at least the medium-length game).
In 2024 alone, Valimail tracked over 3.17 billion suspicious emails on behalf of customers. That’s billions of attempts to impersonate brands and trick employees into costly mistakes. And with AI making it easier (and faster) than ever to create convincing fake communications, these numbers will only climb.
Unfortunately, most enterprises rely on single-point solutions that leave dangerous gaps. Modern threats are smart enough to slip through individual defenses, which is why you need a layered approach that combines behavioral AI with zero-trust authentication.
Below, we’ll show you how to build an enterprise email security stack that actually incorporates this layered approach the right way.
| Key takeaways for busy security leaders – Exceeding the SPF 10‑lookup limit silently breaks authentication and exposes trusted domains to exact‑domain spoofing. – Zero‑trust DMARC enforcement provides a single source of truth for every sender and vendor. Behavioral AI only reaches its full potential when layered after airtight domain authentication. – Automated sender discovery and dynamic SPF flattening are mandatory to keep pace with constantly changing software stacks. |
The limitations of single-point email security solutions
Most enterprises treat email security like a game of whack-a-mole. They spot a problem, deploy a solution, and assume they’re covered. Sure, this takes care of the immediate issue, but it ultimately creates an ugly patchwork of security tools that work in isolation.
Each solution simply protects against specific threats while leaving blind spots everywhere else.
Secure email gateways (SEGs) are a perfect example. They’re great at what they do: scanning attachments, blocking known malicious domains, and filtering obvious spam. But when a cybercriminal sends a perfectly clean email that simply asks an employee to update their login credentials on a fake but convincing website, most SEGs will wave it right through.
The same goes for traditional antivirus solutions that focus on malware detection. Remember, 90% of successful phishing attacks don’t contain any malware at all. They rely purely on social engineering and credential theft. Your virus scanner isn’t going to catch an email that looks like it came from your company’s HR department asking employees to verify their benefits information.
Complexity makes the gaps wider. Enterprises often run multiple SEGs across regions, overlaying them with cloud email security supplements, yet still miss an outdated payroll software that sends from an unmanaged subdomain.
Even worse, solutions offering everything in one platform can often create a false sense of security. IT teams see their email gateway blocking thousands of threats daily and assume they’re fully protected. Meanwhile, the most dangerous attacks (the ones designed to look legitimate) are landing in inboxes unopposed.
Modern email threats require multiple layers of defense, each addressing different attack vectors.
You can’t solve a multi-dimensional problem with a one-dimensional solution.
The modern email threat landscape
Cybercriminals are getting uncomfortably good at their jobs. What used to be obvious spam emails (filled with spelling errors) have turned into smart AI-powered campaigns.
Take business email compromise (BEC) attacks, for example. These aren’t your typical “Nigerian prince” scams anymore. Modern BEC attacks involve extensive reconnaissance: criminals research company hierarchies, communication patterns, and even writing styles before writing messages that perfectly mimic legitimate business communications. They’ll impersonate a CEO requesting an urgent wire transfer or a vendor asking for updated payment details, and the emails look absolutely authentic.
Then there’s the rise of exact domain spoofing, where attackers forge the “From” field to make emails appear as if they’re coming directly from trusted brands or business partners. Valimail’s data shows this is happening at an alarming scale: billions of spoofing attempts annually, many targeting organizations with weak or nonexistent DMARC policies.
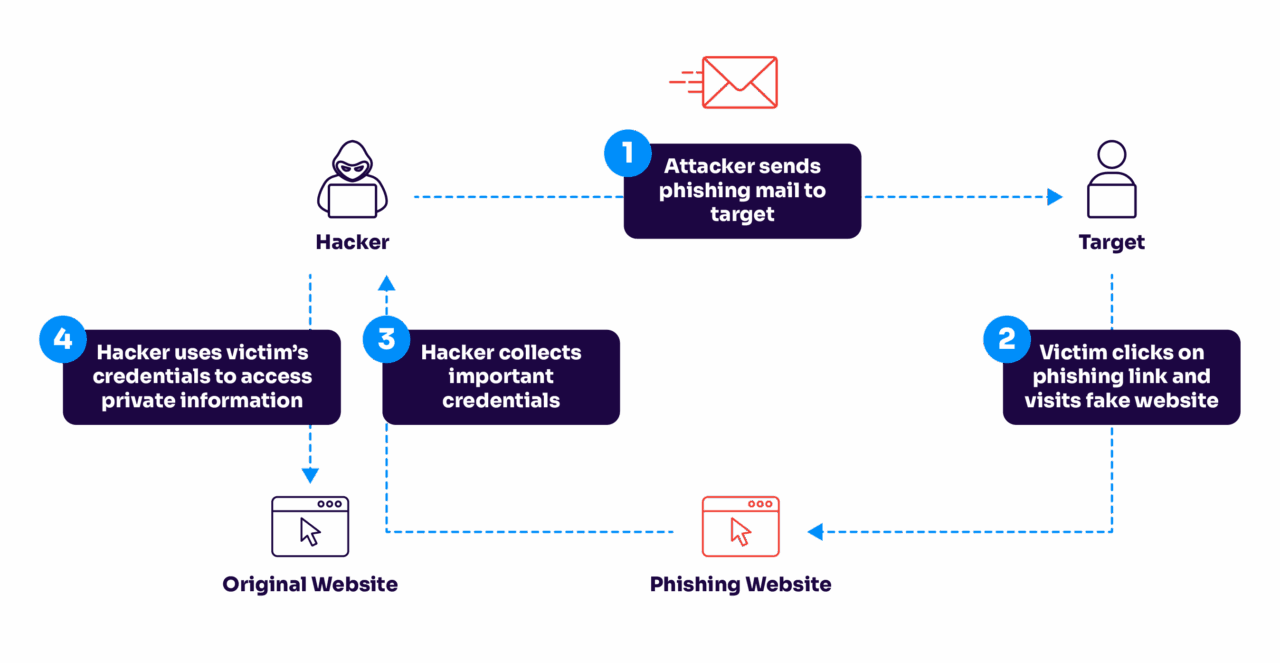
AI has made everything worse. Cybercriminals now use generative AI to create contextually relevant phishing content in multiple languages, build convincing fake websites, and even generate voice recordings for vishing attacks. What used to take skilled social engineers hours to create can now be automated and scaled across thousands of targets.
Supply chain attacks have also become a favorite tactic. Instead of directly targeting large enterprises with strong security, attackers compromise smaller vendors or service providers with weaker defenses, then use those relationships to launch attacks against bigger targets.
Industry-specific considerations
Different industries face different email security challenges, and the stakes vary depending on what you’re actually protecting. Valimail’s latest research across thousands of enterprise domains shows some telling patterns about how various sectors approach email authentication (and where the gaps still exist).
Overall, it’s trending in the right direction (from 74-94% DMARC adoption), and it’s growing every month.
Financial services
Financial services has a 84.8% DMARC adoption, but here’s the concerning part: 33.8% of those domains are still running policies set to “none.” That means they’re visible but not actually protected against spoofing.
For an industry that handles sensitive financial data and is a prime target for fraud, that gap is worrisome.
- Regulatory requirements (PCI DSS 4.0) now include DMARC as a “good practice”
- High-value targets for BEC attacks and wire fraud schemes
- Customer trust is everything—brand impersonation can cause lasting damage
- Need for real-time fraud detection integrated with authentication protocols
- Frequent M&A activity often leaves financial groups with dozens of inherited domains that instantly push SPF records past the 10‑lookup limit.
Healthcare organizations
Healthcare organizations show 86.6% DMARC adoption, but they face unique challenges around patient privacy and communication workflows.
- HIPAA compliance requires protecting patient communications
- Medical device integrations often complicate email authentication
- Phishing attacks targeting prescription information and medical records
- Critical need for secure provider-to-provider communications
- Multiple EHR portals and notification services balloon SPF records, forcing manual record flattening that quickly drifts out of compliance
Manufacturing
Manufacturing actually leads in protection levels with 92.6% DMARC adoption and strong enforcement policies, likely due to supply chain security requirements.
- Supply chain attacks targeting vendor relationships
- Industrial espionage through email compromise
- Need to protect intellectual property and trade secrets
- Integration challenges with legacy systems and IoT devices
- Global production sites often route email through regional ISPs, creating authentication gaps that slip under centralized dashboards
Government entities
Government entities face arguably the highest stakes. They have a 82.5% DMARC adoption, and FedRAMP now requires enforceable DMARC policies for all cloud service offerings.
- Nation-state actors specifically targeting government communications
- Public trust and transparency requirements
- Strict compliance mandates and audit requirements
- Need to prevent disinformation campaigns using government domains
- Complex inter‑agency workflows mean a single misconfigured sub‑domain can undermine years of security investment
How to build your enterprise email security stack
Don’t worry. Building a modern email security stack isn’t about ripping out your existing tools and starting from scratch. It’s about layering defenses to create a comprehensive shield against today’s threats.
Here’s how to do it right.
1. Establish zero-trust authentication
Your first step is getting email authentication locked down. This is your foundation: everything else builds on top of it. Zero trust authentication means never assuming an email is legitimate just because it claims to come from a trusted domain.
Start with DMARC implementation, but don’t fall into the “checkbox compliance” trap. Having a DMARC record set to “p=none” might satisfy mailbox provider requirements, but it won’t actually protect you. You need to work toward enforcement policies (either “quarantine” or “reject”) to stop spoofing attacks.
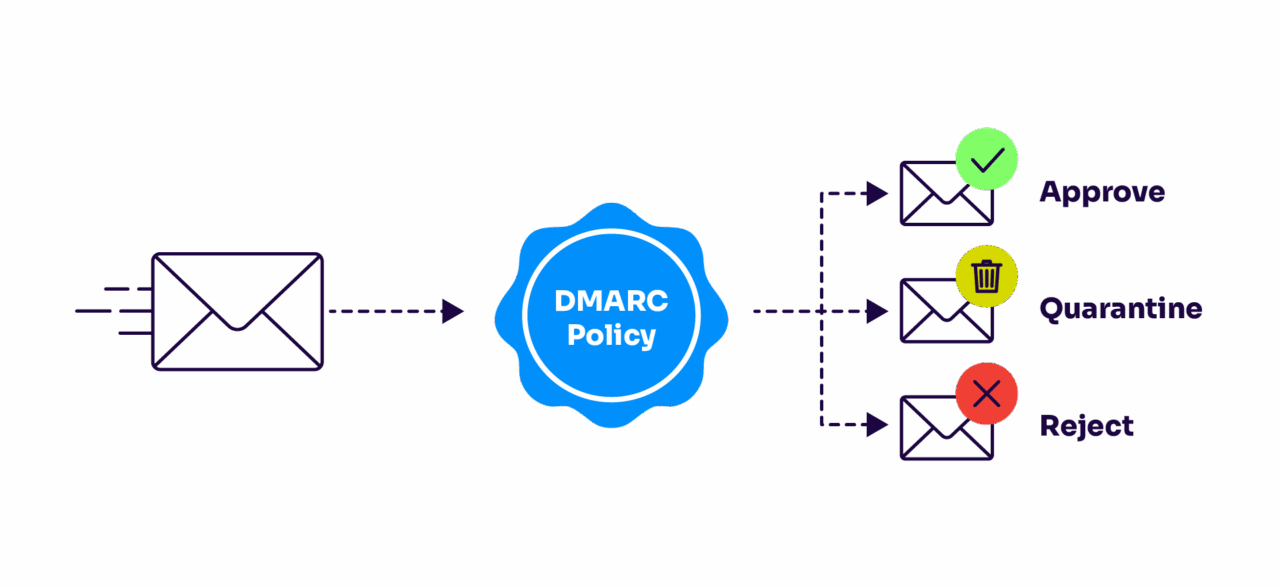
The biggest obstacle enterprises face is identifying all their legitimate email senders. Marketing platforms, CRM systems, helpdesk tools, payroll services—yep, they all send emails on your behalf, and they all need to be properly authenticated. Miss one, and you’ll either block legitimate emails or leave a gap for attackers to exploit.
And then there’s the SPF problem. Every additional software that marketing or another sender adds multiple DNS lookups; hits eleven, and inbox providers start ignoring your remaining mechanisms. Enterprises routinely sail past this limit without realizing it until delivery fails or spoofing succeeds.
This is where automated solutions can help. Instead of manually tracking down every sending service and managing complex DNS records, platforms like Valimail can automatically discover your email ecosystem and handle the technical implementation. They can even overcome traditional limitations like the SPF 10-lookup limit that often prevents full DMARC enforcement. Valimail Enforce automatically eliminates excess lookups with our infinite SPF macro, ensuring you stay under the limit without sacrificing visibility.
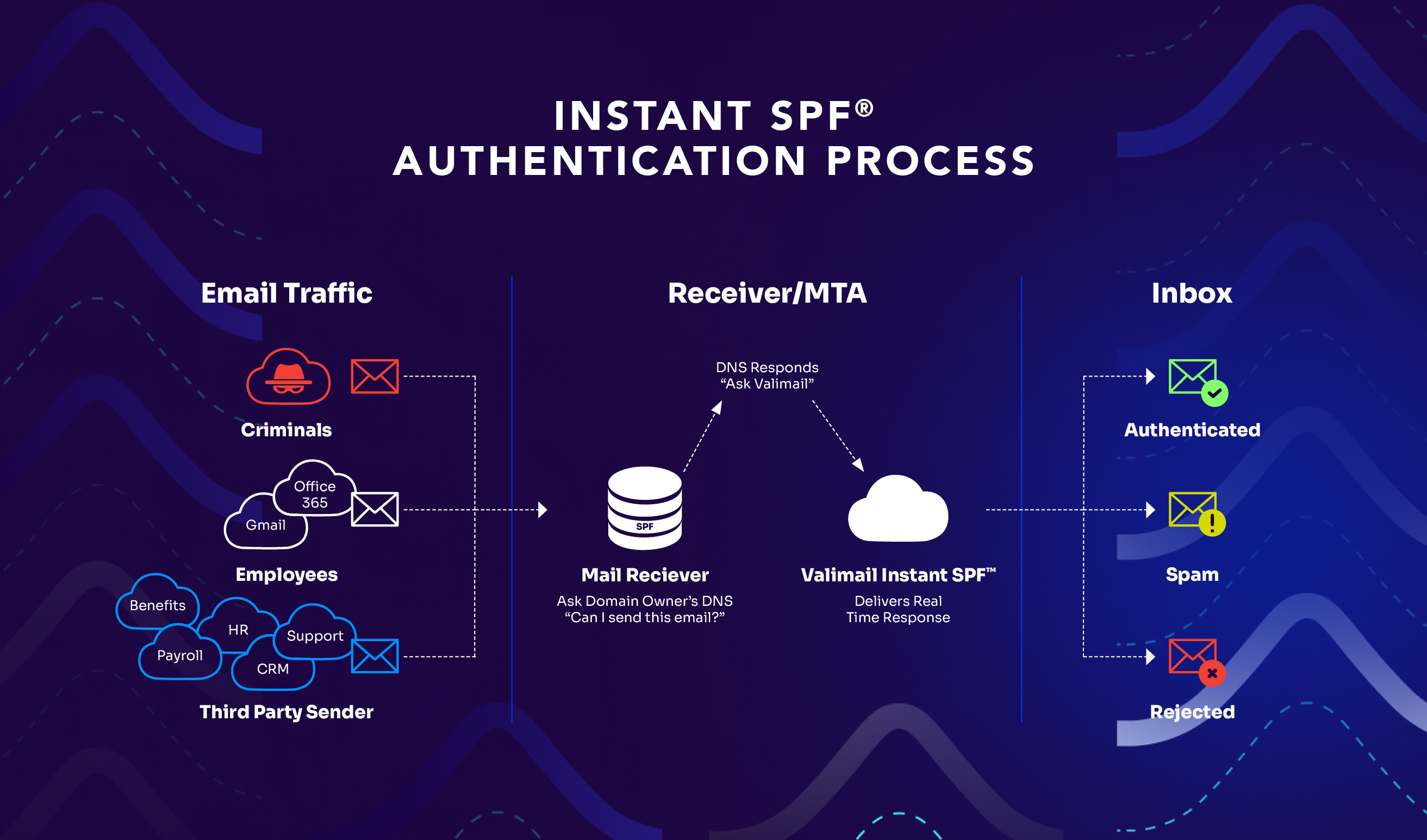
The goal is continuous DMARC enforcement with complete visibility into who’s sending emails using your domain. When you achieve this, you’ve established the trust foundation that makes everything else possible.
Curious where your brand’s domain status lies? Use our free domain checker to get a good baseline for your email security tech stack:
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Your Domain
Not protected AGAINST IMPERSONATION ATTACKS
DMARC NOT AT ENFORCEMENT
exampledomain1.com
Authentication Status for January 10, 2025
DMARC at Enforcement
SPF Record Configured
BIMI Ready
exampledomain1.com
Authentication Status for January 10, 2025
DMARC at Enforcement
SPF Record Configured
BIMI Ready
2. Deploy behavioral AI email security detection
Authentication foundation solid? Good. Now, it’s time to layer on behavioral AI to catch the advanced attacks. This is where you detect the threats that pass authentication checks but showcase suspicious patterns.
Behavioral AI analyzes things like:
- Sender patterns
- Email timing
- Content structures
- Recipient behaviors
For example, it might flag an email from your CEO’s authenticated account that was sent at 3 AM requesting an urgent wire transfer (even though the email technically passes all authentication checks).
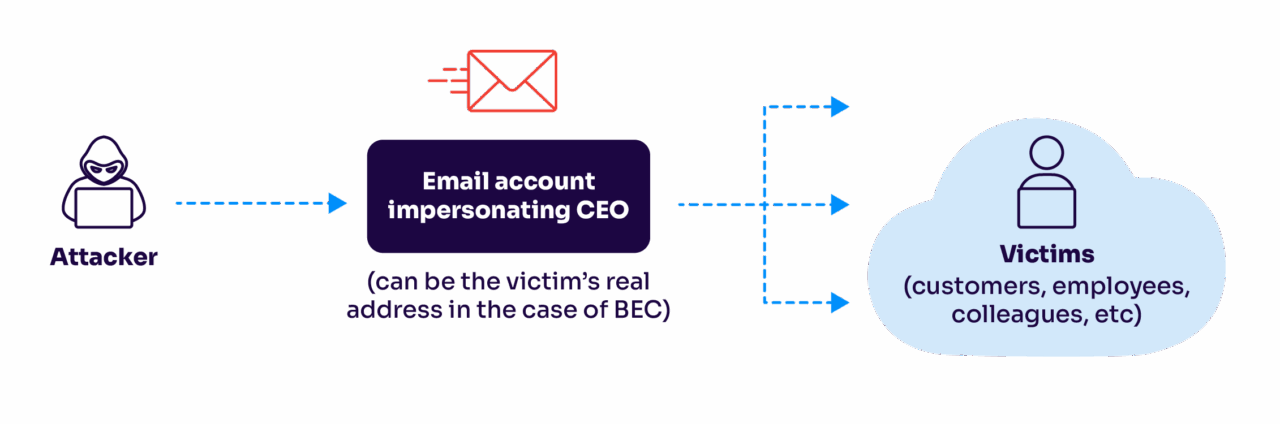
It’s all about choosing AI solutions that integrate well with your existing infrastructure and complement your authentication layer rather than competing with it. Look for platforms that can analyze both metadata and content while providing clear explanations for their decisions.
You don’t want a black box that flags emails without telling you why.
Training periods matter. Behavioral AI needs time to learn your organization’s normal communication patterns before it can identify abnormal ones. Plan for an initial period of monitoring and tuning to reduce false positives while guaranteeing real threats get caught.
The AI should continuously learn from new attack patterns and update its detection models without requiring manual intervention from your team.
3. Create monitoring and response workflows
Great detection capabilities don’t mean anything if you can’t act on the intelligence they provide. Your third layer is building monitoring and response workflows that turn security alerts into actionable intelligence.
Start with centralized reporting that aggregates data from both your authentication and AI detection layers. You need visibility into authentication failures, suspicious behavior patterns, and successful threat blocks in one dashboard. This helps you understand your overall threat landscape and identify trends.
Establish clear escalation procedures for different types of threats. A failed authentication attempt might warrant a different response than a successful AI detection of insider threat behavior. Define who gets notified, when, and what actions they should take.
Automate what you can, but keep humans in the loop for complex decisions. Automatically quarantining obvious spoofing attempts is fine, but emails flagged for suspicious behavior might need human review before taking action.
Build feedback loops that help your systems learn and improve. When your team investigates a flagged email and determines it’s legitimate, that information should feed back into your AI models to reduce similar false positives in the future.
Future-proof your business against email threats
The combination of zero-trust authentication and behavioral AI creates a defense system that is greater than the sum of its parts. This is non-negotiable for enterprise email security in 2025 (and beyond).
Your first step should always be establishing strong email authentication with DMARC enforcement. This foundation stops the most common attacks and creates the trust framework that makes advanced detection possible.
We can help you get started. Valimail’s zero trust authentication platform helps enterprises achieve DMARC enforcement 4x faster than traditional approaches with automated sender discovery and continuous monitoring.

While we’re the experts in email authentication and the #1 G2 leader for DMARC, we realize that a layered approach is the best solution for email security. That’s why we partner with SEGs like Abnormal AI, Cloudflare, and Microsoft to bring you the most domain protection.
Want to learn more and chat about how we and your partners can be your ultimate email security tech stack?