A bank customer receives an urgent email about suspicious activity on their account. The email looks legitimate—complete with the bank’s logo and official formatting. They click the link and enter their credentials to “verify their identity.” You can guess where this is going…Within hours, their account is drained.
This isn’t a hypothetical scenario—it’s happening thousands of times a day to financial institutions worldwide. Banks and financial services are prime targets for email-based attacks, and for good reason. After all, why would cybercriminals bother with small-time scams when they can impersonate a bank and hit the jackpot?
The financial sector faces more phishing attacks than any other industry. A single successful breach can cost a bank millions in direct losses, regulatory fines, and reputation damage. And let’s be honest—in an industry built on trust, the reputation hit will hurt more than the financial one.
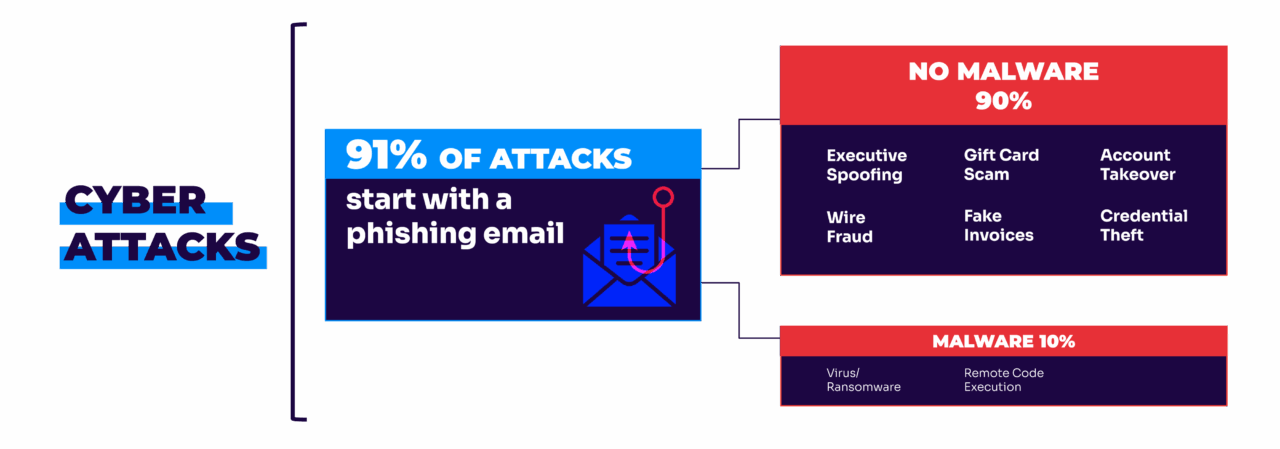
This is where DMARC (Domain-based Message Authentication, Reporting, and Conformance) can help. It stops cybercriminals from impersonating your bank in emails, protecting both your institution and your customers from sophisticated phishing attacks.
Below, we’ll break down everything financial institutions need to know about DMARC: why it’s non-negotiable for modern banking, how to implement it while juggling regulatory requirements, and what happens if you don’t. Plus, we’ll show you how to get it done without disrupting your daily operations—because the last thing you need is another system shutdown.
Why email security matters in finance
While fintech startups might push fancy apps and blockchain solutions, good old email still handles the heavy lifting of daily financial operations. And your customers expect every email from their bank to be legitimate. They trust that account alert, that loan approval, that wire transfer confirmation.
And they should be able to trust it. However, the rise of sophisticated phishing attacks is putting that trust under fire.
Think about all the critical information flowing through financial email systems every day. On the customer side, you’re sending everything from account statements and transaction alerts to loan documents and investment updates. Your customers count on these communications being genuine—their financial lives depend on it.
Then there’s the internal side of things. Wire transfer authorizations, trading confirmations, risk assessments, audit documents—the list goes on. One compromised email in this chain could be a disaster. Your employees need to trust that when they get an urgent wire transfer request from the CEO, it’s really from the CEO.
Let’s not forget about all your external relationships. Every day, you’re exchanging sensitive information with payment processors, vendors, insurance providers, and investment partners. Each of these connections represents a potential vulnerability if your email isn’t properly secured.
From Federal Reserve communications to SEC filings, audit reports to compliance documentation—these aren’t just important emails, they’re legal obligations. When a regulator sends your institution an email, you need to know it’s legitimate. And when you respond, they need the same certainty.
Unlike other industries, where a compromised email might lead to a minor headache, in finance, it can trigger a catastrophic chain of events. A single spoofed email could result in millions in fraudulent wire transfers, exposed customer financial data, compromised trading systems, or massive compliance violations.
The real cost of email fraud in finance
When cybercriminals successfully spoof your bank’s domain, the damage spreads like wildfire through your organization, your customers, and your reputation.
Imagine a scenario where attackers impersonate your bank and convince customers to “verify” their account details. Or worse, your finance team receives what looks like a legitimate wire transfer request from an executive. By the time anyone realizes it’s fraud, the money’s long gone—often millions of dollars that you’ll likely never recover.
And that’s just the beginning. The cleanup costs can exceed the initial loss:
- Forensic investigations to trace the breach
- System-wide security audits and upgrades
- Legal fees (lots of them)
- Customer reimbursements
- Credit monitoring services for affected customers
- Emergency PR campaigns to control the damage
Trust takes years to build, seconds to destroy. In banking, your reputation is quite literally your currency. When customers see headlines about your bank falling victim to email fraud, their confidence crumbles. They start questioning whether their money is safe with you. Whether they can trust those email alerts you send. Whether they should move their accounts elsewhere.
This loss of trust doesn’t just affect your retail banking—it ripples through every aspect of your business:
- Corporate clients may reconsider their banking relationships
- Partners might distance themselves to protect their own reputations
- Top talent might think twice about joining your team
- Investors could start questioning your security practices
Every new security measure you implement, every customer you need to win back, every regulatory requirement you must meet—it all adds up. Some banks never fully recover their former market position after a major security breach.
What is DMARC?
DMARC is an email authentication protocol that helps banks and financial companies protect their domain from unauthorized use by verifying sender identity and enforcing security policies. It works by teaming up with two other security protocols:
SPF (Sender Policy Framework)
SPF is your approved sender list. It tells email providers exactly which servers are allowed to send email from your domain. If an email comes from anywhere else—even if it looks legitimate—it fails the SPF check.
DKIM (DomainKeys Identified Mail)
DKIM adds a digital signature to your emails that proves they haven’t been tampered with in transit. It’s similar to the way your bank seals important documents—if the seal is broken or missing, something’s wrong.
How DMARC makes decisions
When an email arrives claiming to be from your bank, DMARC checks both SPF and DKIM. Based on what it finds, it can take three different actions:
- p=none: “Monitor mode.” The email gets delivered, but you get reports about it.
- p=quarantine: Suspicious emails go straight to spam.
- p=reject: Unauthorized emails get blocked completely. No questions asked.
However, DMARC isn’t just about blocking bad emails. It also sends you detailed reports about who’s trying to use your domain. You’ll see attempted spoofing attacks, unauthorized sending attempts, and even legitimate emails that might be failing authentication.
Once you set DMARC up, it works everywhere. Gmail, Outlook, Yahoo—all major email providers require DMARC before delivering emails claiming to be from your domain. And unlike AI-based security tools that play a constant game of catch-up with fraudsters, DMARC simply verifies sender identity. Either you’re authorized to send email from the domain, or you’re not.
How to implement DMARC for banks and financial companies
1. Evaluate your email infrastructure
Start with a thorough audit of your email ecosystem. Map out every system, service, and third party that sends email on behalf of your domain. This includes your customer communication platforms, marketing tools, trading systems, and any other services using your domain to send email.
Document your sending IPs, mail servers, and cloud-based email services. Pay attention to your legacy systems handling specialized financial transactions—they’re often overlooked. If you need help getting visibility into your domains, use Valimail Monitor for free.
2. Implement SPF
Create a comprehensive SPF record that includes all legitimate email sources. This means accounting for your core banking systems, trading platforms, customer service tools, marketing automation systems, and third-party financial service providers. Start with a minimal SPF record and gradually expand it to include all authorized senders. Test thoroughly before publishing to avoid disrupting important communications.
3. Set up DKIM
Configure DKIM signing for all your email sending services. This step maintains the integrity of sensitive financial communications. Generate strong encryption keys (2048-bit RSA recommended) and implement them across all your email sending systems.
4. Create your DMARC record
Start with a monitoring policy using this basic format:
v=DMARC1; p=none; rua=mailto:dmarc-reports@yourbank.com. This lets you gather data about your email traffic without affecting delivery. Double-check your reporting address is set up to handle the volume of reports you’ll receive because financial institutions typically generate massive amounts of email traffic.
Curious what your DMARC record is? Use Valimail’s free domain checker to get your real-time DMARC record:
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Your Domain
Not protected AGAINST IMPERSONATION ATTACKS
DMARC NOT AT ENFORCEMENT
exampledomain1.com
Authentication Status for January 10, 2025
DMARC at Enforcement
SPF Record Configured
BIMI Ready
exampledomain1.com
Authentication Status for January 10, 2025
DMARC at Enforcement
SPF Record Configured
BIMI Ready
5. Monitor and analyze
Review your DMARC reports carefully. Watch for unauthorized sending attempts, authentication failures from legitimate systems, potential security gaps, and third-party compliance issues. Use this data to refine your authentication setup before moving to enforcement.
6. Address authentication failures
Work systematically through any authentication issues. Financial institutions often face challenges with legacy systems not configured for modern authentication, third-party services sending unauthenticated email, misconfigured marketing platforms, and department-specific applications with custom email capabilities.
7. Move to enforcement gradually
Once you’re confident in your authentication setup, begin enforcement in phases. Start with a small percentage of traffic at p=quarantine, then gradually increase the percentage. Move to p=reject only when you’re fully confident in your setup. Maintain aggressive monitoring throughout the transition.
8. Document and maintain
Create comprehensive documentation of your DMARC implementation. Include authentication configurations, policy decisions, emergency procedures, vendor contact information, and compliance considerations. This documentation helps maintain consistency and respond to audits.
DMARC best practices for financial institutions
These best practices will help you reach (and maintain) DMARC enforcement:
- Start with thorough monitoring. Begin with a p=none policy and collect at least 30 days of data before making policy changes. This baseline helps you identify legitimate senders and spot potential issues before they affect financial communications.
- Implement granular policies for different domains. Your main banking domain might need stricter policies than your marketing subdomain. Create domain-specific policies that match the risk level and business requirements of each domain’s purpose.
- Set up automated alerts. Configure your DMARC system to notify your security team about sudden changes in authentication patterns or unusual sending behavior.
- Maintain strict third-party oversight. Create a formal process for vetting and monitoring third-party services that send email on your behalf. Every vendor should meet your authentication standards before getting authorized.
- Keep detailed authentication records. Document every change to your SPF, DKIM, and DMARC records. This audit trail isn’t just good practice—it’s often required for financial compliance.
- Plan for BIMI implementation. Once you’ve achieved DMARC enforcement, prepare to implement Brand Indicators for Message Identification (BIMI). This adds your bank’s logo to authenticated emails in supporting email clients.
- Review and update regularly. Schedule quarterly reviews of your DMARC implementation, alignment with current regulations, and authentication success rates.
Protect your financial institution with Valimail
The stakes in financial services are too high to just leave your email security to chance. With every phishing attack costing banks millions in losses, regulatory fines, and reputational damage, implementing DMARC isn’t just an IT decision—it’s a business imperative.
We get it, though. Between managing complex banking systems, keeping up with regulatory requirements, and maintaining critical services, your IT team already has its hands full.
That’s where Valimail can help.
We’re not just another security vendor. Think of us as your email security partner (not just another tool in your tech stack). We’ve helped major financial institutions worldwide implement DMARC successfully, and we understand the unique challenges banks face. Our automated platform takes the complexity out of email authentication to allow you to:
- Reach enforcement faster with automated sender management
- Maintain compliance with automated reporting and documentation
- Spot potential threats before they become problems
- Focus on your core business while we handle email authentication
Implementing Valimail’s Enforce, was a significant step in implementing best email security standards via DMARC, DKIM, and SPF and has helped us improve the security of our email communication.”
Senior Information Security Engineer at a Global Financial Services Company
Learn more about how Valimail helped a global financial services company wrangle their DNS records and get DMARC to enforcement.
Ready to protect your institution from email-based attacks?
Sr. Content Marketing Manager at Valimail
Alyssa Harmon