How to verify email sender identity: Complete guide for 2025

Learn the greatest threats to your email communications and how to better verify email sender identity to protect your business and customers.
3 types of dangerous email impersonation attacks to beware
Learn everything you need to know about the latest email impersonation attacks to better protect your business, employees, and customers.
Email fake senders: How bad are fake sender identity issues?

Learn how attackers use fake email senders to impersonate your brand to maliciously target your business, employees, partners, and customers.
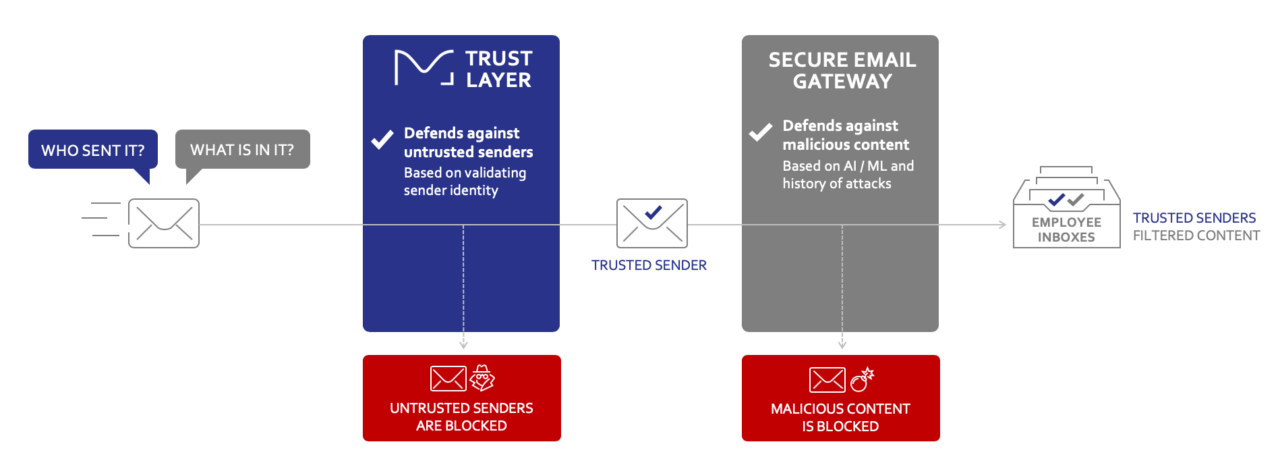
Why email needs a zero-trust security model

Email needs a new approach to stopping bad actors: zero trust focuses on allowing good email rather than attempting to identify and block fraud messages.
The who and what of email security
[Sassy_Social_Share] In the days of circuit-switched telephony, when Grandma dialed Grandpa, the phone company could easily determine that the caller’s identity was, in fact, Grandma. Such confidence melted away, however, with TCP/IP and the Internet. That is, when Kahn and Cerf decided to allow senders, instead of the network, to specify their identity, they created […]
Using sender identity to stop phishing and trust your email again
When it comes to defense against the dark arts of phishing, Valimail thinks a little differently than everyone else. Our contrarian point of view is that it’s better to create a definitive list of friends than try to guess who might be a foe. After all, how do you host a party? Do you open […]