How much can you trust that a political fundraising email really came from who it appears to come from — or that if you click the links in the message, that the money you donate will actually end up in the account of who you intended to support?
The answer, when it comes to most U.S. campaigns and political action committees (PACs), is simple: Not much.
Note: This is an excerpt from Valimail’s research report, 2020 Election Infrastructure Remains Vulnerable to Email Hacking.
We take a lot on faith when we open and click on emails sent by political campaigns and PACs. That’s because, for the most part, the domains used by these organizations are not protected from spoofing through the industry-standard authentication technologies.
We’ll start with the two leading presidential candidates. Joebiden.com has a DMARC record that is set to the most stringent policy, p=reject. As Valimail’s research report went into production, however, the domain’s SPF record was changed, and it became misconfigured, exceeding the standard’s built-in limitation of 10 DNS lookups (a technical constraint that domain owners often fail to observe). This means that some legitimate mail sent from Joebiden.com may fail to authenticate properly — so we cannot characterize the domain as being fully and correctly at DMARC enforcement.
By contrast, Donaldjtrump.com is not protected at all. It has a correctly configured DMARC record, but the DMARC policy is p=none, meaning that spoofed messages impersonating this domain will be delivered as normal. Also, like Joebiden.com, the SPF record associated with this domain has a misconfiguration that may result in authentication failures for some mail.
The candidates’ parties have domains with similar configurations. GOP.com has a published DMARC record but a policy of p=none, while Democrats.org has a strict DMARC policy of p=reject, and is correctly configured, so it can be said to be using DMARC enforcement. As a result, email from the Republican party can be more easily impersonated than email from the Democratic party.
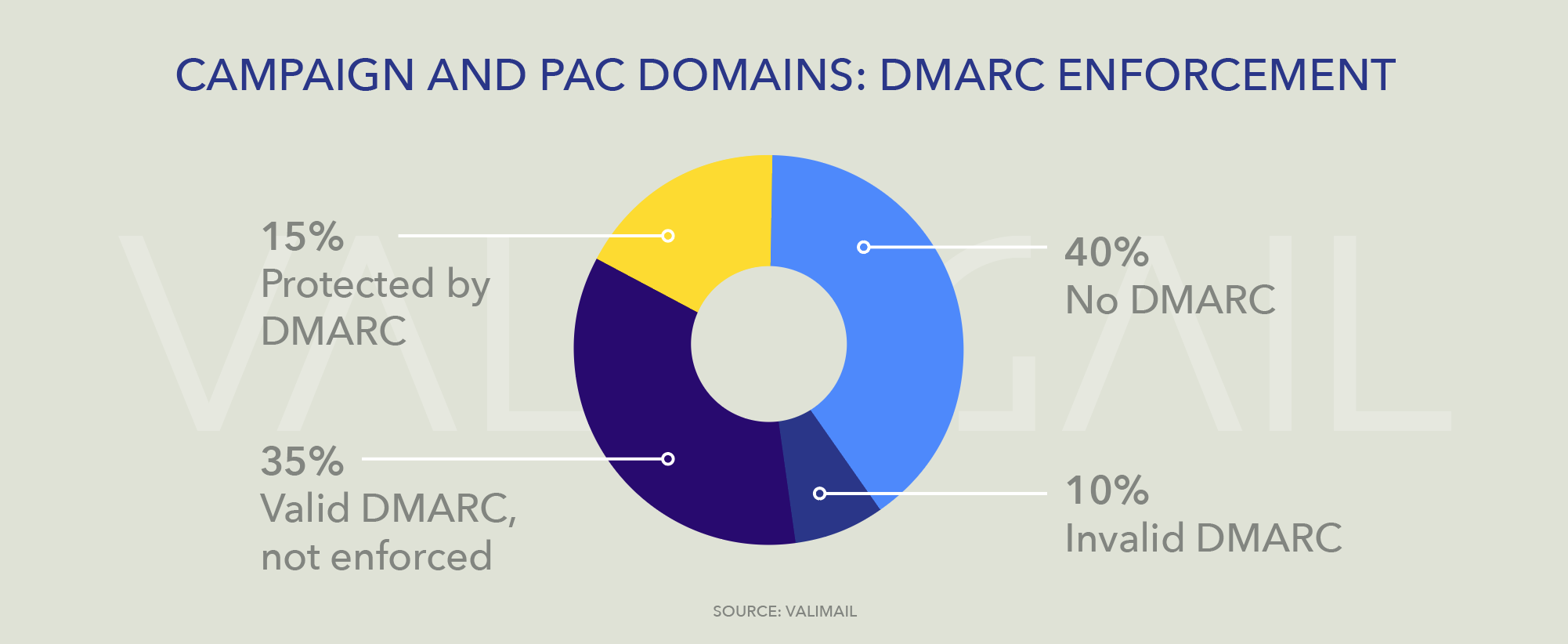
Examining these four domains together with domains for the 20 largest PACs and 20 largest SuperPACs, as listed by OpenSecrets.org, reveals that email security hygiene is not a high priority across the board. Of the 40 domains in this cohort, only 6, or 15%, are protected from spoofing with DMARC at enforcement (p=reject or p=quarantine policies). Domains with DMARC enforcement include three liberal-leaning PACs (emilyslist.org, lcv.org, and smart-union.org), one centrist organization (rtx.com, which is the domain of Raytheon, a major donor to both parties), and one conservative PAC (a1apac.org), in addition to the campaign domains mentioned above.
(There are only 40 domains for a total of 44 organizations because some of the PACs and SuperPACs do not have registered domains that we could find.)
Another 35% have DMARC records that are correctly configured but have a monitor-only policy (p=none), while 40% have not made any attempt to deploy DMARC at all. See the pie chart below for details.
Looking at SPF, which is an older and more widely deployed standard, we see that most of these campaigns and PACs have at least made the attempt to use SPF, with only 10% having no SPF record, and 82.5% publishing a valid SPF record.
This is not surprising for marketing-driven organizations, as SPF is a widely understood marketing best practice, which, if properly configured, can help improve the deliverability of emails sent from that domain. Unfortunately, SPF by itself provides no protection against impersonation, so domains with SPF but not DMARC (or with a DMARC policy of “none”) can still easily be spoofed by malicious actors or spammers seeking to impersonate them.
Clearly, campaigns and PACs have a ways to go before they can be free of spoofed emails that purport to come from their domains. Spoofed emails are already a minor issue in the election. How long until they become a major issue?
Valimail will be releasing our full research report on the state of email security in the U.S. election infrastructure later this week. Follow Valimail on Twitter for the latest updates, and stay tuned!
To download the full report, click here: 2020 Election Infrastructure Remains Vulnerable to Email Hacking.