- Guide
How to Fix the Error “No DMARC Record Found”
Domain-based Message Authentication, Reporting & Conformance (DMARC) is a framework for authenticating email by using Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) to verify the use of the domain in the visible “From:” header. The error “no DMARC record found” means that DMARC is not configured for a domain.
Different software tools might return different error messages when a DMARC record hasn’t been configured.
For example:
-
- “DMARC not at Enforcement”
-
- “No DMARC record published”
-
- “DMARC record not found”
-
- “DMARC record of [domain] is not found”
To fix this problem, you’ll need to set up DMARC properly for your domain. We’ll help you do that in this article.
Correct DMARC setup is about more than just making an error message go away, though. Email is a prime method for attackers to target you and your organization.
According to a report from Verizon, scammers deliver 94% of malware through email, and that’s just the tip of the iceberg. Whether it’s spam campaigns spoofing your domain and tanking your organization’s reputation or phishing attacks stealing trust by sending from a “trusted” address within your network, setting up DMARC bolsters your domain’s email security.
Below, we’ll provide a step-by-step guide to deploying DMARC on a live domain. Additionally, we’ll touch on a few limitations of DMARC to be aware of so your expectations are realistic.
How to fix “no DMARC record found”
Fixing a “no DMARC record found” error is simpler than you might think. First, confirm the error actually exists using a free tool like Valimail’s Domain Checker. If your domain truly lacks a DMARC record, you’ll need to create one.
Start with a basic DMARC record like this:
v=DMARC1; p=none; rua=mailto:dmarc@yourdomain.comThis minimal record sets you up in monitoring mode (p=none) and directs reports to your specified email. Add this as a TXT record to your DNS settings at the location _dmarc.yourdomain.com.
Don’t have SPF or DKIM set up yet? Take care of those first—DMARC needs at least one of them to work properly. Most domain hosts offer simple interfaces for adding these DNS records.
Once you add your DMARC record, verify it’s live by checking again. DNS changes can take up to 48 hours to propagate, so be patient if it doesn’t appear immediately.
Want to take it further? Once you’re comfortable with the monitoring data, gradually move toward enforcement with p=quarantine and eventually p=reject.
Need more handholding? We have more step-by-step details later in the post. Keep reading!
Other DMARC Issues and Fixes
While setting up DMARC, it’s possible to make mistakes along the way that cause yet more errors! You can consult the table below in case that happens, to help you figure out what’s going wrong.
| Common DMARC Issue | How to Fix It |
|---|---|
| No DMARC record found | The domain’s DNS does not contain a DMARC record. Define a policy and add it as a TXT record to your domain’s DNS configuration. |
| Invalid DMARC policy | A record was found, but the syntax is incorrect. Debug your policy and find the syntax mistake. |
| DMARC alignment failure | This error applies to emails that “failed” the DMARC policy because the email was fraudulent, the DMARC policy was too strict, or SPF and/or DKIM were too strict. |
| Missing SPF or DKIM record | DMARC can be deployed by itself, but in practice, it depends on SPF and DKIM to enforce “From:” header alignment and power reports. |
To learn more about the underlying issues that lead to other errors, check out the article 7 common mistakes people make with DMARC.
How DMARC Works
To deploy a DMARC record and fix this error, it’s helpful to first have a basic idea of what DMARC does and how it works.
DMARC validates the use of the domain in the visible From: header by requiring that either SPF or DKIM pass and that the domain used in SPF or DKIM aligns with the From: domain.
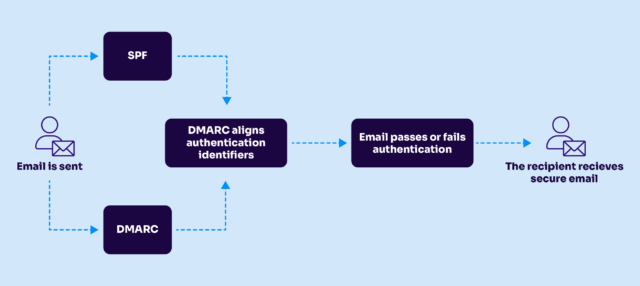
DMARC uses SPF and DKIM to verify the visible From: address in an email
DMARC also offers functionality to suggest what recipients should do when they receive mail from your domain that fails DMARC. Furthermore, you can publish an email address for other servers to send periodic reports to about emails sent using your domain that have passed and failed DMARC checks.
To access your domain’s DMARC policy, receiving servers look it up in DNS. DMARC policies appear as TXT records at the _dmarc subdomain. For example, we can lookup the DMARC record for Uber using the nslookup command like so:
nslookup -type=txt _dmarc.uber.com
Server: 10.240.80.238
Address: 10.240.80.238#53
Non-authoritative answer:
_dmarc.uber.com text = "v=DMARC1; p=quarantine; rua=mailto:dmarc_agg@vali.email"Looking at a DMARC policy can seem intimidating at first. To learn more about what each tag means, check out our article What is DMARC.
Fixing the Error “No DMARC Record Found”
Addressing this error requires two steps. First, you must check to confirm that the DMARC record actually is missing. If it is, then you must publish a DMARC policy for your domain. In this section, we’ll help you do both.
Confirming the error
To verify that no DMARC record exists for your domain, you can look up your domain on Valimail’s Domain Checker. If no DMARC record exists, you’ll see an error message like this:
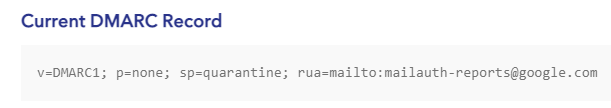
To address this error, you’ll need to set up a DMARC record. Before that, though, you’ll want to have SPF or DKIM in place.
Deploying DMARC
First, you will want to set up SPF and DKIM. How to go about this depends on your mail provider, which is also true for setting up DMARC. For example, for Office 365, you can follow the instructions in our article, DMARC Office 365.
Once you have SPF and DKIM in place, you can begin to craft a DMARC policy. You can do this by following our visual guide: A step-by-step guide to getting DMARC done right.
Finally, you’ll need to publish your DMARC policy as a TXT record at the _dmarc subdomain in your domain’s DNS. Once you’ve done this, you can check again with Valimail’s Domain Checker to confirm that the policy is live.

If you recently published the DMARC policy, it can take a while to become available due to the latency of DNS propagation. However, it should appear within 48 hours at the latest.
DMARC Limitations
So far, we’ve emphasized the positive contributions DMARC makes to your security. However, it’s not a panacea, and you shouldn’t treat it as such. It’s a great protocol, but it doesn’t solve everything.
|
Platform
|
Success Rate
|
Success Rate Frame
|
Estimated FTEs
|
Maintenance
|
Marketplace Apps Identified
|
|---|---|---|---|---|---|
|
DIY Manual
|
20%
|
12+ Months
|
2-3
|
Never ending
|
~100 services
|
|
Outsourced Manual
|
<40%
|
9-12 Months
|
1-2
|
Never ending
|
~100 services
|
|
Valimail Automation
|
97.8%
|
0-4 Months
|
0.2
|
Automated
|
6,500+
|
Consuming DMARC Aggregate Reports
Recall from the opening paragraph of this article that DMARC stands for Domain-based Message Authentication, Reporting & Conformance. The second-to-last word, “reporting,” refers to a feature of DMARC policies that gives you insight into DMARC alignment checks performed by other mail servers against your domain.
Gaining insight into what mail is failing can help fix bugs and raise awareness of recently attempted fraud against your domain. The reports arrive periodically as XML attachments to emails. They look like this:
<?xml version="1.0" encoding="UTF-8" ?>
<feedback>
<report_metadata>
<org_name>example-recipient.com</org_name>
<email>noreply-dmarc-support@solarmora.com</email>
<extra_contact_info>http://example-recipient.com/dmarc/</extra_contact_info>
<report_id>8782497923</report_id>
<date_range>
<begin>123557113</begin>
<end>123453224</end>
</date_range>
</report_metadata>
<policy_published>
<domain>yourdomain.com</domain>
<adkim>r</adkim>
<aspf>r</aspf>
<p>none</p>
<sp>none</sp>
<pct>100</pct>
</policy_published>
<record>
<row>
<source_ip>203.0.113.209</source_ip>
<count>2</count>
<policy_evaluated>
<disposition>none</disposition>
<dkim>fail</dkim>
<spf>pass</spf>
</policy_evaluated>
</row>
<identifiers>
<header_from>yourdomain.com</header_from>
</identifiers>
<auth_results>
<dkim>
<domain>yourdomain.com</domain>
<result>fail</result>
<human_result></human_result>
</dkim>
<spf>
<domain>yourdomain.com</domain>
<result>pass</result>
</spf>
</auth_results>
</record>
</feedback>
The report is easy to read manually because the tags are self-explanatory. However, it’s meant to be read by a program, and it’s much more efficient to use an automated solution like Valimail’s Domain Monitor to consume and process incoming reports.
To enable reporting, use the rua tag in your DMARC policy and point it to the email address where you’d like to receive reports. For example, to receive mail at dmarc_reports@example.test, you’d add rua=mailto:dmarc_reports@example.test.
For a real-life example of this, we can see how valimail.com enables reporting with the rua tag using the nslookup command:
nslookup -type=txt _dmarc.valimail.com
Server: 10.240.80.246
Address: 10.240.80.246#53
Non-authoritative answer:
_dmarc.valimail.com text = "v=DMARC1; p=reject; rua=mailto:dmarc_agg@vali.email,mailto:dmarc.reports@valimail.com"We see above that the Valimail record offers two reporting endpoints, separated by a comma.
The receiving mail server must enforce DMARC
DMARC only works if receiving hosts actually enforce it. In other words, if someone spoofs your domain, the receiving host has to check the DMARC policy for your domain to realize that the spoofed email is out of alignment and do something about it.
In other words, there’s nothing you can do to prevent spoofing of your domain for email sent to hosts that don’t enforce DMARC. This includes your own inbound mail servers. If you don’t validate and enforce DMARC on your inbound mail servers, then you’re not protected from messages spoofing your domain being sent to your domain.
DMARC Requires SPF or DKIM
To pass DMARC, the domain used by either SPF or DKIM aligns with the domain in the visible From: address. If you don’t have DKIM, then from DMARC’s perspective, DKIM always fails. The same is true for SPF.
If you don’t have either, then DMARC will fail every time. So, for DMARC to be useful, it’s necessary to have at least one of these two underlying protocols in place. Ideally, you can set up both and enjoy the additional benefits provided by each.
SPF Fail and Softfail
SPF has two failure modes: fail (often called “hard” fail) and soft fail. However, DMARC ignores this distinction, considering either failure to simply be a failure. Thus, when using SPF with DMARC, be mindful that this distinction won’t exist as far as DMARC is concerned.
To learn more about the subtle distinction between SPF’s two failure modes, read our article SPF Softfail vs Hardfail.
Reports Take Time to Receive
In theory, security monitoring could detect ongoing attacks by analyzing incoming DMARC reports. However, aggregate reports are only sent periodically, and email fraud tends to occur in very fast bursts. Thus, DMARC reporting is not adequate for detecting ongoing email fraud campaigns against your domain.

Minimal resource requirement with only a single one time DNS change needed

DMARC Enforcement guarantee and 97.8%+ success rate

100% Automated service discovery and 1-click validation
Taking Care of All Your DMARC Record Problems
DMARC is important because it helps mitigate fraudulent email impersonating your domain. Properly deploying DMARC will not only fix the “no dmarc record found” error but also make your domain more trustworthy and safe from attacks. Considering that the average cost of a spear-phishing attack on an organization is $1.6 million according to Infosecurity Magazine, preventing email abuse has become a financial necessity.
There are also, of course, limitations to the benefits provided by DMARC. As we discussed in the article, a DMARC policy only helps if you’ve also configured SPF and DKIM correctly. Furthermore, reports trickle in slowly, and you’ll want to use an external service to consume and analyze them.
Once you’ve properly configured a DMARC policy on your domain, the “no dmarc record found” error should no longer be a worry, and you can begin to enjoy the benefits offered by DMARC’s protection.
Explore the chapters:
- 1. Introduction – Email Security Best Practices
- 2. MTA-STS
- 3. DKIM Selector
- 4. DMARC vs DKIM
- 5. DMARC Office 365
- 6. SPF Failure
- 7. SPF Softfail vs Hardfail
- 8. What Helps Protect from Phishing
- 9. Fixing the Error “No DMARC Record Found”
- 10. DKIM Office 365
- 11. How to Configure DMARC Policy to Reject or Quarantine
Get started for free
with Monitor
Start your path to DMARC enforcement with a panoramic view of the traffic being sent on your behalf.
No trial offers, credit cards, or obligations.
Explore all Valimail
has to offer
Go one step further than visibility…Take action! Reach DMARC enforcement faster. Stay compliant with evolving sender requirements. All while protecting your brand.