For many businesses, “security awareness” is a term used to describe both its employees’ knowledge that protecting a company’s physical and information assets is important, and their ability to do so. Much of the periodic security training that employees receive is designed to ingrain and enhance security awareness among the staff, and that training is often focused on electronic threats like phishing and spoofing that cost businesses many millions of dollars every year.
While such training is at least partially successful, even if it were 100% effective it still would only be part of the overall defensive posture needed to protect a company’s domain and the business’s reputation.
Domain-based Message Authentication, Reporting, and Conformance (DMARC), is an email protocol designed to prevent what’s known as “exact domain spoofing.” With DMARC in place and properly configured, the use of a domain in an email message’s visible “From” header can be verified as authorized or not by the site receiving the message, like Gmail, Yahoo, or Microsoft.
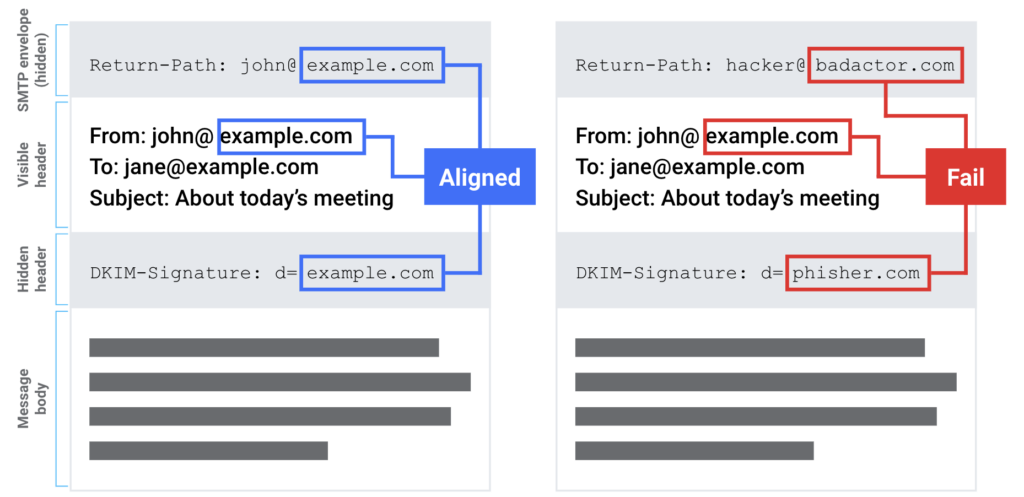
If usage of the domain is not authorized, the receiving site will have information available to it to help it make a decision on how to handle the message. Unauthorized emails are generally rejected or at least placed in the recipient’s spam folder. This makes DMARC a critical tool in stopping some kinds of phishing attacks, specifically those that rely on spoofing a domain in an attempt to make the recipient trust the email message and act on its contents.
In the remainder of this article, we’ll discuss how DMARC can augment and enhance your employees’ security awareness to better protect your domain.
Getting started with DMARC – publish a DMARC policy record
DMARC policy records are published in DNS as TXT records. A domain that publishes a DMARC policy record is announcing to the rest of the internet:
“Use of our domain in the visible From header should be authenticated. If you see messages using our domain name that isn’t passing authentication checks, we’d like you to dispose of it either by delivering it to spam or outright rejecting it. Also, please send periodic reports about all uses of our domain to one or more email addresses.”
A basic DMARC DNS record would look something like this:
domain.com TXT “v=DMARC1; p=quarantine; rua=mailto:dmarcReports@domain.com;”The above contains three key-value pairs:
- (v=) refers to the version of DMARC protocol identified in the record. There is only one version of DMARC at present, but there could be additional versions in the future.
- (p=) refers to the policy the domain owner is requesting for handling email that doesn’t pass authentication checks. The choices for p values include:
- None – no special treatment
- Quarantine – deliver to spam
- Reject – reject the message
- (rua=) refers to an email address that will accept specifically formatted messages sent by sites that do DMARC validation that will allow the domain owner visibility into email streams using their domain and identify any possible shortcomings in the domain’s authentication practices.
Typically a domain will publish a DMARC policy record with p=none until it’s sure that all email it sends is authenticated, after which it’ll upgrade to p=quarantine or p=reject.
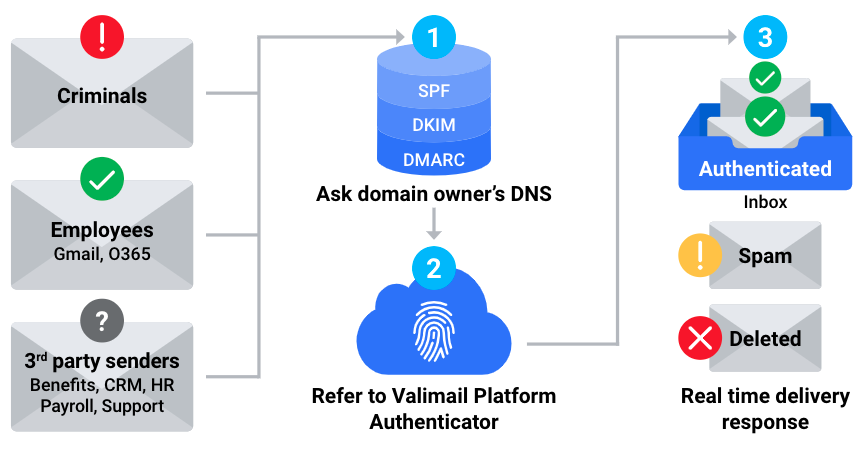
Proper DMARC authentication also relies on two other email protocols – SPF and DKIM. To learn more about how they relate and impact email deliverability, check out or post DKIM vs. SPF: Understanding the Difference to Improve Email Deliverability.
Full DMARC participation – check inbound email
Publishing a DMARC policy record, especially one with a policy of quarantine or reject (what we at Valimail refer to as “at enforcement”), ensures that the use of your domain in email messages can be verified as authorized. However, this does nothing to protect your own employees from receiving email that might be making unauthorized usage of a domain, including spoofing your own domain.
For that, you have to take the next step and ensure that email inbound to your domain is subject to DMARC validation checks and that domain owners’ policies are applied as requested.
The methods for doing this will vary based upon the application being used to host a domain’s email, and for cloud hosts such as Microsoft 365 and Google Workspace. It is important to any domain owner to understand that publishing a DMARC policy by itself is not enough to fully protect the domain’s unauthorized usage in email messages; the domain must also perform DMARC validation and enforcement on inbound email, including messages using its own domain.
Inviting everyone to the party – vendors, clients, and partners
Publishing a DMARC policy record is a way for a domain owner to prevent unauthorized usage of its domain on messages sent to sites that do DMARC validation on inbound email; it has no effect on messages sent to sites that don’t do DMARC validation and enforcement. Likewise, DMARC validation on inbound email has no impact on messages that spoof domains that don’t publish DMARC policy records.
What this means is that even if you take steps to protect your domain and your employees by publishing a DMARC record and doing DMARC validation, you’ll still be vulnerable to attacks that spoof other domains in your supply chain, such as your vendors, clients, and partners.
For example, DMARC validation won’t stop a spoofed message crafted to look like an invoice from one of your suppliers and sent to your accounting department seeking payment unless your supplier’s domain also publishes a DMARC policy record for its domain(s). That supplier will be just as vulnerable to messages spoofing your domain unless they are performing DMARC validation on all email inbound to them.
In order to enjoy the full benefits of DMARC for the entire supply chain, domain owners should insist that any organization they do business with engage in full DMARC participation. This will include not only publishing DMARC policy records for any domains used to send email to the domain owner, but also performing DMARC validation on all inbound email.
DMARC can’t be the only solution either
Even though full participation in DMARC can augment the security awareness of your employees to protect them against external threats, it’s not enough by itself. DMARC is designed to stop “exact domain spoofing.”
This means that if “company.com” fully participates in DMARC, the domain “company.com” is protected against unauthorized usage in email messages. This does nothing to guard against the usage of a domain such as “C0MPANY.COM”, where the first letter ‘o’ is replaced by a zero, to attempt to fool recipients into believing that they’re receiving a message from “company.com.” (Domain names are case-insensitive, so COMPANY.COM and company.com are identical.)
A domain owner with unlimited time and resources could register all possible permutations of lookalike domains (along with all possible domain names mentioning their domain) and publish DMARC records for all of them, but that’s not a solution that’s likely to scale.
Instead, the best solution for a domain owner to employ the best possible defenses against this kind of spoofing is to insist on deploying effective anti-spam and other filtering mechanisms in their inbound email streams. As with DMARC validation, cloud-based hosting providers already do this (and do it well), but those domain owners hosting their own email would be wise to look into obtaining tools to do this, along with augmenting their security awareness training to ensure that employees don’t think they’re smarter than the filters.
One of the ways an organization could do this is by working with an email security company like Abnormal to prevent malicious inbound email.
To be sure, filters aren’t perfect, but they’re right much more often than they’re wrong, and it only takes one employee overriding one correct filter decision to bring disaster to a company. Employees should have a process for challenging filter decisions in the event of a mistake on the part of the filter, but no employee should have the sole right to override them.
Conclusion
Security awareness is a key component of any company’s defenses against its employees becoming victims of phishing at work, but it’s not enough by itself. Full participation in DMARC up and down the supply chain, along with anti-spam and other filtering on inbound email, are crucial to a full suite of defenses against this threat.
If you’re ready to get started on publishing a DMARC record for your domain(s), contact Valimail today.
