What is DMARC?
Everything you need to know about email authentication
Learn how DMARC (Domain-based Message Authentication, Reporting, and Conformance) protects your brand and stops phishing at the source.

Table of Contents
91% of cyber attacks start with a phishing email, and nearly 90% contain no malware.
These types of attacks are typically socially engineered phishing, such as gift card scams, executive spoofing, account takeovers, business email compromise (BEC) or credential theft. They bypass traditional defenses by exploiting trust rather than code.
While there are many security solutions designed to keep your email domain and inbox safe, only one of them will stop it from even being delivered: DMARC. If your domain is not at DMARC enforcement, your domain is still vulnerable, and your email recipients are at risk.
If you’ve spent any time in the email space, you’ve likely seen the word DMARC tossed around. But exactly what is DMARC? How does DMARC work, and is it something you should be concerned about?
We’ve got you covered. Below, we’ll walk you through everything you need to know about DMARC, including what it is, how it works, and why you need it.
What is DMARC?
Domain-based Message Authentication, Reporting, and Conformance (DMARC) is a widely accepted email authentication policy and reporting protocol. When implemented at a reject policy, it ensures that the receiving domain can verify authorized use of the domain in the From: field and take action if the use is not authorized.
Need a simplified DMARC meaning or an analogy? Think of it this way: DMARC acts like a nightclub bouncer for your inbox.
Before anyone gets in, the bouncer checks their ID to ensure they are who they claim to be. If everything checks out, they’re allowed inside. If not, they’re turned away at the door.
DMARC does the same for email. It verifies the sender’s identity before the message reaches your inbox. If the email fails the check, it’s blocked, just like a fake ID at the club.

DMARC also includes a reporting mechanism. Email receivers tell the domain whether or not the email they received passed or failed authentication. The email domain owner’s DMARC record can specify where receivers should send reports. These reports give the DMARC vendor and email domain owners the ability to see who is using the domain to send email.
Domain owners can use the information in these reports to fine-tune their email authentication policy to permit only trusted senders to send emails from your domain.
Curious how industry leaders answer the question, “What is DMARC?”
“I would compare DMARC to the username and password that they use on a website. Even my grandparents know that there’s a username and a password. But when emails are sent around the world, DMARC is the way that we use usernames and passwords to authenticate emails behind the scenes. So I’d say that it’s comparable to that authentication process that you use online. But it’s the emails. And it’s how they talk to each other behind the scenes.”
Karl Mattson
CISO at Endor Labs
How does DMARC work?
For DMARC to work, the sending domain needs a DMARC record, and the receiving server needs to check for that record and see if the sender is authorized (DMARC records are stored as text records in the DNS (Domain Name System)).
Fortunately, billions of email inboxes worldwide now accept the DMARC standard, including 100% of those hosted by major email service providers such as Google, Microsoft, Yahoo, and AOL. 5.3 billion mailboxes worldwide—almost 80% of the global total—will enforce a DMARC policy if the sending domain has published one.
On the sending side, DMARC adoption is growing exponentially. Over 7.2 million domains are now publishing a DMARC record, giving those domains visibility and the ability to protect themselves from phishing and email impersonation.
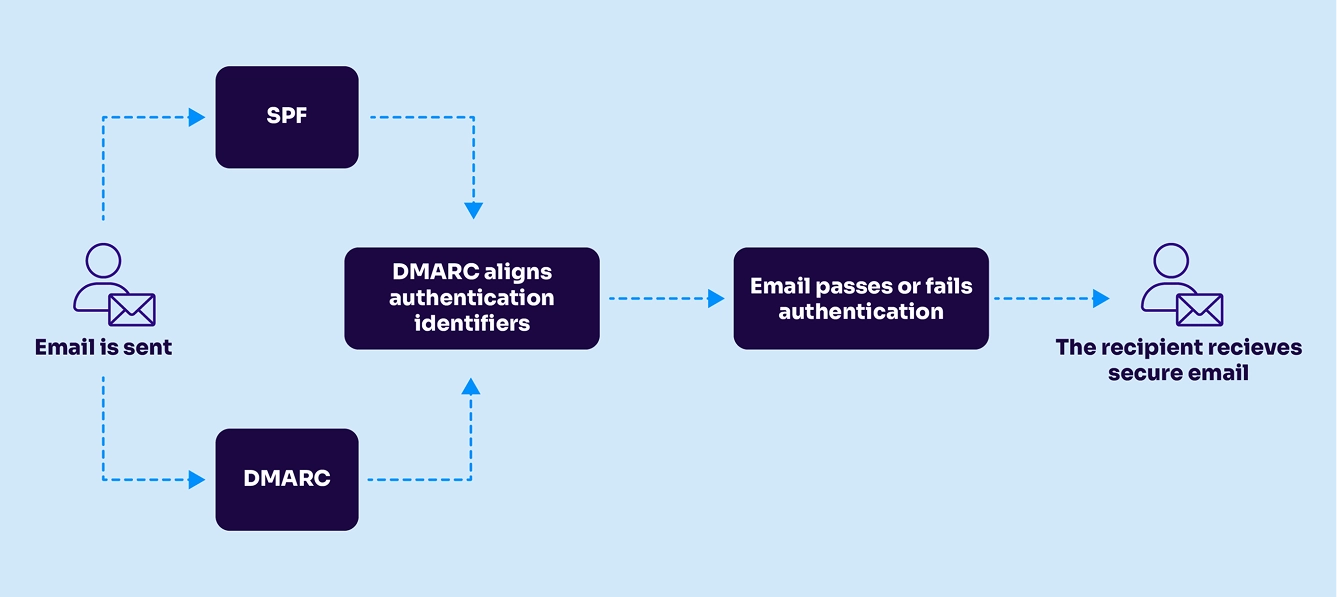
Here’s the step-by-step process for how DMARC works:
- Email is received for delivery.
- The receiver checks for an existing DMARC policy for the From: domain of the message.
- The receiver checks the authentication of the message using both SPF and DKIM by:
- Checking the sending IP of the message against the SPF record and/or
- Validating the message using the sender’s published DKIM key
- The receiver validates DMARC alignment for the message:
- If SPF authentication passes, and the domain checked aligns with the domain in the visible From, then DMARC passes and/or
- If DKIM authentication passes, and the domain checked aligns with the domain in the visible From, then DMARC passes.
- Otherwise, DMARC fails.
- If the email fails DMARC, receivers take action based on the policy specified in the domain owner’s DMARC record:
- Do nothing
- Send it to spam
- Reject it (delete it)
- Once a day, the receiver sends a report to the DMARC domain owner listing the authentication status for all email senders using that domain.
Do a DMARC check for free with our DMARC checker:
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Your Domain
Not protected AGAINST IMPERSONATION ATTACKS
DMARC NOT AT ENFORCEMENT
exampledomain1.com
Authentication Status for January 10, 2025
DMARC at Enforcement
SPF Record Configured
BIMI Ready
exampledomain1.com
Authentication Status for January 10, 2025
DMARC at Enforcement
SPF Record Configured
BIMI Ready
Why do you need DMARC for email?
Phishing and spoofing attacks are becoming more advanced and more complex to detect.
Bad actors increasingly target domains with weak or missing DMARC policies, using sophisticated techniques to impersonate trusted senders. These attacks include supply chain breaches, fake bank payment notifications, and spear phishing campaigns aimed at retailers and public sector organizations. Even nation-state actors have exploited gaps in email authentication to launch coordinated domain spoofing campaigns.
As these threats grow in scale and complexity, DMARC is an email security essential and works with layered secure email gateways (SEGs), making it more critical than ever for defending your domain against unauthorized use and protecting recipients from malicious email.
DMARC combats these threats by preventing the unauthorized use of a domain and ensuring that only legitimate emails are delivered to recipients.
In Q1 of 2025, over half a million domains within our dataset had newly published DMARC records, marking a substantial boost in adoption rates. At the start of 2025, we now observe that more than 7.2 million tracked domains have published a DMARC record.
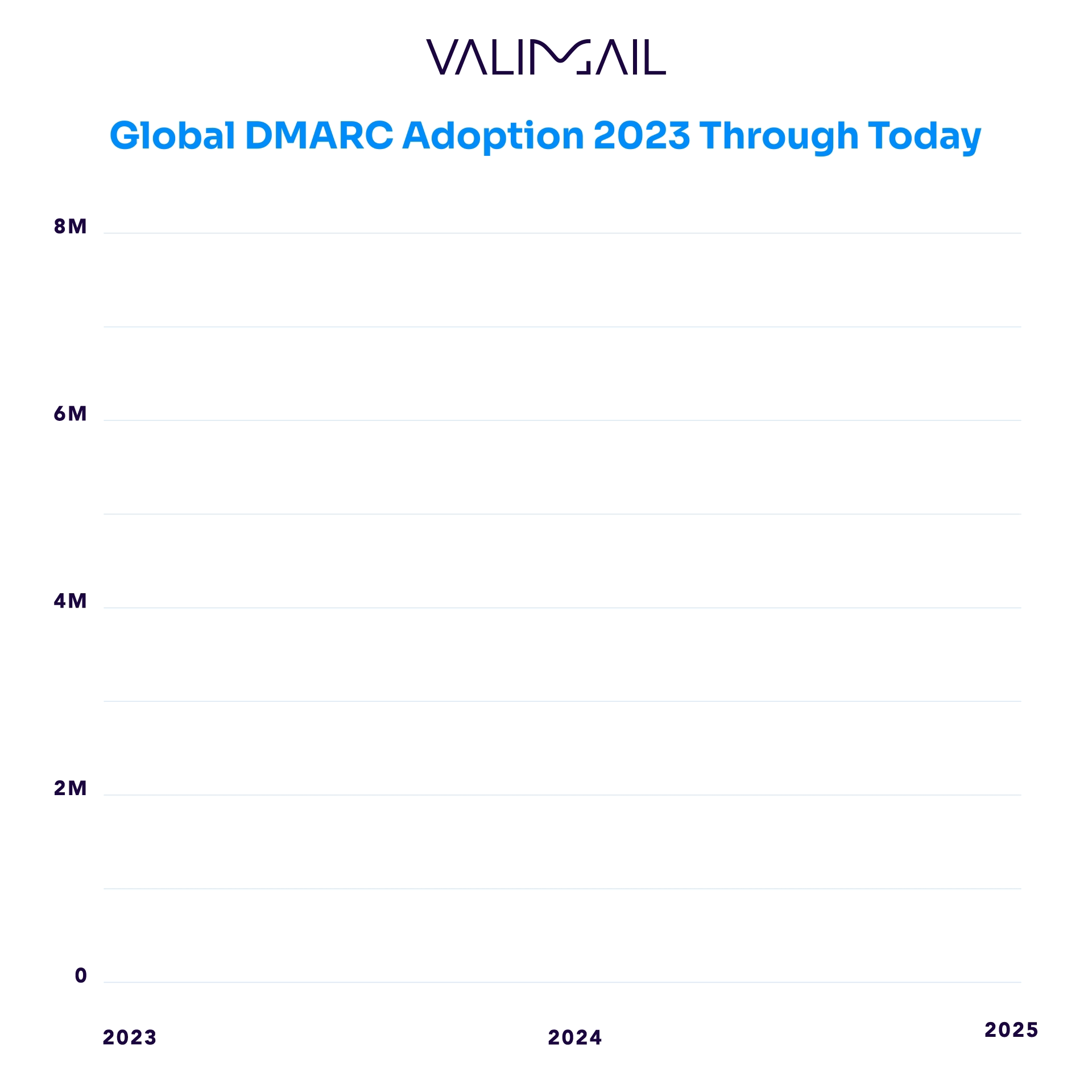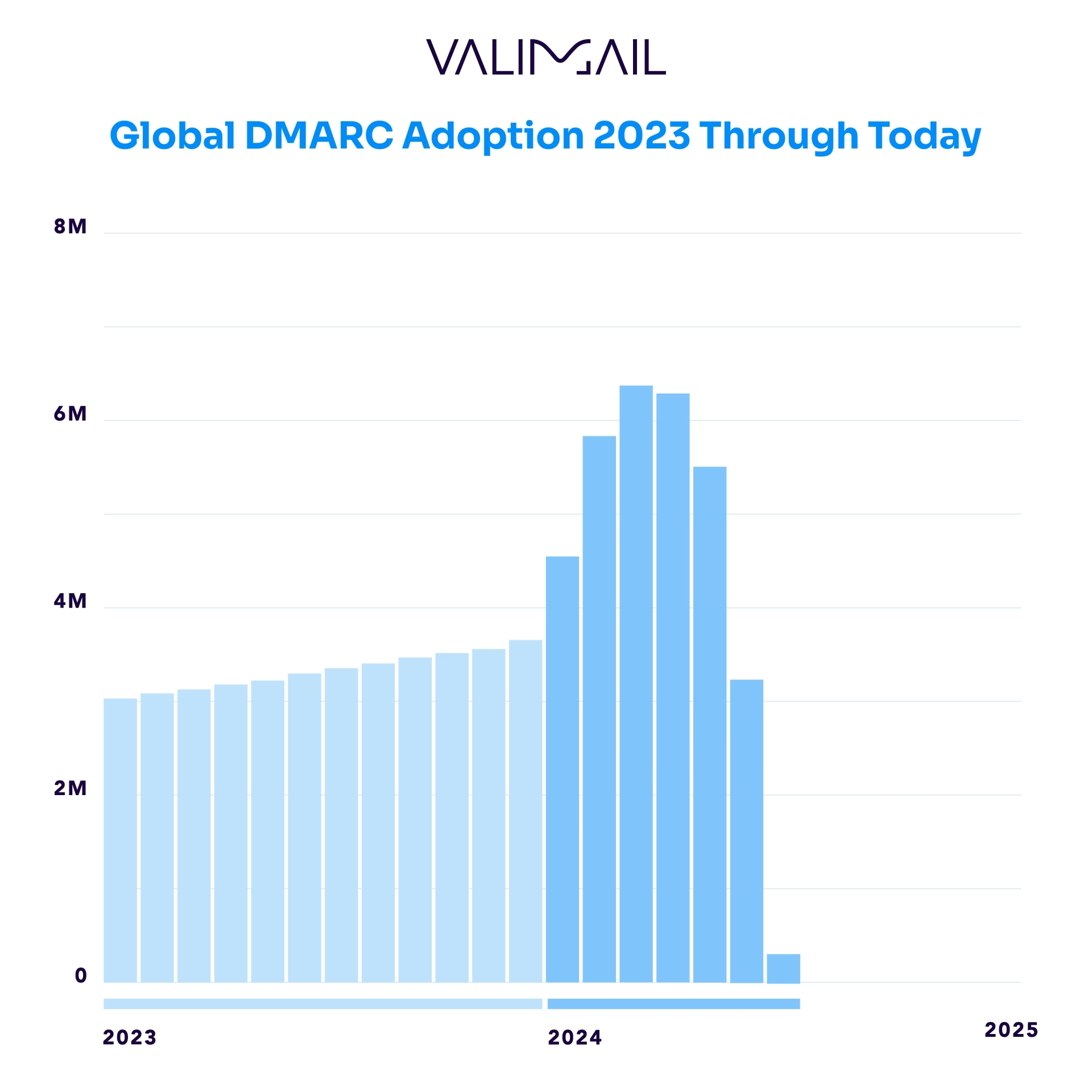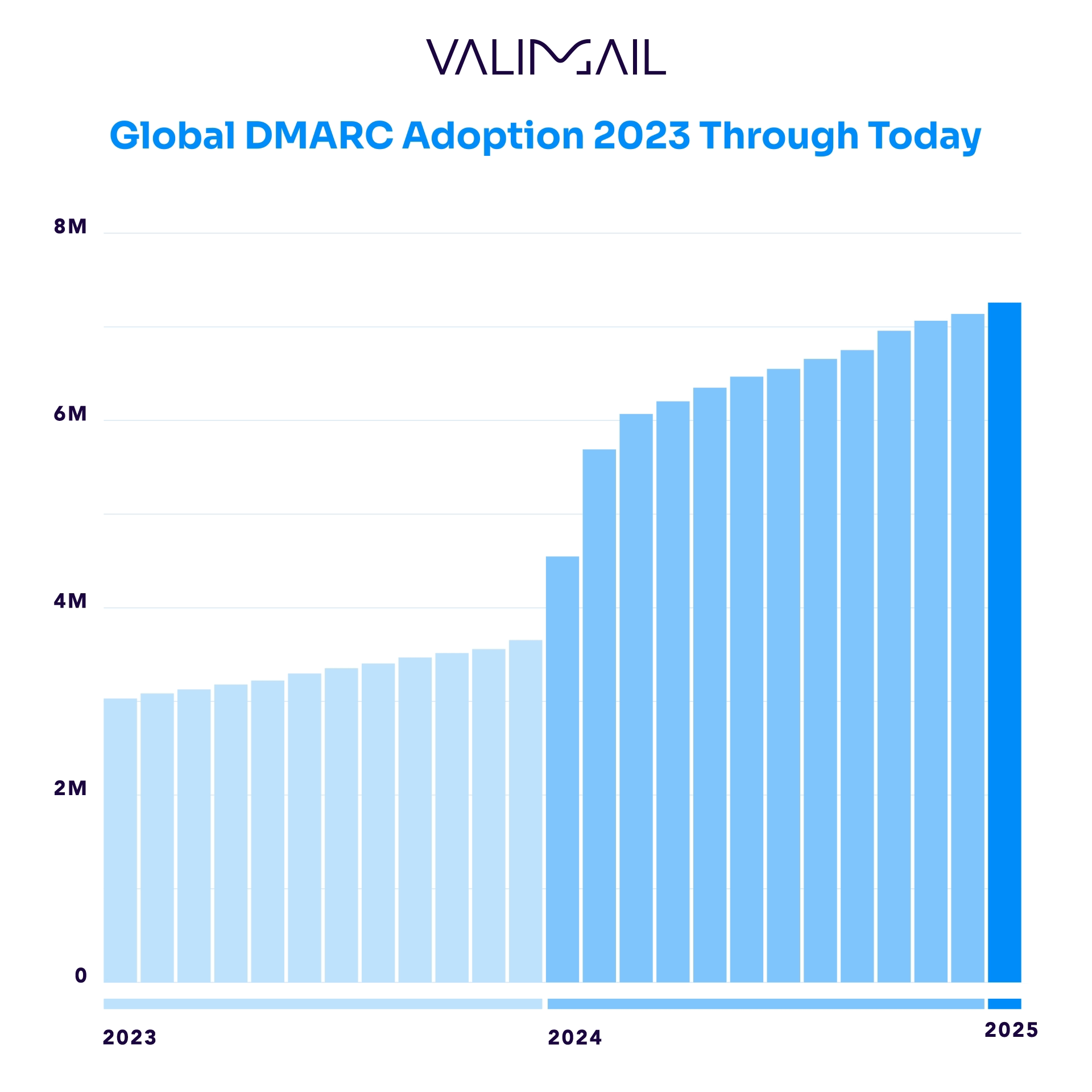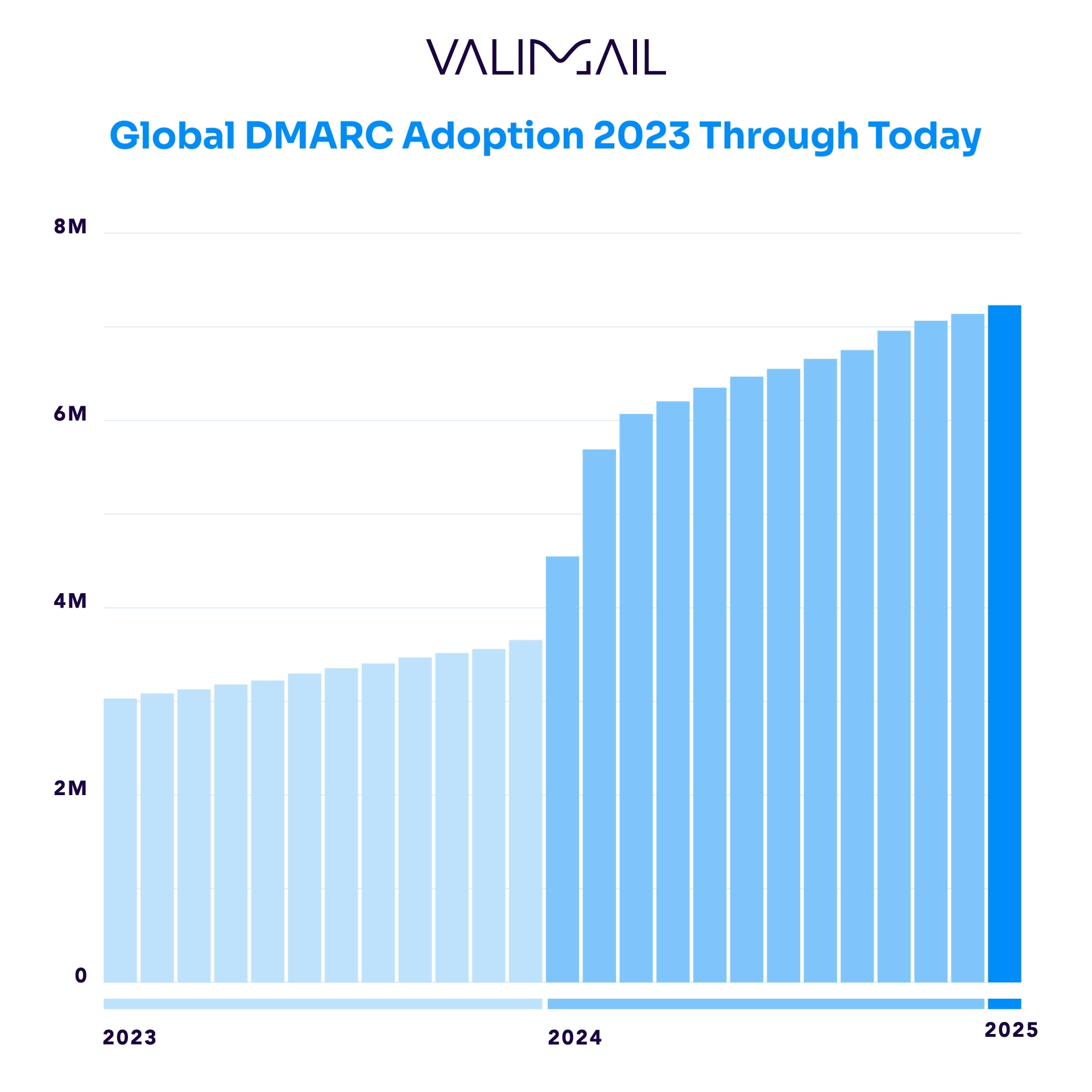

Industry DMARC adoption rates (as measured from the largest companies in each segment) ranged from 74% to 94%, with online retail leading the pack with the highest adoption rate and arts and recreation-related entities lagging significantly, with the lowest adoption rate.
What is DMARC enforcement?
When your domain is configured for DMARC and set to an enforcement policy, email recipients will be aware of your domain’s wishes to have any unauthorized messages rejected (blocked from delivery) or quarantined (moved to a spam folder), and will use that information when making message disposition decisions.
DMARC enforcement occurs when your DMARC record is properly configured and your policy is set to p=quarantine or p=reject. This means that any email that fails authentication will be isolated or blocked to prevent phishing.
DMARC enforcement is where DMARC delivers real protection and not just visibility. Valimail Enforce is an automated DMARC solution that can get you to DMARC enforcement and keep you there without all of the manual work and DNS edits.
What are the DMARC policies?
The three policies that can be set in a DMARC record are:
Policy | Definition | Message handling | Protection level | Risk exposure | Use case |
|---|---|---|---|---|---|
p=none | Monitoring only; no impact on message delivery | All messages are delivered, even if they fail authentication | No protection from spoofing
| High – spoofed emails still reach inboxes | Early stages of DMARC setup and collecting data |
p=quarantine | Partial enforcement; suspicious messages are treated cautiously | Messages that fail DMARC may be sent to spam/junk folder | Moderate protection | Reduced – spoofed mail may still be seen | Testing enforcement readiness and soft rollout |
p=reject | Full enforcement; only authenticated messages are delivered | Messages that fail DMARC are rejected (not delivered at all) | Strongest protection | Minimal – spoofed mail is blocked outright | Organizations ready to fully protect their domain |
A policy of none indicates that the domain owner wishes no specific action to be taken on unauthenticated email messages. But if the DMARC record includes a reporting address, the domain owner can use the data returned from email receivers to understand who is sending the email using that domain.
Pro Tip:
Not all DMARC policies offer the same level of protection.
Understanding the difference between none, quarantine, and reject is key to preventing domain spoofing. If your DMARC policy isn’t set to enforcement, your domain is still vulnerable.
How does DMARC compare to SPF and DKIM?
DMARC addresses shortcomings in the earlier email authentication protocols, SPF (Sender Policy Framework) and DKIM (Domain Keys Identified Mail). The biggest issue for both is that they have nothing to say about the email address in the From field of an email message.
Neither SPF nor a DKIM signature authenticates the sender against the “From:” field that users see. The policy specified in a DMARC record ensures “alignment” between the visible From: address and the DKIM signing domain or the SPF-verified sender, meaning they’re identical or at least part of the same DNS namespace.
This prevents phishers from using a false domain in the “From:” address while signing the message with an unrelated domain they control. This simple check provides an enormous amount of protection that never previously existed for email.
What is DMARC alignment?
DMARC alignment ensures that the domain in your email’s visible “From” field matches the domains authenticated by SPF or DKIM, so attackers can’t spoof your identity.
When an email is sent, DMARC checks whether the domain shown to recipients (the “From” email address) is aligned with the domains validated by the SPF and/or DKIM. If there’s no alignment, the message may fail DMARC authentication.
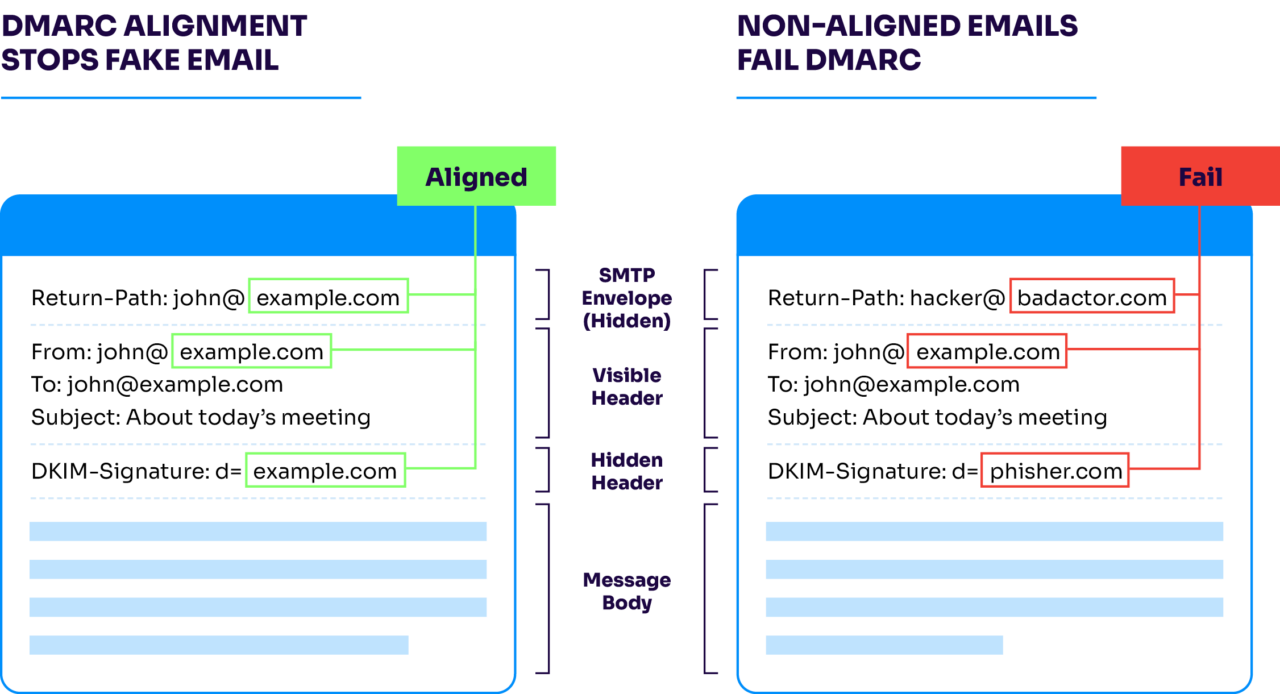
There are two types of DMARC alignment:
- Relaxed alignment allows subdomains (e.g., mail.example.com aligning with example.com).
- Strict alignment requires an exact domain match.
Alignment is a critical part of DMARC’s defense against exact-domain impersonation. Without alignment, bad actors can bypass SPF and DKIM protections to make emails appear as if they’re coming from a trusted brand.
What is a DMARC record?
DMARC records are stored in your email domain’s Domain Name System (DNS). This makes them instantly accessible to any mail server on the Internet.
A DMARC record is inserted as a TXT record alongside your other DNS records, with a name beginning with “_dmarc” followed by the domain to which the policy applies. For example, the DMARC record for “example.com” would be published at “_dmarc.example.com”.
DMARC record example
Here’s what a typical DMARC record looks like:
_dmarc.example.com IN TXT “v=DMARC1; p=none; rua=mailto:dmarc-rua@example.com”
Learn what pitfalls to avoid when handling your DMARC record:
Required DMARC tags
Here’s an overview of all the DMARC tags available in a DMARC record.
It looks complicated, but we can easily boil it down to the essential DMARC tags you need:
Only three tags are required in order to effectively use DMARC:
- v= (Only the “v=DMARC1” tag is case sensitive)
- p=
- rua=
Tags v= and p= must be set as the first and second position. All other tags are optional and can be placed in any order.
Primary domain policies apply to subdomains unless a subdomain policy is explicitly defined. You may have one and only one DMARC TXT record on a domain or subdomain—multiple records are treated as if there is no DMARC record at all.
Get these three tags right, and you’ll be able to take advantage of the visibility, control, and anti-phishing benefits that DMARC has to offer. The remaining DMARC tags you can ignore unless you have specific needs. These are the essential ones:
1. “v=DMARC1” (DMARC version)
Identifier of a DMARC record. “I’m a DMARC record, and you can use me to discover policy.”
2. “p=” (policy)
The “policy” tag indicates the domain owner’s preference for handling a message that fails DMARC authentication. There are three values:
- “p=none” – receiver takes no action
- “p=quarantine” – the domain owner wishes the message to be treated as suspicious and delivered to the spam/junk folder.
- “p=reject” – the domain owner wishes the message to be rejected.
Reject Email
Quarantine Email
3.“rua=mailto:address@company.com”
Tells the receiver where to send the DMARC Aggregate reports.
Aggregate reports provide the most valuable information provided by DMARC. They contain daily summaries of all the senders worldwide using your domain and their authentication status.
Note: To get DMARC’s visibility benefit, you must define a reporting address.
A p=none record with no DMARC reporting is the same as no record at all.
Completely optional DMARC tags
In most cases, a well-formed DMARC record only needs the three required tags mentioned above. The remaining tags can be ignored in most cases, but can be helpful in some situations:
- sp
- adkim
- aspf
- pct
- fo
- rf
- ri
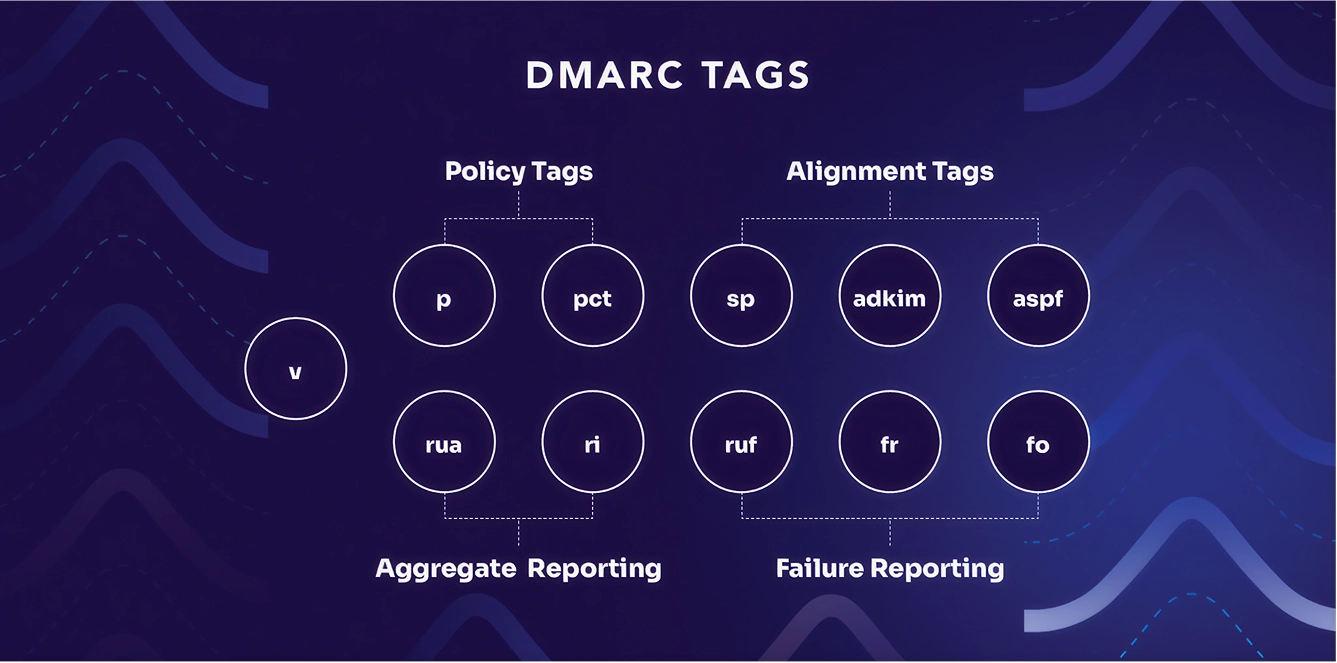
Here’s what the optional DMARC tags do:
sp: Defines the policy for subdomains
Subdomains will inherit the parent policy by default.
In general, you want your domains and subdomains to be covered by the same policy, so this tag isn’t needed unless you have subdomains that need different policies than the parent domain.
adkim: Indicates strict or relaxed DKIM identifier alignment
The default is relaxed. With a relaxed policy, DMARC alignment will pass if the organizational domains in the visible From and what is authenticated by DKIM. With strict alignment, a message that authenticates as email.example.com would fail DMARC alignment if the visible From was @example.com instead of @email.example.com.
aspf: Indicates strict or relaxed SPF identifier alignment
The default is relaxed. With a relaxed policy, DMARC alignment will pass if only the organizational domains in the visible From and what is authenticated by SPF match. With strict alignment, the subdomains also need to match: For example, a message that authenticates as email.example.com would fail DMARC alignment if the visible From was @example.com instead of @email.example.com.
pct: Percentage of messages to which the DMARC policy is to be applied
The default value for DMARC pct is 100, so all messages are subject to the policy. Changing the percentage to anything less than 100 allows imposters to bypass your specified policy. For instance, at 80 percent, you’ll have no control over which 80 percent of the messages will be subject to the policy.
ruf=mailto:address@company.com
Tells receivers where to send DMARC failure reports. If not specified, receivers will not send failure reports.
Failure reports are generated each time a message fails authentication. They may include the full contents of the failing email and, therefore, may include personally identifiable information (PII). Because of the risk of PII exposure, none of the major mailbox providers (e.g., Google, Microsoft, Yahoo, etc.) generate these reports anymore.
How to use DMARC reports
A DMARC report can provide global visibility into senders using your domain and their authentication status. DMARC also allows domain owners to express a preference for what mail servers should do with unauthorized emails.
We recommend only using aggregate reports, which are XML documents containing IP addresses, domain names, and authentication information for emails the receiver has seen sent as that domain. These XML reports can be thousands or hundreds of thousands of lines long, depending on how many email messages are sent using the domain around the world.
DMARC aggregate reports contain no direct information about the service that sent the email (e.g., Salesforce, MailChimp, ADP), so it is up to the domain owner to figure this out for themselves.
Pro Tip:
Valimail takes the complexity out of DMARC reporting.
Instead of combing through unreadable XML files, Valimail parses, organizes, and presents your aggregate data in a clean, human-readable dashboard. You’ll see which services are sending on your behalf, how they’re performing, and where issues exist—no guesswork or spreadsheets required.
What are the benefits of DMARC?
DMARC offers many benefits for the email ecosystem and your domain and delivers measurable business value.
DMARC can stop exact-domain spoofing, improve email deliverability, and build trust with customers, partners, and inbox providers. It’s one of the highest ROI investments you can make and offers a foundational layer for zero trust security.
“Outcomes show that implementing DMARC is one of the highest ROI solutions available. Just make sure to insist on enforcement (activation) and that the process is automated – otherwise, DMARC can be daunting.”
Alexander García-Tobar
CEO at Valimail
Some of the DMARC benefits include:
- Stopping brand impersonation
- Improving email deliverability
- Protecting brand reputation
- Enabling visibility and control
- Ensuring you’re DMARC compliant and strengthening risk posture
- Maximizing ROI with DMARC automation
- Reducing cybersecurity insurance
Implementing email authentication with DMARC (and its challenges)
Working towards DMARC enforcement should be the end goal of any organization that sets a DMARC record in DNS. The journey to enforcement is a multi-step process that involves four main tasks:
- Set up a DMARC record with a monitoring-only policy of p=none. Ensure the record includes a reporting address to collect aggregate reports from all DMARC-compliant receiving domains. Mail receivers worldwide—such as Google, Microsoft, and Yahoo!—support DMARC and will send DMARC aggregate reports to the domain owners who have configured it.
- Collect and analyze the reports over time.
- Start cataloging email-sending services that are sending email that fails authentication.
- Determine which sending services your organization supports, and get them authenticated.
Note that there are several challenges in implementing DMARC:
- Identifying all sending services and incorporating them into the SPF record without exceeding the
- 10 DNS lookup limit
- Discovering all unknown cloud-sending services
- Updating SPF, DKIM, and DNS
- Mitigating the risks of blocking good email
Pro Tip
DMARC enforcement doesn’t have to be risky or time-consuming.
Valimail Enforce automates sender discovery, simplifies DNS management, and safely guides you to enforcement without breaking email or hitting technical roadblocks.
Start your DMARC journey with Valimail
Implementing DMARC can be a long journey, but it starts with visibility. If you can’t see who’s sending email on your behalf, you can’t stop impersonation, phishing, or domain spoofing. That’s where Valimail comes in.
We’ve helped thousands of organizations, from startups to global enterprises, take control of their email domains and protect their brands from abuse with a thorough DMARC setup. With Valimail Monitor, you’ll gain instant insight into which sources are sending mail on your behalf, which ones are failing authentication, and where you need to take action.
Unlike DIY approaches or tools that leave you guessing, Valimail simplifies everything:
- No manual DNS updates
- No confusing reports
- No technical bottlenecks
You get clear, real-time monitoring that helps you in understanding DMARC and your domain’s exposure and map your path to full DMARC enforcement.
Trust the established #1 leader in DMARC, according to the past twelve G2 reports since Summer 2025:

“Outcomes show that implementing DMARC is one of the highest ROI solutions available. Just make sure to insist on enforcement (activation) and that the process is automated – otherwise, DMARC can be daunting.”

Phil Jackson
System Administrator at AI Solutions
Create a free Valimail account and get immediate visibility into your domain’s DMARC status. It’s the first and most important step to protecting your brand, your customers, and your reputation.
Additional DMARC resources
Explore more on DMARC, email authentication, and phishing prevention with these expert insights. Whether you’re just getting started or fine-tuning your enforcement strategy, these resources will help you secure your domain and stay ahead of emerging threats.
Frequently asked questions about DMARC
As the global leader in DMARC and email authentication, Valimail has helped over 80,000 organizations secure their domains and stop impersonation attacks. In this section, we answer the most common questions and DMARC FAQs so you can protect your email domains with peace of mind.
What does DMARC do?
DMARC protects your domain from being used in phishing and spoofing attacks. It verifies that incoming email messages claiming to come from your domain actually align with the domain’s authentication records (SPF and DKIM). If the message fails those checks, DMARC instructs the inbox providers to monitor, quarantine, or reject it.
DMARC also generates detailed reports that give you visibility into who’s sending on your behalf, helping you identify unauthorized sources and prevent brand impersonation.
How do I add DMARC to my email?
To add DMARC, you need to publish a DMARC record in your domain’s settings. This record tells inbox providers how to handle unauthenticated email from your domain and where to send reports.
To get to full DMARC enforcement, you’ll need to ensure your SPF and DKIM are properly configured, monitor reports, and avoid common pitfalls like the 10 DNS lookup limit.
Can you set up DMARC without DKIM?
Yes, but it’s not recommended. DMARC requires email to pass either DKIM or SPF, and for the domain used in that authentication method to align with the domain in the visible “From” address. Technically, you can configure DMARC with SPF alone, but your domain will be more vulnerable.
SPF breaks with email forwarding, even if it’s legitimate email. DKIM adds cryptographic proof of authenticity, which ensures message integrity and improves deliverability. Using both SPF and DKIM maximizes your protection and ensures better compatibility across different mailbox providers.
Which mailbox providers require DMARC?
Google, Yahoo, Apple, Microsoft, and Comcast all currently require that bulk senders have a DMARC policy of at least none. These requirements could strengthen in the future, and more mailbox providers could require DMARC. This requirement is important for keeping inboxes safer. Learn more here.
Do DMARC records expire?
A DMARC record in a DNS TXT entry will remain active as long as it’s published and present in your DNS settings. Unlike certifications or tokens, it doesn’t have a set expiration date. It’ll be there even if the domain is abandoned.
It only disappears if the domain owner or administration manually removes the record.
What does a DMARC warning mean?
DMARC helps email receivers determine whether a message really comes from the domain it claims to be. When an email fails this check, the receiving server will look at the domain’s DMARC policy for guidance on what to do with the message.
A DMARC warning doesn’t mean the email is malicious. But it does mean that something isn’t configured properly. These alerts can identify potential threats and help you identify where you should tighten your domain’s email security posture.
What is a good DMARC pass rate?
A good DMARC pass rate is typically 95% or higher, but the real goal is full alignment and enforcement.
Your DMARC pass rate reflects the percentage of email messages sent from your domain that pass both authentication (SPF and/or DKIM) and alignment checks. The higher your pass rate, the more legitimate messages are correctly identified and delivered without getting blocked or flagged.
Here’s how to think about pass rates:
| Pass rate | What it means | Action required |
|---|---|---|
| 95-100% | Strong—most of your senders are authenticated and aligned | Review any remaining failures and confirm readiness for enforcement |
| 80–94% | Moderate—some senders may be misconfigured or unauthorized | Identify and fix sources failing alignment |
| Below 80% | Concerning—many messages are unauthenticated or misaligned | Investigate third-party services and review SPF/DKIM setup |
Keep in mind: A “high” pass rate isn’t enough on its own. You also need a strong DMARC policy (p=quarantine or p=reject) to stop malicious messages from being delivered.
Get started for free
with Monitor
Start your path to DMARC enforcement with a panoramic view of the traffic being sent on your behalf.
No trial offers, credit cards, or obligations.
Explore all Valimail
has to offer
Go one step further than visibility…Take action! Reach DMARC enforcement faster. Stay compliant with evolving sender requirements. All while protecting your brand.


