Email impersonation isn’t just an IT problem. It’s a silent storm, quietly brewing and eroding your brand’s reputation, customer trust, and financial stability. It’s no longer a question of if cybercriminals will target your brand—it’s a matter of when.
Imagine: Your customers receiving emails that (on the surface) appear to be from your brand. They trust these messages, click on them, and unknowingly walk into a cyber trap. This isn’t a hypothetical scenario. This is email impersonation, and it’s happening every single day online.
You’re already taking the first step toward defending against email impersonation by reading this article. Taking a proactive approach can help prevent successful attacks and mitigate damage to your brand.
Below, we’ll cover what email impersonation entails, why it’s a threat in 2025, and (most importantly) how to protect your brand by implementing smart, robust defenses against it.
What is email impersonation?
Email impersonation is a deceptive tactic cybercriminals use to trick victims into believing they’re a trustworthy entity when they’re not. They use this trust to get customers and employees to take actions like sharing sensitive information, clicking on malicious links, and transferring funds.
It’s a prevalent form of cyberattack that exploits the inherent trust we place in our inboxes and the people (and businesses) we communicate with.
Email impersonation isn’t a new phenomenon, but it has been rising significantly in recent years. The surge in remote work and the global shift towards digital communication have made it easier for cybercriminals to exploit vulnerabilities and conduct sophisticated impersonation attacks.
And these attacks are nothing to dismiss. Successful attacks can hurt your brand and lead to the following:
- Financial Loss: Directly through fraudulent transactions and indirectly through remediation costs.
- Reputational Damage: Diminishing customer trust and tarnishing the brand image.
- Legal Consequences: Especially if customer data is compromised and regulatory compliance is breached.
Different types of email impersonation attacks
Understanding the different forms of email impersonation attacks helps you develop better prevention strategies. While attacks evolve and change over time, here are the most prevalent impersonation attempts as of 2025:
- Sender Name Impersonation: The attacker uses a display name that mimics a legitimate entity, hoping the recipient won’t check the actual email address.
- Domain Spoofing: The attacker uses a domain that closely resembles the legitimate domain, often by changing or adding a letter.
- Look-alike Domain Attacks: The attacker registers a domain that visually resembles the targeted domain, using it to send seemingly legitimate emails.
- Compromised Email Account Attacks: The attacker gains access to a legitimate email account and uses it to send malicious emails.
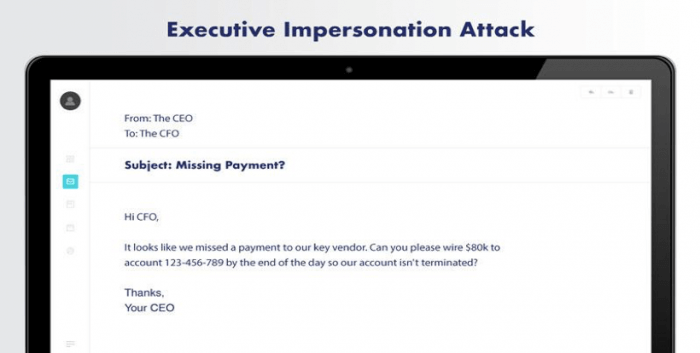
- Business Email Compromise (BEC): The attacker impersonates a high-ranking official within the organization, often targeting employees with access to financial resources.
- Whaling: A subset of BEC, where the attacker targets top executives, exploiting their access and authority.
- Man-in-the-Email Attack: The attacker inserts themselves into an existing email thread, often during a transaction process, to divert payments or steal information.

How to stop email impersonation
Knowing the threat is one thing—but learning how to stop an impersonation attack is a whole other ordeal. While attacking tactics change from time to time, we’ve found the following best practices to be the best defense against email impersonation.
We know you’re busy, but preventing a cyberattack is much easier than recovering from it. Implement these prevention mechanisms as soon as possible to protect your brand and stop an impersonation attack.
1. Take advantage of DMARC, DKIM, and SPF
Implementing email authentication protocols can safeguard your brand against domain spoofing and phishing attacks:
- Domain-based Message Authentication, Reporting, and Conformance (DMARC): DMARC is an email authentication protocol designed to give email domain owners the ability to protect their domain from unauthorized use, commonly known as email spoofing. It leverages SPF and DKIM authentication mechanisms and provides a policy for handling emails that fail authentication, along with reporting capabilities to improve and monitor email protection.
- DomainKeys Identified Mail (DKIM): DKIM allows senders to associate a domain name with an email message by adding a digital signature to the email headers. This signature is validated against a public cryptographic key in the sender’s DNS records to prove that the email wasn’t altered during transit.
- Sender Policy Framework (SPF): SPF is an email authentication method that detects and blocks email spoofing by providing a mechanism to allow receiving mail exchangers to verify that incoming mail from a domain comes from an IP Address authorized by that domain’s administrators. It works by defining a policy that specifies which mail servers are permitted to send email on behalf of a domain.
Getting all this set up can take a bit of time—that’s why we created Valimail Enforce. It accelerates your journey to DMARC enforcement with world-class automation, all without any manual SPF, DKIM, or DNS configuration on your end.
2. Study the latest cyberattacks
Keep up to date on the latest cyberattack trends and tactics to help you anticipate and prepare for potential threats. Cybercriminals continually evolve their strategies, exploiting new vulnerabilities and devising sophisticated attack mechanisms.
Regularly reviewing cyber threat intelligence and participating in cybersecurity forums and communities can provide insights into emerging threats and preventive strategies. Staying proactive ensures your defense mechanisms are always one step ahead of the bad guys.
3. Use multifactor authentication
Multifactor Authentication (MFA) adds an additional layer of security by requiring multiple forms of verification before granting access. Even if a cybercriminal obtains user credentials, MFA prevents unauthorized access by requiring a second form of identification, such as a temporary code sent to the user’s phone.
Implementing MFA across all email accounts and sensitive data access points significantly enhances your cybersecurity posture.
4. Train your employees
Employees are often the first line of defense against email impersonation attacks. Provide them with regular training sessions that educate them on recognizing and responding to phishing and impersonation attacks.
Simulating phishing attacks can also help assess their preparedness and identify areas requiring additional training, ensuring they can effectively intercept real-life impersonation attempts.
While training your employees is important, the best defense is stopping these emails from ever getting into the inbox. This is where DMARC comes in.
With the use of Enforce, Valimail helped customer Travers Smith get to DMARC enforcement in 90 days to block an average of 95,000 phishing emails a month to secure their email communication.
“Prioritizing our DMARC implementation with our management team was easy once we explained the risk and how we could eliminate the risk – and protect the Travers Smith brand, our customers, employees, and partners.”
Darragh Macken, Head of Information Security at Travers Smith
5. Monitor for cyberthreats
Continuous monitoring for cyber threats enables you to promptly detect and respond to potential attacks. Employing threat detection tools and establishing a cybersecurity response team helps you swiftly identify and mitigate threats, minimizing potential damage.
Monitoring should also include keeping an eye on domain registrations similar to your company’s to detect potential impersonation attempts.
We offer Valimail Monitor as a free service to everyone. It provides a seamless monitoring solution, pinpointing your services by name and removing the complexities of manually deciphering raw IP data in DMARC reports. Quickly recognize and authorize all senders, highlight potential threats from malicious actors, and initiate DMARC enforcement with Monitor.
6. Perform regular audits and simulated attacks
Conduct regular cybersecurity audits to assess the robustness of your defenses. Simulated attacks test the practical application of your security policies and the readiness of your team, revealing vulnerabilities in a controlled environment. These practices help refine your security protocols and enhance your preparedness for actual cyberattacks.
7. Mitigate the impact
Remember, attacks will happen. And, unfortunately, some might breach your defenses. When they do, you need a well-defined incident response plan to manage the threat and mitigate the damage.
This involves identifying the breach, containing the threat, eliminating the cause, and recovering data and systems. Post-incident analysis provides insights into improving your defense mechanisms and preventing recurrence.
8. Adopt BIMI
Brand Indicators for Message Identification (BIMI) allows brands to display a logo next to their emails, providing a visual verification of authenticity. BIMI works in conjunction with DMARC to guarantee that only authenticated emails show the brand logo in the recipient’s inbox.
This enhances brand visibility and provides an additional layer of verification, strengthening customer trust and reducing the likelihood of successful impersonation.

Prevent email impersonation with Valimail
The email impersonation threat isn’t going away—it’s only evolving. And so should your email security solutions.
Enter Valimail Monitor.
Valimail Monitor provides a straightforward and efficient way to identify your email services by name and understand the insights hidden within your DMARC reports. It’s free to use, and you can get started today.
Start your journey for email impersonation protection with Valimail to keep your brand’s communication secure, authentic, and trusted by your stakeholders. Let’s make email secure together.


